Protect Your Digital Identity and Simplify Secure Access with AuthX
The efficient way to manage identities. Empower your team and protect your data without any fuss.

Identity-based threats are rising.
Stolen Credentials Fuel Attacks.
Discover the Power of Digital Identity Management
Elevate your protection and productivity with IAM solutions. Our advanced features deliver effortless access, robust security, and smart automation, keeping your team secure and productive.
Improve Workforce Productivity with IAM Solutions
AuthX provides a comprehensive approach to workforce identity management, ensuring seamless access, and robust security across all environments.
Flexible Deployment
Tailor solutions to cloud, on-premises, or hybrid setups
Employee Convenience
Seamless access across any device
Authentication Options
Passwordless methods like Badge Tap, Biometrics, Mobile Push
Data Protection
Adaptive and continuous authentication
Administration
Simplified management with intuitive interfaces
Cost Efficiency
Reduce administration and maintenance burdens
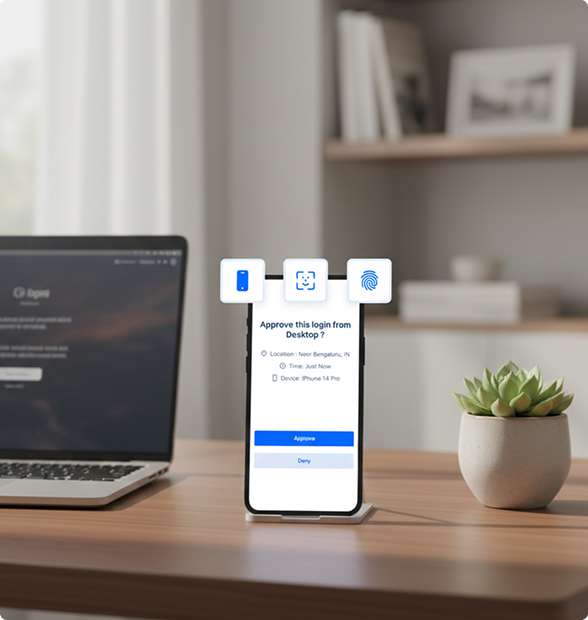
Secure Every Access with Robust Multi-Factor Authentication
AuthX MFA adds extra layers of protection by requiring users to verify their identity through multiple methods; something they know, something they have, and something they are. This drastically reduces the risk of unauthorized access and strengthens enterprise identity security.

Simplify Access with Passwordless Single Sign-On (SSO)
Streamline user access with AuthX SSO. Users log in once and access multiple applications without re-entering credentials, reducing login fatigue and strengthening security by minimizing password management.
Customized Access Solutions to Fit Your Security Needs
AuthX offers diverse access methods to match your security and usability goals:
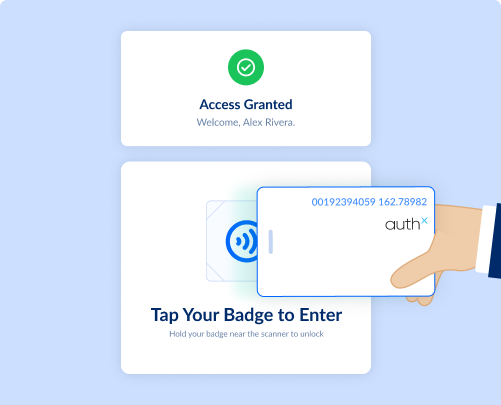
Badge Tap & Go
Access systems instantly with a simple badge tap, no passwords, no friction. Ideal for shared workstations and fast-paced environments where every second matters.
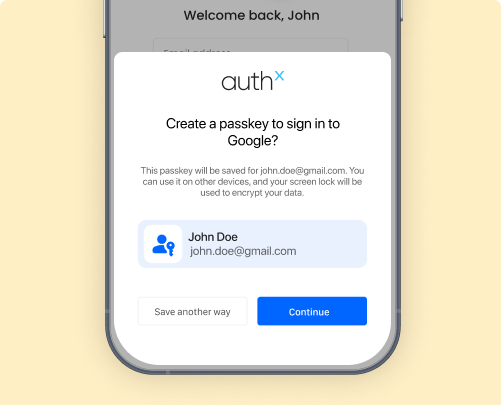
Passkeys
Replace passwords with phishing-resistant digital passkeys designed for modern security threats. Users get seamless access while IT eliminates credential theft risks at the root.
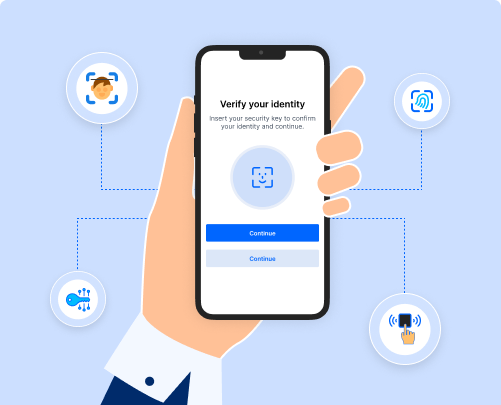
Biometric Authentication
Confirm identity using facial recognition or fingerprint scanning in seconds. It delivers strong, user-friendly security without adding extra steps to logins.
Mobile Push
Approve access requests instantly through a secure push notification on your phone. Perfect for teams that need fast, remote-friendly authentication without compromising control.

Mobile Face Verify
Use your mobile device’s camera for quick, accurate facial verification on demand. Adds an extra layer of assurance when risk levels rise or access needs validation.

OTP Authentication
Secure logins with time-sensitive one-time passcodes sent directly to your device. A simple, reliable option for reinforcing access without complex setup.


