Authentication Methods that Work as Fast as Your Team
Prioritize users, streamline access, and protect your business with AuthX’s advanced authentication methods, designed to boost productivity while keeping your organization safe.

It’s Time to Rethink How You Authenticate
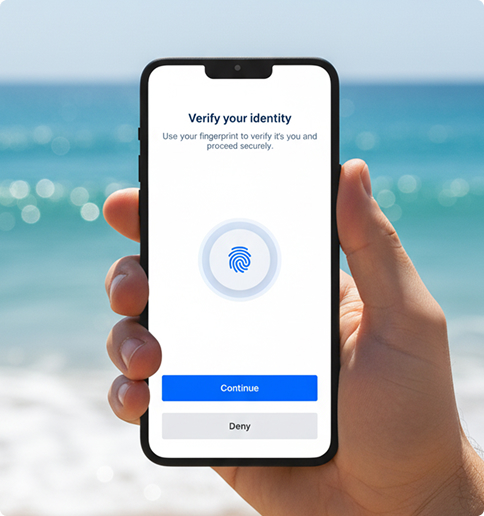
Biometric Authentication
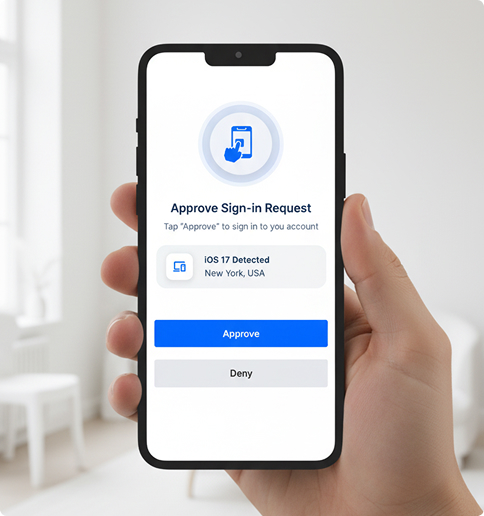
Mobile Push Authentication
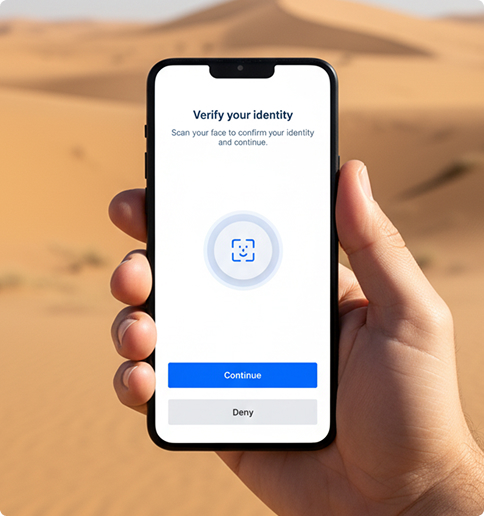
Mobile Face-Verify

FIDO & Passkeys
AuthX supports cryptographic logins via FIDO standards and passkeys, providing strong, passwordless security for devices and cloud applications. It’s fast, secure, and user-friendly.

OTP / Passcode Support
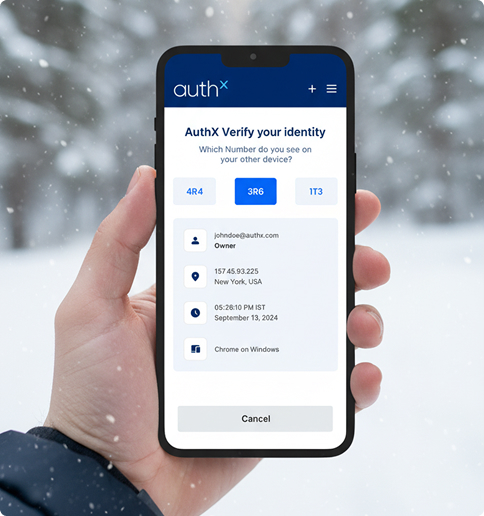
Visual Push

Security Tokens
Hardware security tokens, including devices like YubiKey, generate one-time codes or cryptographic keys. They deliver robust, password-free authentication across systems and apps.
AuthX Passcode Support
Benefits of Efficient and User-Friendly Authentication
Improved User Experience
With our passwordless authentication methods, users can access their accounts quickly and easily without the hassle of remembering multiple passwords.
Flexibility and Scalability
AuthX's secure authentication methods can be tailored to fit the unique needs of any organization, regardless of size or industry, and can easily scale as the organization grows.
Increased Productivity
With faster and more secure access to systems and data, employees can perform their tasks more efficiently, leading to overall increased productivity.
Cost Efficiency
By reducing the reliance on traditional password management and minimizing security breaches, organizations can save on costs associated with password resets and data breach recovery
Seamless Access, Zero Friction
AuthX ensures secure logins across applications with minimal prompts, letting users focus on their work without interruptions.
Frequently asked questions
What are the main types of authentication methods?
Authentication methods fall into three primary categories:
- Something you know: Knowledge-based credentials, like passwords, PINs, or personal security questions.
- Something you have: Physical items, such as security tokens, smart cards, or mobile devices that generate or receive one-time codes.
- Something you are: Biometric data, including fingerprints, facial recognition, or iris scans.
These methods are often combined for Multi-Factor Authentication(MFA) or Two Factor Authentication (2FA) to strengthen security by requiring multiple forms of verification.
How does authentication differ from authorization and accounting (AAA)?
Authentication, authorization, and accounting form the AAA framework to secure user access:
- Authentication verifies the user’s identity using methods like passwords, MFA, or SSO.
- Authorization determines what tasks, resources, or data a user can access after authentication.
- Accounting tracks user activity, including session duration and data usage, which helps monitor compliance, optimize resources, and improve security controls.
Together, AAA ensures that only the right users access the right resources while maintaining accountability.
Why is passwordless authentication considered more secure and efficient?
Passwordless authentication eliminates traditional passwords, which are often weak, reused, or stolen. Instead, it relies on secure methods such as biometrics, passkeys, hardware tokens, or mobile push notifications. This approach:
- Reduces the risk of phishing and credential theft.
- Improves productivity by removing password typing and reset workflows.
- Provides a frictionless user experience while maintaining high security standards across devices and applications.
How do multi-factor and adaptive authentication enhance security?
MFA requires users to present two or more authentication factors from different categories (knowledge, possession, or biometrics). Adaptive authentication goes a step further by dynamically adjusting security requirements based on contextual signals, such as:
- Device type or location
- Time of access
- User behavior patterns
This layered, risk-based approach ensures stronger protection against unauthorized access while keeping the login experience smooth for legitimate users.
