Authentication protocols play a vital role when we talk about securing access to applications, services, and data. They are the invisible gatekeepers that ensure only the right people can access sensitive resources. In the world of identity and access management (IAM), two key protocols dominate: SAML (Security Assertion Markup Language) and OIDC (OpenID Connect). But when it comes to SAML vs OIDC, which one fits your needs best?
In this blog post, let’s explore the fundamentals of SAML authentication and OIDC authentication, delve into their workflows and features, compare their security benefits, and examine how each protocol fits into today’s authentication landscape. We’ll even share insights on when to choose each based on your specific needs.
Introduction to SAML and OIDC
Authentication methods are like a house’s foundations; without a solid one, everything collapses. In today’s digital environment, when businesses are more cloud-centric and mobile, selecting the correct protocol is critical for security and user experience.
While SAML protocol has long been the gold standard in enterprise applications, OIDC authentication has emerged as a modern alternative, especially in cloud-based and API-driven scenarios. Both systems provide the same purpose—secure user authentication—but approach it differently. The question isn’t always “Which is better?” but rather “Which one meets your needs?”
What Are SAML and OIDC?
Before we dive into how they work and when to use them, let’s define each protocol.
SAML
What is SAML authentication? SAML is an XML-based authentication protocol intended primarily for enterprise Single Sign-On (SSO). If your firm continues to use legacy systems or connects with services that require strong identity assertions, SAML could be the answer you’ve been utilizing for years.
It enables secure XML-based assertions between Identity Providers (IdPs) and Service Providers. These assertions verify a user’s identification and give access to resources without the user having to log in several times, supporting SSO using SAML workflows.
OIDC
What is OIDC? OIDC, or OpenID Connect, is an OAuth 2.0 protocol that utilizes JSON Web Tokens. While OAuth requires authorization, OIDC adds an identity layer, making it perfect for user authentication. It’s lightweight, easy to set up, and perfect for modern web and mobile projects that need to scale quickly.
For example, many social logins you see nowadays, such as “Login with Google” or “Log in with Facebook,” are driven by OIDC authentication. Its simplicity and developer friendliness have made it the preferred protocol for modern software environments.
How Do They Work?
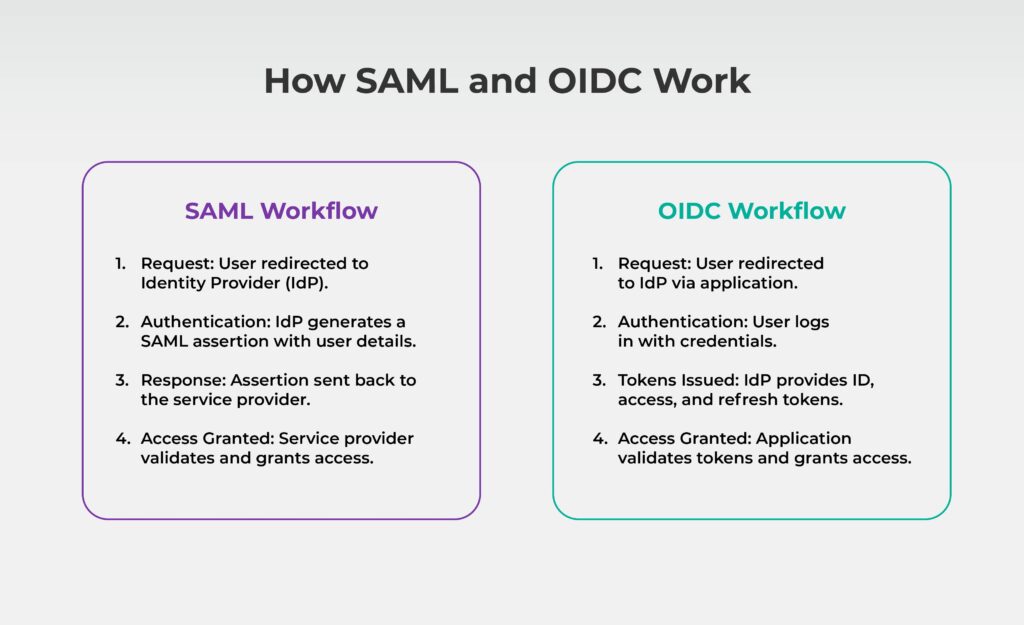
Let’s examine how these protocols function in practice to understand their differences.
SAML Workflow
The objective of SAML is enterprise-level authentication. The following actions take place during a SAML flow:
- Request: To authenticate, the user is sent to an Identity Provider (IdP).
- Authentication: The IdP generates a SAML assertion and authenticates the user. This assertion contains information about the user’s identity and any attributes the service provider needs.
- Response: The IdP sends the assertion back to the service provider.
- Granting Access: The service provider validates the assertion and grants access to the user.
This SAML protocol ensures a robust, secure SAML authentication flow but can become quite complex in modern, distributed environments.
OIDC Workflow
By emphasizing token-based communication, OIDC authentication simplifies the process. This is how it operates:
- Request: The user is redirected to the IdP after requesting access to an application (the client).
- Authentication: The user authenticates with a username/password or other factors.
- Tokens: The IdP issues an ID token (and, optionally, access and refresh tokens), which the client validates.
- Granting Access: The application validates the token and grants access to the user.
OIDC’s workflow is generally faster and more straightforward, particularly in cloud environments where APIs play a central role.
Key Features of SAML and OIDC
Here’s a quick comparison of their key features:
SAML:
- Robust, secure, and well-suited for enterprise-level applications.
- It uses XML for messages, which can be complex to implement.
- Strong support for SSO using SAML.
- Ideal for older, on-premises systems.
OIDC:
- Lightweight and flexible, optimized for modern web and mobile apps.
- It uses JWTs, which are easier to manage and more compact.
- Designed to support API-based applications.
- Strong focus on user experience and developer ease of use.
Developers often say, “We switched to OIDC because it’s much easier to integrate with our cloud services.” That’s the power of OIDC; its simplicity is perfect for today’s fast-moving tech stacks.
Use Cases
When to Use OIDC?
- OIDC is the clear choice when:
- You’re building modern applications or APIs.
- You need to support mobile applications.
- You want to implement social login or third-party authentication (e.g., Google or Facebook).
- You’re working in a cloud-native environment.
When to Use SAML?
SAML is the better option when:
- You need to support enterprise applications that are not cloud-based.
- You’re dealing with legacy systems or cross-organization collaboration.
- Your organization has an established SAML-based IdP and workflows requiring SAML flow.
Security Comparisons
Security is a top priority when selecting an authentication protocol. SAML and OIDC offer strong security features, but approach risks differently.
Phishing Prevention
- SAML: Encrypts the identity information sent during authentication to prevent phishing.
- OIDC: By switching from password-based authentication to more secure token-based solutions, OIDC lowers the danger of phishing attacks.
Brute Force Prevention
By using Multi-Factor Authentication (MFA) and Single Sign-On (SSO), both protocols aid in thwarting brute force assaults. The risk of unauthorized access is reduced by requiring extra verification stages.
Privacy Protection
- SAML: Offers robust data deletion features that are necessary for some sectors to comply.
- OIDC: Provides customers additional control over their privacy by providing granular control over the data shared between the Identity Provider and Service Provider.
Choosing the Right Protocol
So, how do you decide which protocol to use? The choice between SAML and OIDC depends on the nature of your environment.
- OIDC is recommended for modern apps and APIs that need to scale quickly. Applications that must interface with other third-party services and businesses that value the developer experience will benefit from it.
- Enterprise settings, particularly legacy systems that depend on on-premises identity providers, are better suited for SAML.
We often recommend a hybrid approach for organizations that need to support old and new systems.
Benefits of AuthX for SAML and OIDC Integration
AuthX is designed to seamlessly integrate with SAML and OIDC, offering flexibility for any infrastructure. With passwordless and multi-factor authentication support, AuthX provides a secure, user-friendly experience for any environment.
AuthX is compatible with both modern and legacy systems, allowing you to enjoy the benefits of both protocols while minimizing implementation complexity
Final Takeaway
Choosing between SAML vs OIDC is less about one being “better” than the other and more about understanding your needs. For modern cloud applications, OIDC authentication is often the best choice. However, SAML authentication is still the go-to for large enterprises with complex legacy systems.
At AuthX, we offer solutions that support SAML protocol and OpenID Connect, ensuring your authentication is secure, flexible, and seamless.
FAQs
Can OIDC replace SAML entirely?
While OIDC is more suited for modern applications, SAML still holds strong in enterprise environments with legacy systems.
Is SAML becoming obsolete?
No, SAML continues to be widely used, particularly in established organizations. However, OIDC is becoming the preferred choice for new applications.


