In our fast-paced digital world, protecting sensitive information is more critical than ever, particularly for law enforcement organizations. As cyber-attacks increase, achieving Criminal Justice Information Services (CJIS) compliance is a regulatory requirement and a critical defense strategy. This blog explores how AuthX’s advanced multi-factor authentication (MFA) solutions help you achieve CJIS compliance and enhance operational efficiency for law enforcement agencies.
What is CJIS Compliance? What does CJIS stand for?
Criminal Justice Information Services (CJIS) compliance refers to adherence to the security standards – policies and procedures the FBI’s CJIS Division sets. It encompasses a comprehensive framework of policies, procedures, and technical precautions to protect criminal justice information (CJI) shared among authorized entities.
What is CJIS Security Policy?
CJIS compliance refers to adherence to the security standards – policies and procedures the FBI’s CJIS Division sets. It encompasses a comprehensive framework of policies, procedures, and technical precautions to protect criminal justice information (CJI) shared among authorized entities.
- something you know (e.g., a password)
- something you have (e.g., a token)
- something you are (e.g., a biometric factor)
This multi-layered approach significantly reduces the risk of unauthorized access and enhances overall data security.
Ensuring CJIS compliance is crucial for smooth access to CJI and to maintain the confidentiality, integrity, and availability of sensitive data, including criminal histories, fingerprints, and other investigative information. Non-compliance can lead to breaches, data theft, and compromise of law enforcement operations, posing significant risks to public safety and trust.
AuthX's Comprehensive MFA Solutions to Help You Be CJIS Compliant
- RFID/NFC Badge Tap: Quick and secure authentication using RFID/NFC Badges.
- Mobile Face-Verify: Reliable identity verification through facial recognition technology on mobile devices.
- Fingerprint Biometric: High-accuracy fingerprint scanning for secure access.
- Mobile Push: Convenient authentication through push notifications on mobile devices.
- Remote Unlock: Securely lock/unlock systems from a remote location.
- SMS/Call/Email OTP: Additional layers of authentication are available through OTP on SMS/Email or phone calls.
13 Compliance Requirements for Criminal Justice Information Services (CJIS)
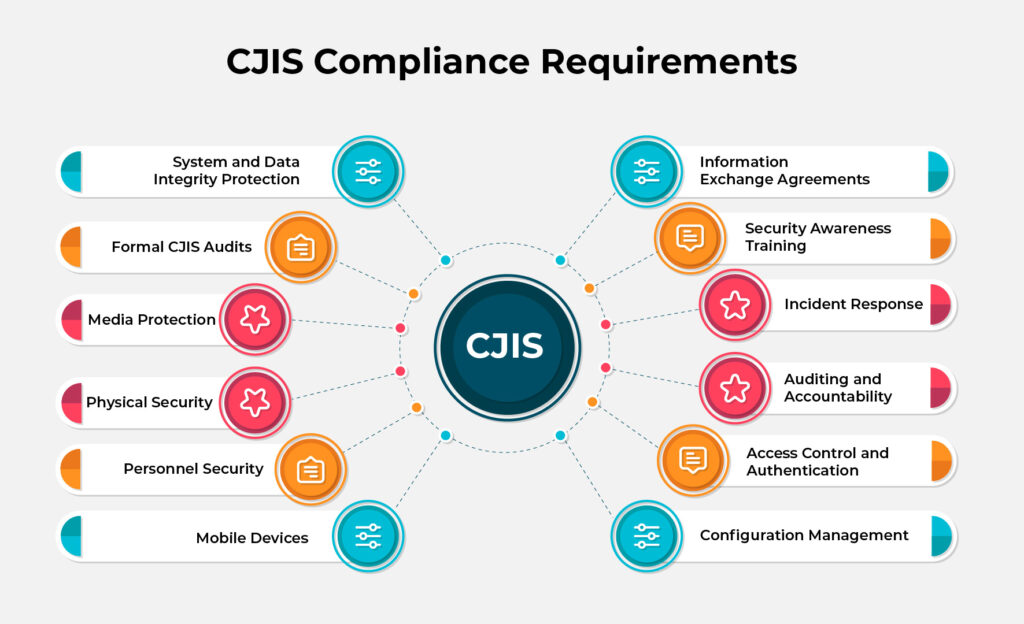
- Information Exchange Agreements:Organizations handling criminal justice information must establish clear protocols for exchanging data and ensure agreements cover audits, logging, security measures, and timely responses.
- Security Awareness Training:All personnel accessing criminal justice data must undergo routine security awareness training designed for their specific roles and responsibilities, reinforcing the importance of data protection.
- Incident Response:Robust procedures for detecting, analyzing, and responding to security incidents must be in place, with mandatory reporting to relevant authorities, including the Justice Department.
- Auditing and Accountability:Regular audits should cover a range of critical events, including login attempts, permissions changes, and access to sensitive files, ensuring accountability and compliance.
- Access Control:Access to criminal justice information must be strictly controlled, with user privileges monitored and tracked on a need-to-know basis to minimize risks.
- Identification and Authentication:To access CJIS data securely, each authorized user must have a unique identifier and employ standard authentication methods like MFA.
- Configuration Management:Whether planned or unplanned, information system changes must be meticulously documented and safeguarded against unauthorized access.
- Media Protection:Policies should outline secure storage, transportation, and destruction of digital and physical media containing sensitive information, ensuring data integrity and confidentiality.
- Physical Security:Access to physical media and storage areas must be restricted and monitored closely to prevent unauthorized access or tampering.
Systems and Communications Protection and Information - Integrity:Applications and systems must enforce stringent security measures to protect data and network integrity and define clear pathways for information exchange.
- Formal CJIS Audits:Organizations should be prepared for formal CJIS audits by the FBI and other agencies to verify adherence to CJIS compliance standards.
- Personnel Security:Stringent security screening processes must be applied to all personnel accessing unencrypted CJIS data, ensuring trustworthiness throughout their employment lifecycle.
- Mobile Devices:Policies should address the secure use of mobile devices for accessing CJIS data and implement wireless security protocols and device management practices to mitigate risks effectively.

Benefits of AuthX for Law Enforcement Industry
- Enhanced Security: Using multiple MFA modalities, AuthX significantly reduces the risk of unauthorized access and data breaches. Our solutions ensure that only authorized personnel can access sensitive criminal justice information, helping you meet CJIS security requirements.
- Improved User Experience: At AuthX, we prioritize user experience. Our passwordless MFA modalities are designed to provide secure access without disrupting critical law enforcement tasks. This balance between security and convenience is essential for efficient operations.
- Cost-Effectiveness: AuthX offers flexible, budget-friendly options catering to organizational needs and funding limits. Our solutions are designed to be cost-effective while ensuring robust security.
- Streamlined Deployment: AuthX integrates seamlessly with existing identity stacks or can serve as an end-to-end identity provider. Our solutions are designed for easy deployment, minimizing disruption to your organization’s operations.
Conclusion
At its core, CJIS compliance isn’t only about meeting regulatory standards—it’s about protecting the justice system’s integrity and the individuals it serves. It’s about ensuring that every interaction, every piece of information exchanged, upholds the principles of accountability and justice.
By providing seamless, user-friendly MFA solutions, AuthX enhances security and empowers Law Enforcement personnel to perform their duties confidently and efficiently. It’s about giving them the tools to focus on what truly matters: protecting and serving their communities.
Connect with our experts today to learn how we can help you be CJIS-compliant.


