Roles were great—until everything changed.
Workforces became hybrid, devices multiplied, and regulations tightened. Suddenly, “Manager” or “Finance Team” wasn’t specific enough to determine access. That’s where most organizations hit a wall. Role-Based Access Control (RBAC), once the go-to solution, started feeling more like a one-size-fits-all tool in a world that demands a tailored fit.
According to a GigaOm study, Attribute-Based Access Control reduced policy burden by 93 times compared to RBAC, requiring just 8 policy changes where RBAC required 745.
That’s where ABAC access control comes in. It doesn’t ask what your title is, it asks who you are, what you’re accessing, and under what conditions.
This isn’t just an upgrade to RBAC. It’s a shift in mindset from static roles to dynamic decision-making.
Let’s break down what is ABAC, what makes it different, and why more teams are calling it the authorization model of choice.
What Is ABAC?
ABAC stands for Attribute-Based Access Control. It uses attributes (metadata) to determine who gets access to what, under which conditions.
Unlike RBAC, where access is based solely on a user’s role (e.g., “Manager” or “HR”), attribute access control evaluates a richer set of data points like:
- The user’s department
- The sensitivity level of the resource
- The time of day the request is made
- The device or location involved
- And a dozen other contextual signals
The idea is simple: access control security should mirror real-world logic.
Here’s an Attribute-Based Access Control example:
“Only full-time finance employees in the U.S. can export payroll data, but only on weekdays between 9 AM and 6 PM from corporate laptops.”
This isn’t a one-off policy; it’s how attribute access control works by design. It evaluates every access request using attributes of subject, resource, action, and environment.
The Core Elements of ABAC
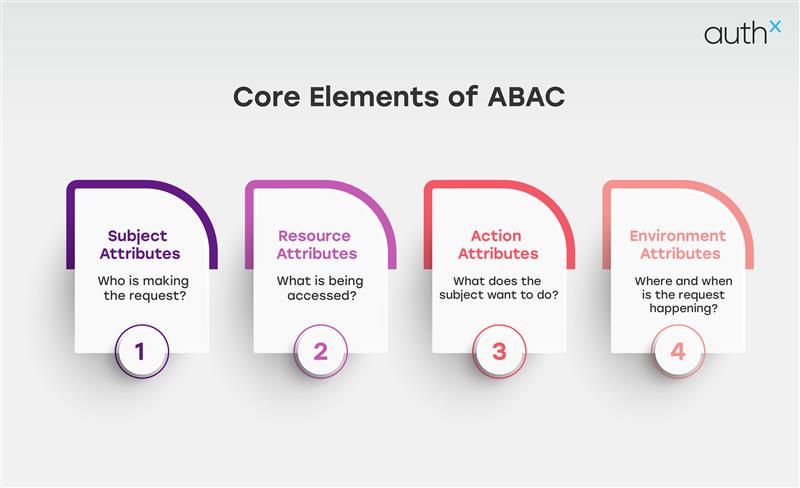
Let’s unpack the four major building blocks:
- Subject attributes –Who is making the request? Consider department, job title, clearance level, device compliance, etc.
- Resource attributes – What is being accessed? Maybe it’s a database tagged “confidential”, or a record marked “VIP.”
- Action attributes – What does the subject want to do? View, edit, delete, transfer?
- Environment attributes—Where and when is the request happening? Time, geolocation, device posture, and network type all matter.
When a user initiates an action, the system evaluates the request based on these attributes and policies. The result? Real-time access decisions that reflect real-world context.
ABAC vs. RBAC: Where Role-Based Falls Short?
Most organizations start out with a handful of roles and tidy policies. But as teams grow, locations multiply, and exceptions pile up, you end up with role explosion. ABAC access control flips the model. Instead of hardcoding logic into fixed roles, you define conditional policies and let attributes do the heavy lifting.
| Feature | ABAC | RBAC |
|---|---|---|
| Control Model | Attribute-based (dynamic) | Role-based (static) |
| Policy Logic | Conditional, contextual | Role-defined |
| Flexibility | High – adapts to org changes | Low – requires manual updates |
| Granularity | Fine-grained, condition-based | Coarse-grained |
| Common Pitfall | Policy complexity | Role explosion |
| Ideal For | Complex, regulated, growing orgs | Small to medium-sized static orgs |
What Makes ABAC Powerful in Practice?
ABAC earns its keep in complex, compliance-heavy, and dynamic environments. Think:
- Healthcare : A nurse should access patient records only if assigned to that patient, during their shift, from a hospital-managed device. ABAC cyber security policies can enforce all that.
- Banking & Finance : An employee in wealth management may view client portfolios but not download them unless they’re in the office, on a VPN, and cleared for that asset class.
- Education : Professors can update grades only for courses they teach and during exam periods.
- Government : Sensitive records are restricted to users with certain clearance levels and only from devices passing endpoint compliance checks.
This is where Attribute-Based Access Control examples turn policy into real-world enforcement.
How ABAC Works Behind the Scenes
Here’s a simplified flow:
- A user initiates an action (say, downloading a document).
- The system gathers real-time data about the user, device, and environment.
- The policy engine evaluates the request against pre-defined rules.
- If conditions match, access is granted (and logged). Otherwise, it’s blocked or flagged.
Modern platforms make attribute access control more manageable with integrations to IAM solutions, HRIS, and SIEM tools.
Benefits of ABAC (That Go Beyond Security)
Let’s talk about business impact. Here’s what we’ve heard from customers after shifting to ABAC:
- Context-Aware Access: There are no longer static policies. Decisions adapt to the user’s location, time, device, and risk level.
- Operational Efficiency: No more role maintenance nightmares. Fewer access-related tickets. Simpler onboarding.
- Compliance Confidence: You can bake regulatory logic into policies—HIPAA, PCI, GDPR, etc.—and prove enforcement with clean logs.
- Fewer Mistakes: Granular rules reduce over-provisioning. You avoid the “just give them admin for now” trap.
- Smooth User Experience: Users get what they need—no more, no less—without delays from manual reviews.
ABAC Challenges (And How to Overcome Them?)
ABAC cyber security is powerful but not always plug-and-play:
- Complexity : Policies can get verbose if not appropriately managed. You’ll need a way to test and visualize them.
- Attribute Management: You need clean, trusted data. If attributes are outdated or inconsistent, ABAC decisions won’t work.
- Policy Sprawl: The freedom to define any logic can lead to over-engineered rules. Governance matters.
The good news? Modern ABAC platforms (like AuthX) offer visual policy builders, real-time simulators, and attribute validation tools to make life easier.
Is ABAC Right for You?
Ask yourself:
- Are roles alone no longer cutting it?
- Do you manage complex organizational structures or sensitive data?
- Are you juggling multiple compliance frameworks?
- Are access reviews turning into a quarterly headache?
If yes, it might be time to explore what is Attribute-Based Access Control in depth.
Some organizations pilot ABAC cyber security in one department (like HR or finance). Others run it alongside RBAC, transitioning gradually.
Either way, the shift is happening. Access is becoming conditional, contextual, and dynamic.
ABAC: The Future of Access Control
In a world where people work from anywhere, use anything, and expect instant access to everything, static roles are a blunt tool.
Attribute-Based Access Control provides the precision, agility, and intelligence needed to control access at scale.
It’s not just about better security. It’s about matching your access control strategy to your business’s operations. And in 2025? That’s not optional, it’s essential.
FAQs
What is Attribute-Based Access Control (ABAC)?
ABAC is a dynamic access control security method that uses attributes like user role, location, and device to determine access.
How does ABAC improve access control compared to RBAC?
ABAC avoids static roles by using real-time data for decisions, offering more flexibility and reducing the need for dozens of predefined roles.
What is an example of Attribute-Based Access Control in action?
A policy allowing only U.S.-based HR staff to access payroll data during work hours on company devices is a classic ABAC use case in access control security.
Is ABAC suitable for small organizations?
Yes, especially for those handling sensitive data or compliance needs—it’s scalable and easier to manage with modern tools.


