Do you ever feel like you’re juggling a dozen keys to get into your digital life? With Single Sign-On (SSO), you can leave those keys behind and unlock everything with a single click. Imagine a master key that opens every door in your online world, eliminating the need to remember many passwords.
According to Gartner, 70% of users report an improved end-user experience as the top benefit of SSO adoption. Additionally, 64% of organizations experience a need for fewer access management tools, and 61% see a reduction in IT support tickets.
This blog will explain what single sign-on (SSO) is, how it works, and why it’s a transformation for managing your digital life. We’ll also discuss the different SSO protocols, their benefits, and challenges and explain how AuthX leverages SSO to make your online experience seamless and secure.
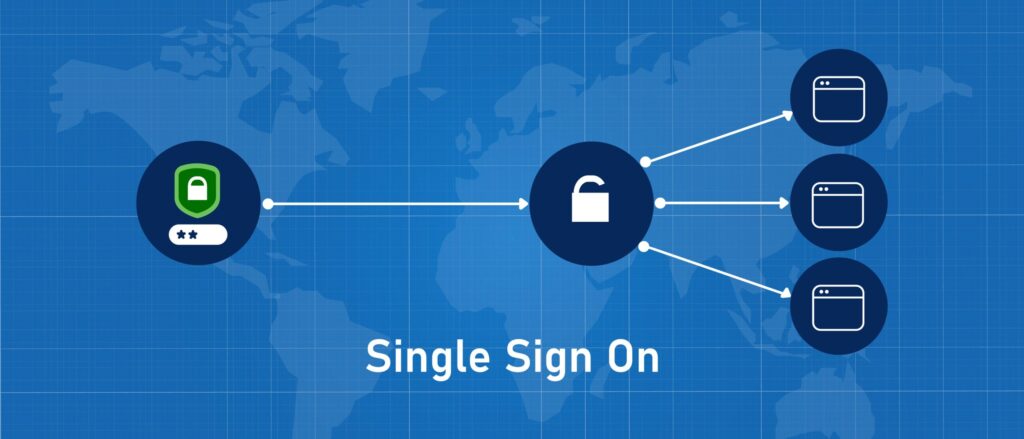
What is Single Sign-On (SSO)?
How does SSO work?
SSO uses a centralized authentication server to manage user credentials and authentication requests. When a user logs into an application, the application communicates with the SSO server to verify the user’s identity. Once authenticated, the SSO server provides an authentication token or ticket that the user can use to access other connected applications without needing to log in again.
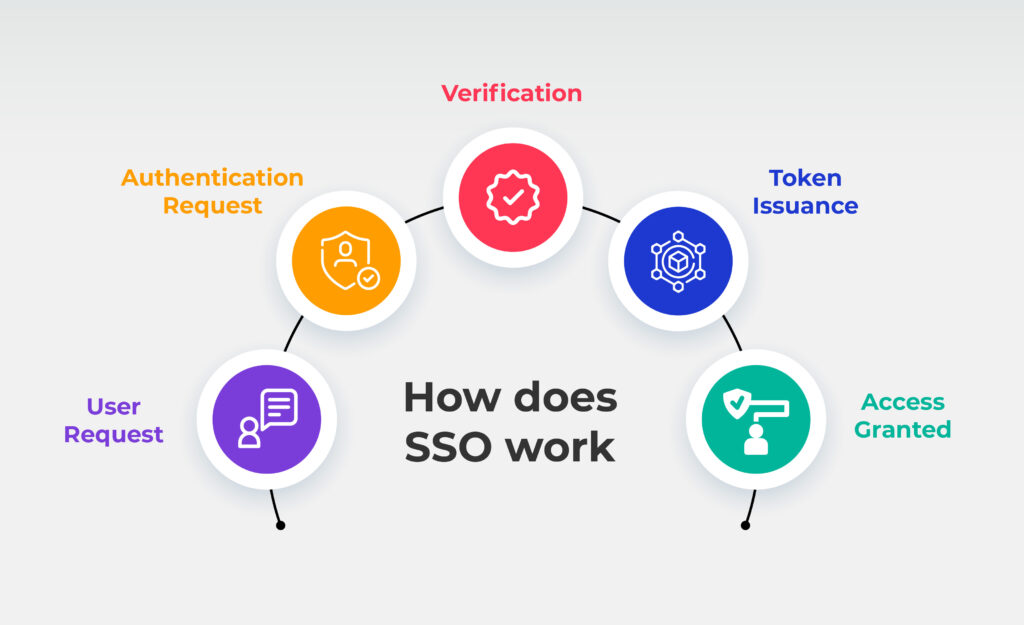
Here’s a simplified flow of how SSO implementation works
- User Request : The user initiates access to an application by entering the URL or opening the app. At this point, they are prompted to authenticate, which triggers the Single Sign-On (SSO) process.
- Authentication Request : The application redirects the user to the SSO server for authentication. This redirection is crucial as it ensures that user credentials are handled by a centralized, secure authentication system rather than the application itself.
- Verification: The SSO server receives the authentication request and verifies the user’s credentials against its database or an external identity provider. This process involves checking the credentials for accuracy and ensuring they meet the necessary security standards.
- Token Issuance: Upon successful verification, the SSO server generates an authentication token or ticket. This token is a secure, time-sensitive credential that proves the user has been authenticated and can be used to gain access to other applications without needing to log in again.
- Access Granted: With the authentication token in hand, the user is granted access to the requested application. Additionally, the token allows seamless access to other connected systems and applications that are part of the SSO network, streamlining the user experience and reducing the need for multiple logins.
Types of SSO Protocols
Several protocols support SSO, each with its own advantages and use cases:
- SAML (Security Assertion Markup Language): SAML is an XML-based protocol primarily used for exchanging authentication and authorization data between parties, especially between an identity provider and a service provider. It is widely used in enterprise environments and supports federated identity management.
- OAuth (Open Authorization): OAuth is a protocol that allows applications to obtain limited access to user accounts on an HTTP service. The latest version, OAuth 2.0, is commonly used for delegated access and is often combined with OpenID Connect for authentication purposes.
- OpenID Connect : Built on top of OAuth 2.0, OpenID Connect adds authentication layers, providing a standardized way to verify user identities. It is commonly used in consumer-facing applications and provides a more streamlined user experience.
What is Social and Enterprise SSO?
Social SSO
Social SSO allows users to log in to various applications using their social media accounts (e.g., Google, Facebook, LinkedIn). This approach leverages existing social identity providers to simplify the login process and can enhance user convenience. However, it may raise concerns about privacy and security as it involves sharing data between platforms.
Enterprise SSO
Enterprise SSO solutions are designed for internal organizational use. They integrate with corporate directories and applications to provide seamless access to various enterprise systems. Enterprise SSO often supports complex scenarios like multi-factor authentication and integration with on-premises and cloud-based systems.
On-Premises vs. Cloud-Based Single Sign-On (SSO)
| Feature | On-Premises SSO | Cloud-based SSO |
| Deployment | Hosted and managed within the organization’s own data center | Hosted and managed by a third-party provider |
| Control | Greater control over infrastructure and customization | Less control, but with easier management |
| Maintenance | Requires in-house IT resources for maintenance and updates | Maintenance and updates handled by the provider |
| Scalability | Limited by internal infrastructure capacity | Easily scalable to accommodate growing needs |
| Integration | May require complex integrations with existing systems | Typically integrates easily with cloud applications |
| Security | Full control over security measures and policies | Security measures are managed by the provider, but often include advanced features like encryption and compliance |
| Cost | High initial investment and ongoing maintenance costs | Pay-as-you-go pricing model, potentially lower upfront costs |
| Accessibility | Access is typically restricted to within the organization’s network | Accessible from anywhere with internet connectivity |
| Disaster Recovery | Requires in-house disaster recovery planning and resources | Provider typically offers built-in disaster recovery and redundancy |
| Compliance | Easier to ensure compliance with internal policies and regulations | Provider handles compliance with industry standards and regulations |
Advantages of SSO
- Improved User Access Experience: Users only need to remember one login, which is like having a magic key to all doors—minus the keychain clutter.
- Increased Productivity: Swift access to multiple applications means less time lost in the login labyrinth and more time for actual work.
- Reduced IT Costs: Fewer passwords reset requests and less administrative overhead mean IT departments can finally breathe a sigh of relief and maybe even take a vacation.
- Enhanced Security: SSO can bring security practices up a notch by incorporating multi-factor authentication, making your digital fortress even more impregnable.
Challenges of Single Sign-On (SSO)
- Single Point of Failure: If the SSO system hits a snag, it’s like locking yourself out of your own house—and all the other houses you’ve unlocked with that key.
- Complex Implementation: Integrating SSO with various applications and systems can be as intricate as assembling a high-tech puzzle.
Single Sign-On (SSO) Security
Ensuring the security of an SSO service involves a few crucial practices:
- Multi-Factor Authentication (MFA): Layering on extra verification is like adding an alarm system to your digital security, just in case.
- Regular Audits: Think of these as routine check-ups for your SSO system to keep vulnerabilities at bay.
- Secure Token Management: Treat your authentication tokens like precious gems—keep them safe and sound.
- Encryption: Use robust encryption to ensure that your authentication data travels safely through cyberspace.

Single Sign-On (SSO) Implementation
Rolling out SSO is a bit like launching a new tech gadget:
- Assessment: Figure out what you need, like deciding on the features of your new device.
- Selection: Pick the right SSO protocol and solution that fits your needs, much like choosing the perfect gadget.
- Integration: Connect the SSO system with your apps and systems—think of it as syncing your new tech with your existing setup.
- Testing: Give it a thorough test drive to make sure everything runs smoothly.
- Deployment: Roll out the SSO solution to users and offer them a crash course, just like showing off a new gadget’s features.
Role of Single Sign-On (SSO) in Identity and Access Management
Single Sign-On (SSO) is the VIP pass of Identity and Access Management (IAM), which enables users to securely access all their applications with one set of credentials. It’s like having a universal keycard that not only simplifies logins but also upgrades your security with consistent policies and Multi-factor authentication (MFA). SSO eliminates the hassle of multiple logins, cuts IT support costs, and ensures compliance by keeping access controls uniform across your entire domain. It’s the ultimate sidekick in your IAM strategy, turning a complex landscape into a well-oiled machine.
Choose AuthX for Single Sign-On (SSO)
When it comes to SSO, AuthX stands out as your trusted SSO provider. With seamless integration options for various protocols, including SAML, OAuth, and OpenID Connect, AuthX provides single sign-on, that is a versatile and scalable approach to managing authentication. Our solutions are tailored to meet the needs of both enterprise and consumer-facing applications, ensuring that users have a smooth and secure login experience.
Conclusion
Single Sign-On (SSO) is a powerful tool that simplifies user authentication, enhances security, and improves productivity. By understanding how single sign-on login works, the different types of protocols, and the benefits and challenges associated with SSO, organizations can make informed decisions about their authentication strategies. AuthX is committed to providing passwordless SSO solutions that streamline access management and support the evolving needs of modern organizations. Experience the potential of AuthX and see how our single sign-on capabilities can transform your digital ecosystem into a more secure and efficient environment. Reach out to us today to discover how our SSO service makes it possible for your team to work seamlessly with one login.


