Security leaders must always strike a balance between scalability, usability, and security. In 2023, 56% of employed adults worked from home at least some of the time, with 22% working entirely from home and 34% on a hybrid basis. Access control is more important than ever because of distributed teams, hybrid workforces, and rising Zero Trust standards. We are managing a digital environment where identity, location, and device all influence who has access to what. The stakes are high: every misstep in access control becomes a vulnerability waiting to be exploited.
There are several models out there – RBAC, ABAC, PBAC, ACL, DAC and we’ve seen a rise in hybrid approaches too. But the real question is:
Which access control model is right for your organization? Let’s break it down.
What Is Access Control?
Access control is the system that defines who can access what and when. It’s the cornerstone of digital access security, ensuring only the right people reach sensitive resources.
Traditional methods used static rules. But with cloud environments and hybrid work, modern access control needs to be context-aware—factoring in a user’s role, location, time, and device to create secure, flexible frameworks.
What Is RBAC (Role-Based Access Control)?
The Role-Based Access Control definition is simple: access is granted based on a user’s pre-defined role within an organization, not their individual identity. Think: Manager, HR, Developer, Intern. Every role has a set of permissions, and users inherit access when assigned to a role.
How does it work in real life?
A new marketing intern joins the team. They’re assigned the “Marketing Intern” role, which allows them to view campaign dashboards but not edit budgets.
Types of RBAC
- Flat RBAC: All roles are on the same level, offering simplicity but lacking nuanced access control.
- Hierarchical RBAC: Roles inherit permissions from higher-level roles, streamlining management while allowing more refined control.
- Constrained RBAC: Limits access based on separation of duties, reducing the risk of conflicts of interest and unauthorized actions.
- Symmetric RBAC: Ensures users can only perform actions within their designated role boundaries, balancing security with ease of use.
RBAC Benefits
- Easy to implement and scale in small to mid-size organizations: RBAC offers a straightforward approach, making it ideal for companies with clear roles and limited complexity.
- Role reuse makes onboarding fast: By assigning access based on predefined roles, onboarding new employees becomes quicker and more efficient.
- Aligns well with compliance frameworks like HIPAA or SOX: RBAC’s structure makes it easier to audit and ensures compliance with stringent regulations.
RBAC Challenges:
To scale RBAC access control, organizations must plan for role hierarchy, periodic audits, and privilege cleanup.
- Role explosion: As organizations grow, the number of roles can become overwhelming, leading to management challenges.
- Privilege creep: Users often retain access to systems they no longer need, potentially creating security risks.
- Not flexible enough for modern, fluid work environments: RBAC struggles to adapt to dynamic teams, remote workers, and constantly changing business needs.
What Is ABAC (Attribute-Based Access Control)?
ABAC uses attributes to make access decisions about the user, the resource, the environment, and the action.
Here’s an example of ABAC rule:
“Allow access if the user is in HR, accessing from a corporate device, during business hours.”
ABAC policies are like IF statements. If all the attributes match, access is granted.
ABAC Components:
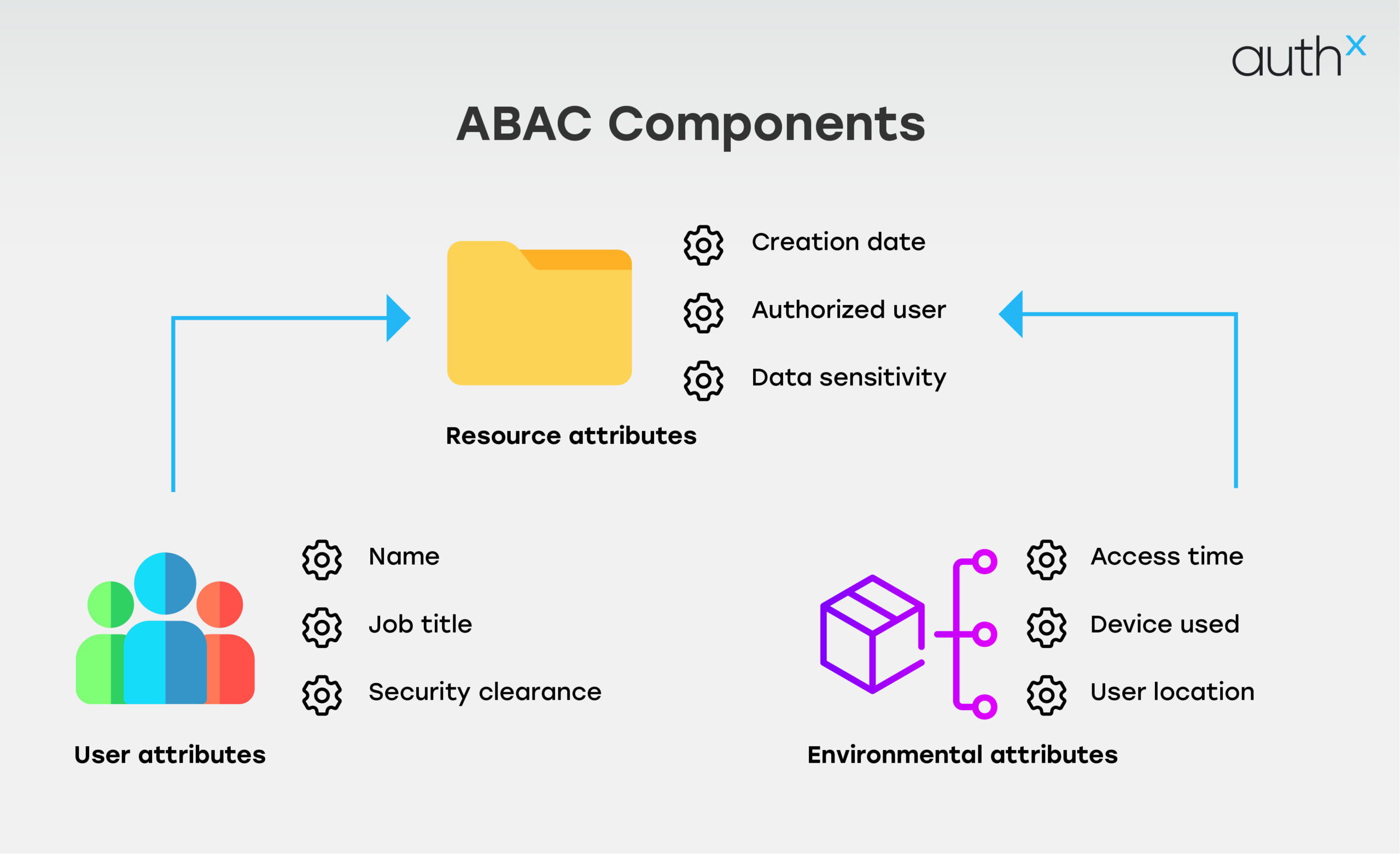
- User attributes: These include factors like job title and clearance level, which determine what a user can access based on their identity.
- Resource attributes: This involves considering the sensitivity or type of resource being accessed to ensure that only authorized users can interact with certain data or systems.
- Environment: Context matters—factors like time of day, device used, or user location can influence whether access is granted.
- Action: The specific action a user wants to perform (e.g., read, write, delete) is factored into the access decision.
ABAC Benefits:
- More dynamic and granular than RBAC: ABAC provides more precise control by considering a variety of variables, enabling better customization.
- Supports distributed, hybrid, and remote teams: ABAC adjusts to modern work settings where users may access systems from various devices and locations.
- Easier to modify access for new or changing users: As roles or circumstances change, it’s easier to modify user permissions because access decisions are based on attributes.
ABAC Challenges:
- More complex to configure and govern: Setting up ABAC requires managing a wide range of attributes, which can be complicated for IT teams.
- Attribute sprawl requires tight oversight: As the number of attributes grows, ensuring consistency and accuracy becomes a key challenge.
- Steeper learning curve for IT teams: The increased complexity of ABAC can make it harder for IT teams to get up to speed, requiring additional training and management.
So, what is ABAC in simple terms? It’s a dynamic, fine-grained approach that adapts to the realities of today’s workplace.
RBAC vs. ABAC
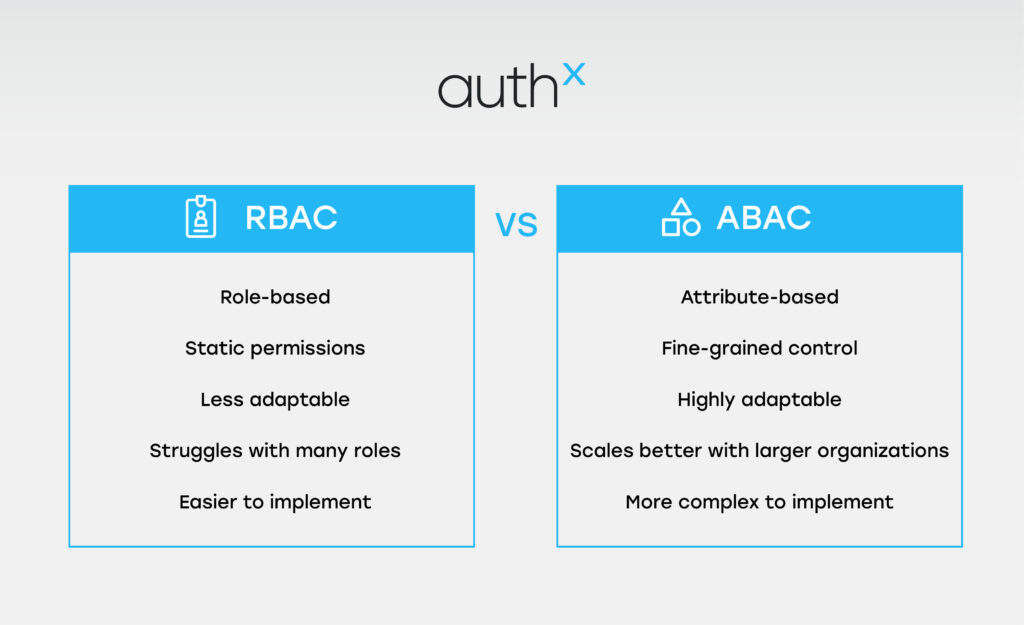
| Feature | RBAC | ABAC |
|---|---|---|
| Method | Based on roles | Based on multiple attributes |
| Flexibility | Low | High |
| Setup | Simple | Complex |
| Maintenance | Low | High |
| Scalability | Limited by role count | Scales with attribute depth |
| Best for | Small orgs, static teams | Hybrid work, dynamic teams |
| Compliance | Easy to audit | Strong for data protection |
Ultimately, the RBAC vs ABAC debate isn’t about which is superior, but which fits your current and future IT realities.
Use RBAC If:
- Your team is small to mid-sized.
- Job roles are stable and well-defined.
- You need something easy to deploy and audit.
Use ABAC If:
- You manage remote or hybrid teams.
- You want context-aware access (e.g., time or device checks).
- You need to meet strict regulations like HIPAA or GDPR.
- Your company is scaling or moving to cloud-native systems.
Combining RBAC and ABAC – The Hybrid Approach
Most modern organizations use a mix of both.
RBAC handles the basics—who’s on what team and what they usually access. ABAC adds the extra layer: when, how, and from where they can access it.
Example:
RBAC grants an HR associate access to payroll tools.
ABAC ensures they can only use it on weekdays, from the office, using a secure device.
Benefits of the Hybrid Model:
- Reuse roles while adding dynamic context.
- Lower risk without creating an admin nightmare.
- Easier path toward Zero Trust frameworks.
Other Access Control Models
While the ABAC vs RBAC vs PBAC discussion dominates modern access security strategy, other models like ACL and DAC still serve specific use cases. Here’s a quick guide to three additional models:
PBAC (Policy-Based Access Control)
PBAC uses a rule engine to define access permissions based on policies that work like logical statements. For example, a policy might specify, “Only allow finance access during Q4 audits.” This model is particularly useful for high-level business policies, allowing administrators to manage access based on predefined conditions.
ACL (Access Control List)
An Access Control List (ACL) is a simple method of managing access that generates a list of users and their permissions for each resource. ACLs are simple to set up, but as businesses grow, they become more complicated and less useful, particularly in cloud environments or huge, dispersed systems.
DAC (Discretionary Access Control)
In DAC, users can define who can access their resources. While this provides flexibility, it can also lead to over-permissions, creating security risks as users may grant excessive access to others. As such, DAC can cause access sprawl if not managed carefully.
Each of these models offers unique benefits and challenges. Depending on your organization’s structure and security needs, you may find one or a combination that suits your environment best.
Beyond Access Models – Toward Zero Trust
RBAC and ABAC are great foundations, but Zero Trust demands more.
With ZTNA (Zero Trust Network Access), every request is verified in real-time. Not just based on identity, but also device health, session risk, and more.
This is critical for:
- BYOD environments
- Temporary cloud resources
- Contractors and short-term access needs
At AuthX, we integrate MFA software, SSO, and real-time risk checks into RBAC/ABAC models, so you can build access strategies that evolve toward Zero Trust without disruption.
AuthX PoV – Smarter Access Starts Here
Whether you prefer RBAC, ABAC, or something in between, AuthX can help you implement:
- SSO auth+ MFA for strong identity verification
- Context-aware policies for dynamic access
- Risk-based rules that evolve with your organization
We’re built for industries where precision matters—like healthcare, education, retail, finance and manufacturing—where access decisions can’t be one-size-fits-all.
Final Thoughts
Access control is crucial for scaling securely in today’s digital world. While RBAC offers simplicity, ABAC provides flexibility for dynamic environments. Many organizations are moving toward hybrid models to combine the strengths of both. As Zero Trust authentication becomes the future, it’s essential to focus on context and continuous verification. At AuthX, we help organizations build smarter, more secure access strategies tailored to their needs, ensuring secure access, no matter the environment.
FAQs
What is RBAC vs ABAC vs PBAC?
What is access control and why is it important?
Access control defines how users are granted access to systems and data. It’s essential for protecting sensitive information, preventing insider threats, and complying with regulations.
What is the difference between Role-Based Access Control and Attribute-Based Access Control?
Role-Based Access Control (RBAC) uses user roles to grant access, while Attribute-Based Access Control (ABAC) evaluates multiple attributes like user department, device, and time of access to make dynamic decisions.
Is hybrid access control better than using RBAC or ABAC alone?
In many cases, yes. A hybrid model leverages the simplicity of RBAC with the contextual intelligence of ABAC offering better control without overwhelming IT teams.


