Navigating the path to a more secure digital future involves mastering the management of identities and access. No matter where the company’s resources work, they access sensitive business data at considerable risk owing to increasing cybersecurity threats. Identity and Access Management (IAM) ensures data security and integrity. IAM is an extensive approach to controlling access and managing user identities. It also includes working on their access to certain apps, systems, and data within an organization. In this blog, we will explore Identity and Access Management (IAM), its significance in cybersecurity, and why it should be important to your organization.
What is Identity and Access Management (IAM)?
According to Gartner, Identity and Access Management (IAM) is essential to security and operations. It involves various technologies and procedures to ensure that the right person can access the right resources at the right time. IAM protects an enterprise against unauthorized access and fraud. IAM primarily can be explained by answering these questions:
Who is the user? It determines the identity of an individual seeking access to resources.
What can the user do? IAM defines the level of access rights given to a user based on their roles and responsibilities in the organization.
How does the user do it? Identity and Access Management Solution monitors user activity and provides a thorough audit report for security.
Why is IAM important?
Imagine a company with multiple departments requiring access to different systems and data. Without Identity Access Management, managing user access becomes a nightmare. Employees may have access to sensitive information they don’t need, increasing the risk of data breaches. With IAM, the company can centrally manage user access, ensuring that employees only have access to the resources necessary for their roles, i.e., privileged access. This strengthens security and streamlines operations by automating user provisioning and access requests. As a result, the company can maintain compliance with industry regulations, minimize security risks, and optimize productivity, showcasing the importance of an effective IAM platform in modern business operations.
How Does IAM Work?
IAM consists of several components:
1. Authentication
User identities are verified through several types of authentications like passwords, Multi-Factor Authentication (MFA), biometrics, and smartcards. Secure authentication is crucial to ensure that only authorized users access critical information.
2. Authorization
Authorization is the guardian of IAM that determines which resources a user can access post-authentication. Typically, authorization policies are set up based on the user’s roles, permissions, and attributes. For example, an HR manager can access employee records securely, and a finance authority can access only financial data.
3. User Management
IAM systems offer administrator tools for managing a user’s identity, role, and permission. It includes creating, modifying, or deleting user accounts. IAM executes access controls and monitors user activities. Automated provisioning and de-provisioning user accounts are essential for ensuring security and efficiency.
4. Single Sign-On (SSO)
IAM utilizes SSO technology to provide a passwordless authentication experience that contributes to user convenience by enabling access to multiple applications with a single set of credentials. It enhances user experience and streamlines workflows.
5. Auditing and Reporting
IAM systems maintain comprehensive records of user activity. These logs are crucial for auditing, allowing organizations to track who did what and when. These are also helpful in the detection of suspected or unauthorized conduct.
Key Benefits of IAM
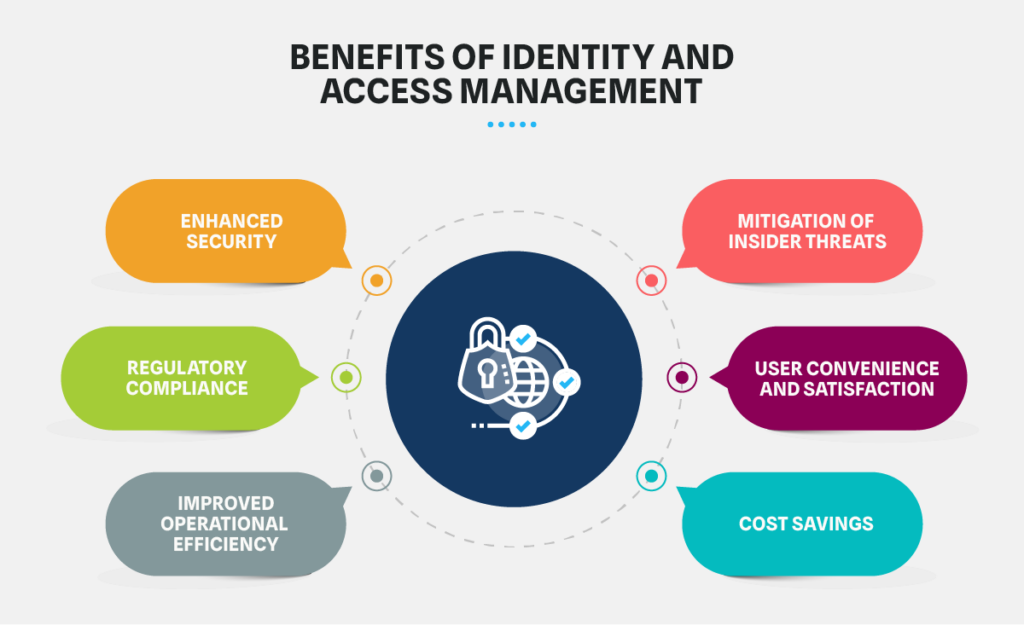
1. Enhanced Security:
IAM strengthens an organization’s security posture by implementing strict access controls that ensure only authorized individuals can access critical information. This preventative approach significantly reduces the risk of data breaches and insider threats.
2. Navigating Regulatory Compliance:
Many industries and organizations are regulated by standards that demand rigorous control over user access to sensitive data. Identity and Access Management helps fulfill and demonstrate compliance with requirements like GDPR, HIPAA, and PCI DSS.
3. Improved Operational Efficiency:
IAM streamlines user provisioning and de-provisioning for centralized management within an organization. It lowers administrative expenses and eliminates the likelihood of human error. This operational efficiency leads to higher productivity.
4. Cost Savings
Identity and Access Management reduces the probability of security events, leading to financial savings as it avoids breach-related costs. This proactive approach safeguards assets and prevents costly repercussions.
5. User Convenience and Satisfaction
By allowing quick access to resources and self-service password management options, IAM systems aim to boost productivity and user satisfaction.
6. Mitigation of Insider Threats
By monitoring user activity, identifying unusual behavior, and restricting access based on roles and responsibilities, IAM helps detect and prevent insider threats.
Exploring the World of Cloud IAM
With the rapid expansion of cloud computing, IAM has naturally extended its scope to embrace Cloud Identity and Access Management. Cloud Identity Management incorporates the core concepts of IAM while adapting them to secure cloud-based resources, services, and applications. It delivers the same benefits as traditional IAM but can be tailored to the ever-changing world of cloud operations. Cloud IAM incorporates Role-Based Access Control (RBAC), Multi-Factor Authentication (MFA), Centralized User Identity Management and Compliance Management.
Conclusion
Organizations must recognize Identity and Access Management Solutions as critical to modern cybersecurity and business efficiency. IAM enables organizations to adhere to regulations, protect sensitive data, and boost efficiency. Investing in reliable IAM systems today allows you to deal with user identities responsibly, manage access, and track user activity. As the digital world evolves, IAM’s importance persists in ensuring an organization’s strength and security.
Ready to secure your digital assets? Discover how AuthX can elevate your IAM game! Explore AuthX, a modern Identity and Access Management platform offering top-tier security, convenience, and operational efficiency. Contact us today to discover how our IAM services can help you protect your digital assets and improve your cybersecurity posture.


