Ensure Security with AuthX for Technology

Security and User Experience in Tech
The technology sector faces numerous challenges securing digital assets while prioritizing user experience. Traditional authentication methods, relying solely on usernames and passwords, fall short in the face of evolving cyber threats, leaving organizations vulnerable to data breaches and identity theft. Additionally, complex authentication procedures frequently lead to user dissatisfaction. AuthX helps organizations overcome these challenges by implementing robust yet user-friendly access solutions.
Enhanced Security with AuthX
Robust Access Controls with MFA
Enhance your security with Multi-Factor Authentication (MFA) , crucial for protecting sensitive data in the technology sector. AuthX MFA offers a seamless experience with options like Biometrics, Mobile Push, Mobile Face Verify, and Badge Tap Access, ensuring robust protection while simplifying access.
Risk Detection and Adaptive MFA
Our Risk Detection and Adaptive MFA provide proactive defense mechanisms. Using advanced algorithms, we detect anomalies in user behavior and adjust authentication requirements based on risk factors. This approach adds an extra layer of security, continuously monitoring and safeguarding your digital assets.
Improved User Experience
Single Sign-On (SSO)
SSO simplifies access to multiple applications, allowing developers to navigate various tools and platforms with single credentials. SSO enhances developer productivity, reduces access friction, and fosters a more fluid workflow by eliminating the need for repetitive logins. It lets them dedicate their time and energy to core tasks and innovation.
Passwordless Authentication
Passwordless Authentication offers a seamless and secure login experience for your workforce. It increases workforce productivity by eliminating the reliance on traditional passwords and introducing innovative authentication methods such as Biometrics, Mobile Push, Face Verify, Mobile Passwordless Authentication, etc.
AuthX's Proactive Defense in Action
01 Security Breach Detected
AuthX's advanced security protocols detect an unauthorized attempt to access a technology company's network, putting critical source code, sensitive data, and assets at risk.


02 Immediate Response
AuthX swiftly activates its adaptive security measures to contain the breach and prevent it from spreading further. AuthX analyzes the breach attempt's characteristics to adapt its defense mechanisms in real time.
03 Adaptive Authentication Ensures Security
AuthX implements adaptive authentication protocols, dynamically adjusting authentication requirements based on the detected risk level. While maintaining stringent security standards.


04 Access Control Implemented
In a decisive move, AuthX revokes access to the compromised device, swiftly halting the breach.
05 Continuous Vigilance
Even after neutralizing the immediate threat, AuthX remains vigilant. AuthX monitors the network for any suspicious activity to ensure ongoing protection against potential breaches.

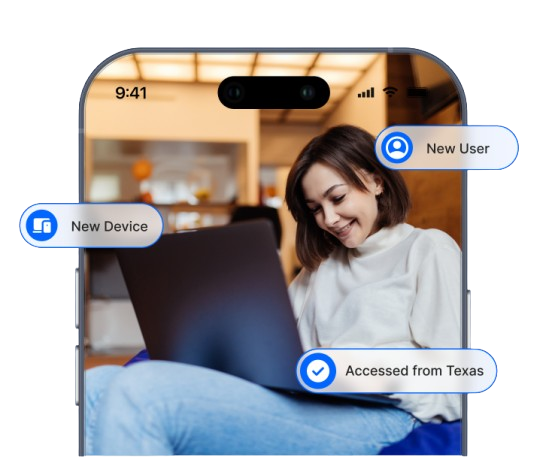
Secure Device Verification
Protect your organization’s assets and data by ensuring the integrity of device access using AuthX’s Trusted Devices approach. By meticulously verifying device identities, our solution protects against potential security threats.
We go beyond simple authentication by assessing the security health of phones, tablets, laptops, and more, ensuring they meet strict security standards before granting access. With advanced device access policies, including geolocation controls and blocking risky devices, we enable you to intensify your digital perimeter against unauthorized access attempts.
Optimize Product Development
Accelerate your product development process with our efficient identity solutions. In the technology industry, identity management is crucial to every product development. Our platform offers a complete solution for user management, authentication, and authorization, relieving your product teams from building these systems independently.
By effortlessly integrating our identity framework, your teams can focus on innovating distinct features that define your products. We expedite your time-to-market and enhance user experiences through simplified identity management, pushing your product development initiatives to new levels.

