Introduction
What Is SMS Authentication?
SMS Authentication is a two-factor authentication (2FA), where users receive a text message on their registered mobile device, that they use to verify while logging into an application or website. An estimated 70-80% of organizations worldwide use SMS authentication today. Hence people assume that this is one of the most secure ways to access their applications since mobile devices are the most carried devices.
However, despite its ease of use, this method faces growing criticism for its security. Many experts argue that using SMS for authentication leaves users vulnerable to various attacks. So, while SMS authentication is convenient, it’s important to consider whether it truly provides the level of security we believe and require in today’s digital world.
How Does SMS Authentication Work?

SMS Authentication Codes - Types of One-time Passwords (OTPs)
Static OTPs are fixed codes for specific transactions but can be risky if intercepted.
In contrast, dynamic OTPs change frequently, with two main types:
1. Time-Based One-Time Password (TOTP)
A temporary code using a static secret key that calculates a time counter based on the current Unix time divided by a predefined timestep. The usual seconds may vary from 30 or 60 up to 120 seconds. If unused within the provided timeframe, the code becomes invalid.
2. Hash-Based One-Time Password (HOTP)
Initiative for Open Authentication (OATH) developed HOTP uses a counter that increments with each OTP request. It requires a secret key known only to the user’s token and the server. The key and counter are processed through a cryptographic hash function, producing a 160-bit hash code typically reduced to a 6- or 8-digit number. This OTP remains valid until the user requests another one.
Pros of SMS Authentication
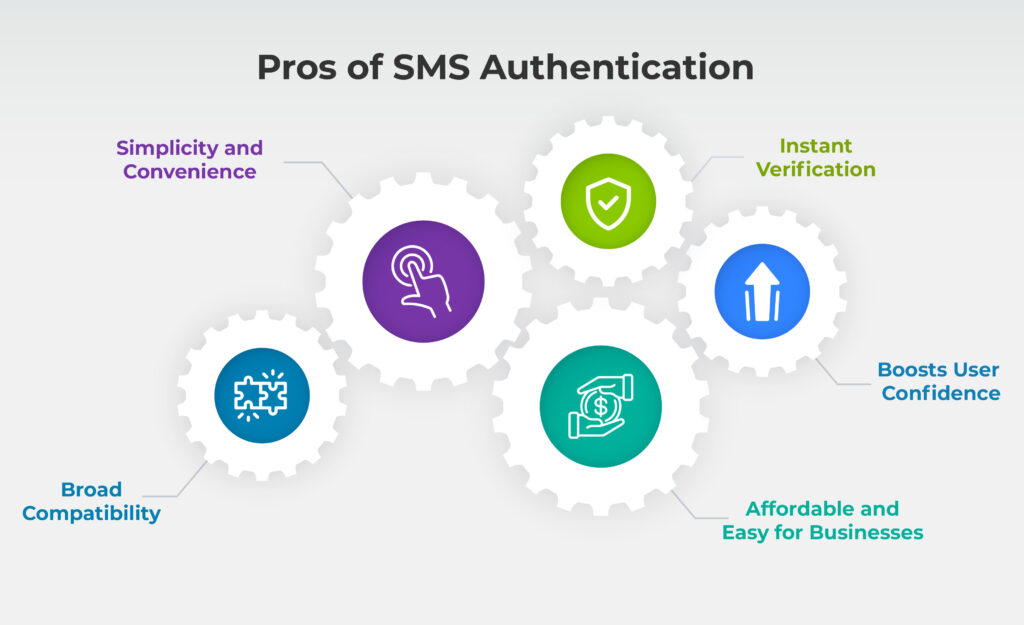
With SMS authentication being widely used by organizations across the world, let us now look at few of the advantages of SMS authentication:
1. Simplicity and Convenience
SMS authentication is extremely easy to use with no complicated setup or extra apps required to be installed. Just enter the code received to your phone, and you’re good to go! This simplicity makes it a great option for both individuals and organizations.
2. Broad Compatibility
Most people have access to SMS, even without a smartphone. Unlike other methods, SMS works on any phone, making it accessible to a much wider audience.
3. Instant Verification
SMS codes are delivered instantly, allowing users to gain access quickly without long waits. This seamless experience keeps things fast and efficient while still ensuring account security.
4. Boosts User Confidence
Having an extra layer of security makes users feel more secure. The fact that they get a unique code sent directly to their phone adds peace of mind, knowing their accounts are protected from unauthorized access.
5. Affordable and Easy for Businesses
For organizations, SMS authentication is straightforward and cost-effective to set up. It doesn’t require much infrastructure and being cost effective makes it a great choice, especially for smaller businesses.
Is SMS authentication fully secure?
Although SMS authentication is widely used for its simplicity, it comes with a significant vulnerability that compromise security. Let us see why SMS authentication a safe choice might not be:
1. Lack of Encryption
SMS messages are not ensured by end-to-end encryption for security, which may lead to interception by attackers and be accessed by service providers. Outdated mobile network protocols are particularly vulnerable.
2. SMS Spoofing
Our mobile phones are mostly connected to the internet, they also become easy targets for phishing attacks. Attackers easily spoof SMS messages to imitate trusted organizations, leading to malicious sites that take sensitive information.
3. SIM Card Swapping
Attackers can pull off SIM card swaps by pretending to be the phone number’s owner. By convincing cellular providers to transfer the number to their own SIM card, and gaining access to all SMS messages, including crucial authentication codes.
4. Cost Considerations
For businesses, relying on SMS authentication can lead to high operational costs, especially when dealing with a large user base that requires frequent verifications.
So, while SMS authentication might seem convenient, it’s important to weigh these risks carefully.
Alternatives to SMS Authentication
Given the vulnerabilities associated with SMS authentication, organizations should explore more secure alternatives that offer enhanced protection against cyber threats.
1. Mobile Authentication Apps
More secure than SMS, these apps display the OTP directly on the user’s screen during login, which is then submitted for verification. This method reduces operational costs and employs end-to-end encryption, making interception by hackers difficult.
2. Email OTP
Like SMS authentication, email OTP uses email to deliver the code. Users verify their email during registration and receive an OTP in their inbox for login. While it avoids reliance on cellular networks, it still requires an internet connection, which can be a vulnerability.
3. Biometric Authentication
Biometric Authentication is the most robust of all. Using fingerprint and facial recognition devices offers quick access without the hassle of passwords. Also providing security that exceeds SMS authentication. As duplicating biometric data is incredibly difficult for attackers, making it a much safer option.
4. FIDO2 (Fast IDentity Online 2)
A public key cryptography protects from phishing attacks. This means your information is secure and protected, promoting passwordless logins. FIDO2 is used commonly as Windows Hello, TouchID, or security keys like Yubikey. The technologies enhance streamline the login process.
Going beyond SMS authentication with AuthX
AuthX offers a powerful combination of authentication methods designed specially to boost security and enhance your overall user experience:
1. Multi-Factor Authentication (MFA)
MFA combines multiple verification techniques to build robust security. The layered approach ensures that accounts are protected in the digital world!
2. Passwordless Authentication
Say goodbye to traditional passwords! This method uses email or SMS links, magic links, and biometric factors, making access easier and more secure.
3. Single Sign-On (SSO)
Using SSO, you can authenticate with an application or website once with RFID, and access multiple applications or websites without requiring logging in separately every time.
4. OAuth and OpenID Connect
The protocols enable third-party services to efficiently authorize user identities. It also ensures your information remains secure while you enjoy seamless access to various services.
5. Biometric Authentication
Using fingerprint or facial recognition, biometrics authenticates the unique traits of everyone, providing high security to access your accounts.
6. Authenticator Apps
Apps like AuthX Authenticator generate time-based or event-based OTP, adding an extra layer of security.
7. Push Notifications
This method sends a login request to your device, allowing you to approve or deny access with a simple tap. It often offers greater security than SMS codes.
8. FIDO2
Using hardware tokens like YubiKey, this method enables passwordless authentication based on public key cryptography, making your logins secure and hassle-free.
9. Email OTP
As the name states, a one-time password is sent to your registered email. While convenient, it’s important to stay aware of potential phishing risks.
10. Hardware Tokens
Physical devices generate OTPs or provide cryptographic authentication, which is used to access enterprise environments for high security.
Conclusion
SMS authentication has become a cornerstone of account security, offering a quick and accessible way to add an extra layer of protection. However, as cybersecurity threats evolve, organizations can benefit from understanding the strengths and limitations of SMS-based security.
At AuthX, we empower organizations to make informed choices about their security. Our suite of passwordless authentication solutions includes Biometrics, Badge Tap, Passkeys allowing you to tailor your defenses to your needs. By enhancing your security approach, you can protect your data with confidence and ensure a safer digital experience for all users.
Together, let’s create a more secure, trusted online environment for everyone.


