We often hear security leaders talk about their struggles with achieving Zero Trust in hybrid work environments. The conversation always circles back to one point: DEVICES. If you can’t trust the devices connecting to your network, how can you trust the individuals that access company resources?
Device trust is no longer optional; it is an essential component of any effective security approach. With the development of BYOD (Bring Your Own Device) policies and an increase in remote work models, IT leaders are asking: How can I validate every device without disrupting productivity?
Let’s explore how device trust works, how it complies with Zero Trust regulations, and why it is crucial for an organization’s security.
What is Device Trust?
Simply put, device trust makes sure that your network is only accessible by devices that meet certain security requirements. It is crucial to verify the security status of any devices on the premises, whether they are an IoT device, a partner’s mobile phone, or an employee’s laptop.
Device trust, according to IT managers, is a “security hygiene” practice that is often ignored until a breach happens. It is the foundation upon which the rest of the security stack is built. Without device trust, securing your network is like locking the doors but leaving the windows wide open.
How Device Trust Works?
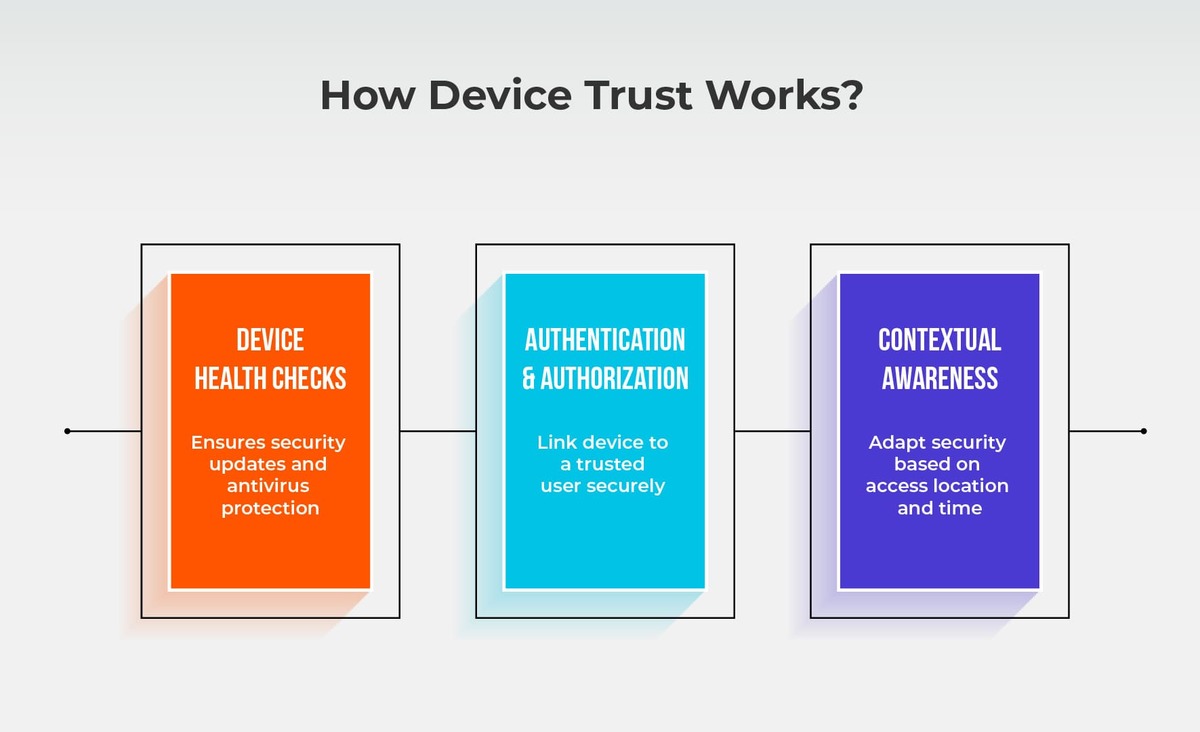
The key to device trust lies in evaluating the device identity alongside its behavior. When we talk about device trust, we’re discussing a few key steps:
Device Health Checks
Device health checks involve ensuring that the device is up to date on security patches, anti-virus software, and endpoint protection. Only devices that pass these checks get access.
Authentication and Authorization
The next step is ensuring that the device is associated with a known, authorized user identity. This involves device identification, which ensures that every device accessing the network is properly recognized and validated. By tying this to authentication methods like passkeys, biometrics, or secure login apps, organizations add another layer of trust before granting access to corporate resources.
Contextual Awareness
Beyond the device itself, context is key. Is the device trying to access sensitive data from an unfamiliar location? Is it outside of typical working hours? These conditions help enforce a more adaptive security approach.
The key to device trust lies in evaluating the device identity alongside its behavior. Understanding what the device is doing and where it is attempting to go ensures a more comprehensive and context-aware approach to security.
How Device Trust Aligns with Zero Trust Principles
Zero Trust security has become the gold standard in cybersecurity. The core principle of Zero Trust is simple: Never trust, always verify. But here’s the catch — Zero Trust is not achievable without device trust. Let us explain why.
A common topic continues to pop up among cybersecurity experts is that the effectiveness of a Zero Trust architecture is determined by the devices it protects. This becomes especially significant in environments with BYOD policies, where a diverse range of personal devices are used to access corporate networks. It isn’t just about authenticating individuals; it’s also about verifying the devices they use to access your network. Without device identification and verification, a user with legitimate credentials could still be gaining access to your network through an untrusted device, which could put them at risk.
Zero Trust demands ongoing authentication, and device trust is critical here. Access is refused if the device is unreliable, even if the user’s login credentials are valid.
Did you know?
According to a report from Cybersecurity Insiders, Data loss is the #1 security concern surrounding BYOD.
The Role of IAM Solutions in Device Trust
Identity and access management (IAM) solutions are critical to device access control because they manage who and what can access your network. Effective device access control ensures that only secure and compliant devices can interact with corporate resources, aligning with modern security protocols. IAM systems work best, when paired with device trust protocols and modern authentication techniques like passwordless login and Multi-Factor Authentication (MFA).
For instance, when a user tries to access your network, IAM solutions not only authenticate their identity through MFA or passwordless methods, but also verify whether the device meets specific security standards. If a device doesn’t meet these standards, IAM solutions can block access to sensitive resources or trigger additional security checks.
By integrating with endpoint detection and response (EDR) systems, IAM solutions can enforce device trust and verify both the user’s identity and the device identity. This ensures that only compliant devices and authenticated users interact with corporate resources, forming a robust multi-layered security approach.
Challenges of Device Trust
Despite being an essential part of a Zero Trust security system, device trust has its own set of challenges in terms of implementation and maintenance. Some of the key hurdles are:
- Device Diversity: From BYOD gadgets like smartphones and laptops to Internet of Things devices, businesses usually find it difficult to control and verify the variety of devices connecting to their networks. Effective device identification processes are necessary to catalog and secure each device type. It could be challenging and time-consuming to ensure that all devices adhere to security standards.
- User Behavior: User behavior can compromise the integrity of a device, even if it is trustworthy. Connecting to unsecured networks or downloading malicious malware are two examples of this. Comprehensive security requires both monitoring user activity and ensuring device confidence.
- Legacy Systems: Older systems or devices that do not support modern security protocols can be hard to integrate into a device access control framework. Organizations may struggle to establish trust with legacy endpoints without costly upgrades or workarounds.
- Real-Time Verification: One of the biggest challenges is continuously confirming in real-time how reliable devices are. A strong and scalable solution is needed to keep track of current device health statuses and prevent unauthorized access during device compromise or user mobility.
Key Benefits of Device Trust
- Reduced Risk of Data Breaches: Organizations can prevent malware or compromised devices from getting access to sensitive data by confirming device security before providing permission.
- Enhanced Endpoint Protection: Device trust ensures that devices connecting to the network are adequately protected, reducing the attack surface and strengthening overall endpoint security.
- Streamlined User Access: When devices are authenticated automatically, users can get the tools they require without having to go through many steps. Device trust offers frictionless, secure access to company resources, increasing productivity.
- Simplified Compliance: For industries that require strict data protection regulations, device trust helps organizations maintain compliance by ensuring that only authorized, secure devices can access sensitive information.
The Future of Device Trust
Device trust will become even more essential as more organizations implement remote and hybrid work models. As mobile device management, IoT, and personal devices proliferate, organizations must reconsider traditional security practices.
The development of AI and machine learning will also play a crucial role in enhancing device trust since it will allow for automated, real-time decisions on device access. Furthermore, as regulatory frameworks evolve, device trust will become an increasingly important factor in achieving and maintaining the industry standards.
Building a Stronger Security Posture with Device Trust
Device security is now an essential part of your organization’s entire security plan, not just an IT task. Efficient device management strengthens Zero Trust frameworks, integrates easily with IAM systems, and shields your company from potential risks. Making sure that only trustworthy devices have access to your network is the first step towards creating a safe and effective work environment.
Organizations can ensure that only secure, authorized devices can access their networks by adopting device trust, which serves as a solid foundation for an all-encompassing security strategy. Ready to take the next step? Let’s discuss how AuthX can help secure your devices and build a Zero Trust environment tailored to your needs.


