What is Passwordless Authentication and how to use it?

Passwordless Authentication – Imagine that you didn’t have to use passwords anymore. Let me tell you how;
Usually, when you need to access restricted data or web applications, you have to authenticate yourself using a username and password. And, in many circumstances, we choose our passwords, and sometimes we may occasionally allow an automated password generator to create credentials for us to access.
But here’s the thing: we might need to log into a lot of apps using a lot of different credentials. Some web applications may even have their own set of criteria for creating passwords for authentication. Now, that’s a lot of passwords to remember.
For each application, the user should remember or make a note of the credentials, save them in a secure location digitally, or write them down and keep them physically. However, they will eventually forget their credentials and the place they saved, resulting in the loss of the accounts for all web applications. Moreover, forgetting passwords can lead to hackers breaking into accounts.
Find out how passwordless authentication can help us avoid password fatigue and how it can safeguard our web accounts and provide streamlined access to web applications.
How is passwordless achieved?
A passwordless authentication method is one in which the user does not need to provide a password every time to verify their identity. The purpose of passwordless authentication is to eliminate the use of written passwords by using the best authenticator platforms in the industry.
AuthX provides modular solutions, allowing you to select the appropriate authentication method for your needs.
* 2021 DBIR Data Breach Investigation Report, Verizon
Using passwords presents many usability problems and security risks. With passwordless authentication factors, you can perform Multifactor Authentication by adding two or more authentication steps to avoid security issues and seamless access to user devices.
Biometric authentication, Mobile Authentication, One-Time Password (OTP), and Hardware tokens are the most common authentication methods. By using these factors, the user and his identity can be authenticated in real-time.
Passwordless authenticators use Unique biological factors for accessing your computer. The fact that it’s difficult to replicate biological characteristics increases security and provides quick access to networks.
To provide a seamless authentication procedure, AuthX covers a series of authentication methods. All of this can be accomplished without the use of a password through AuthX.
Authentication Factors
Let’s dive into the different authentication methods and how to use them effectively
Biometric
Each person has a unique biometric fingerprint, and only you have that pattern. Other people’s fingerprints cannot be matched to yours. As a result, fingerprints are always the most reliable authentication factor.
Any individual who registered their fingerprint to the database can use it effectively among your enterprise without any friction.
Use Cases :
- Most banking apps now have a fingerprint sensor, allowing you to complete transactions only with a tap on the sensor.
- Lock and unlock your mobile device using a fingerprint scanner.
People can be recognized in images, videos, or real-time using facial recognition technologies. Using facial recognition, users can have faster access to workstations.
Every industry has an Identity and Access Management system in place to identify users and grant them access to assigned devices. Facial recognition is used to simplify the IAM process, minimize friction between administrators and users, and save money.
Use Cases :
- The law enforcement department has been a significant use case for facial recognition since the technology’s development.
- Most of the small businesses and large organizations also use Facial Recognition to record employees’ attendance.
Mobile
With a simple tap, confirm logins with push notifications to your device.
A secure application on the user’s smartphone receives a push notification when an authentication attempt is made. Users can check authentication details and authorize or reject access with the push of a button.
With Push notification, perform seamless access and eliminate the need for passwords.
Use Cases :
Push notifications are becoming increasingly popular due to their ease of use for users and low cost of implementation for IT administrators.
Most IT organizations use push notifications for swift logins.
With the Mobile Authentication method, receive OTP through SMS to your registered mobile number. Then enter the OTP and gain access to your workstation. This simple authentication factor requires no passwords.
Users can perform mobile authentication through existing mobile devices.
Use Cases :
OTP is widely used in mobile transactions, payments etc.
All banking apps use the OTP method to verify user identity through registered mobile numbers.
Time-based One-Time Password (TOTP) generators are hardware key fobs or software tokens. By using the current authentication server, it generates One-Time passcodes. We can only use TOTP for a limited time before they expire.
Users receive a new TOTP every 30 seconds through their mobile devices.
Use Cases :
- The world’s largest multinational corporations such as Google and Microsoft utilize TOTP.
- Customers can use the TOTP method for seamless authentication to restricted online applications.
Users who choose the call option will receive an automated phone call to their registered mobile number. A computerized voice will tell you the OTP during that call. Users can use that OTP to gain access to their workstations Users’ identity is verified through OTP received to the mobile device. For authentication purposes, users can combine two or more authentication factors instead of a password to improve security.
Use Cases :
Telecom service providers use voice authentication methods to connect with the consumers. All banking industries use voice call options to deliver OTP to their respective customers.
Hardware Token
Hardware tokens offer the strongest phishing defense but are also easy to use. YubiKeys are available in a variety of formats and support multiple authentication protocols, ensuring their great user experience while protecting your favorite apps and online services.
Use Cases :
All security firms, Internal Bank operations, use Hardware tokens.
RFID
RFID technology captures digital data embedded within RFID tags or smart labels using radio waves and then stores the data from the tag or label into a database
Using a multi-factor authentication (MFA) solution, users can gain access to their desktop without a password with tap-in/tap-out authentication, saving time without compromising security.
Use Cases :
- For inventory management and warehouse storage, RFID is critical in security systems.
- IT Companies use RFID ID cards to authenticate employees’ digital identities.
Offline Authentication
When your device does not have an internet connection, these authentication steps will help you to log in.
Select the Offline option on the computer and scan the QR code with your mobile device to easily connect to your workstation.
Use Cases :
- Many enterprises provide Offline Authentication Mode to consumers when they don’t have access to the internet and need to log in to their devices.
5 Best practices for passwordless authentication
Register device properly
Before using a passwordless authentication application, you must correctly register your digital identity. Register your mobile phone number and all other necessary information with the application. To get rid of passwords, you must first choose an authenticating factor that works best for you.
Implement Two-Factor Authentication
Confirm your identity using a one-time code shared to your mobile device, or log in using a fingerprint scanner or any other available factors. The concept is that with two-factor (or multi-factor) authentication, an attacker cannot acquire access simply by guessing or cracking the password.
Single Sign-On with Passwordless authentication
Enterprises that use many applications will achieve significant security benefits from eliminating passwords by combining an SSO method with passwordless multi-factor authentication.
With Single sign-on, passwordless authentication reduces the friction between IT Admin and the user. With Cloud computing, SSO can connect multiple web applications with a single login credential through remote access.
Passwordless Authentication for Identity Management
Passwordless authentication integrates with Identity and access management (IAM) to verify the identity of the user and the device to provide seamless access and identity management solutions. Passwordless authentication reduces the possibility of phishing assaults and identity theft.
Easy deployment through local and remote servers
Businesses are moving away from local servers and toward cloud-based servers, which connect users and their workstations from all over the world. Passwordless authentication tools help the industry by facilitating instant deployment and generating real-time reports for all PCs connected to the company.
Statistics: “By 2022, Gartner predicts that 60% of large and global enterprises, and 90% of midsize enterprises, will implement passwordless methods in more than 50% of use cases — up from 5% in 2018.”
(Embrace A Passwordless Approach To Improve Security (gartner.com))
Reason to go passwordless
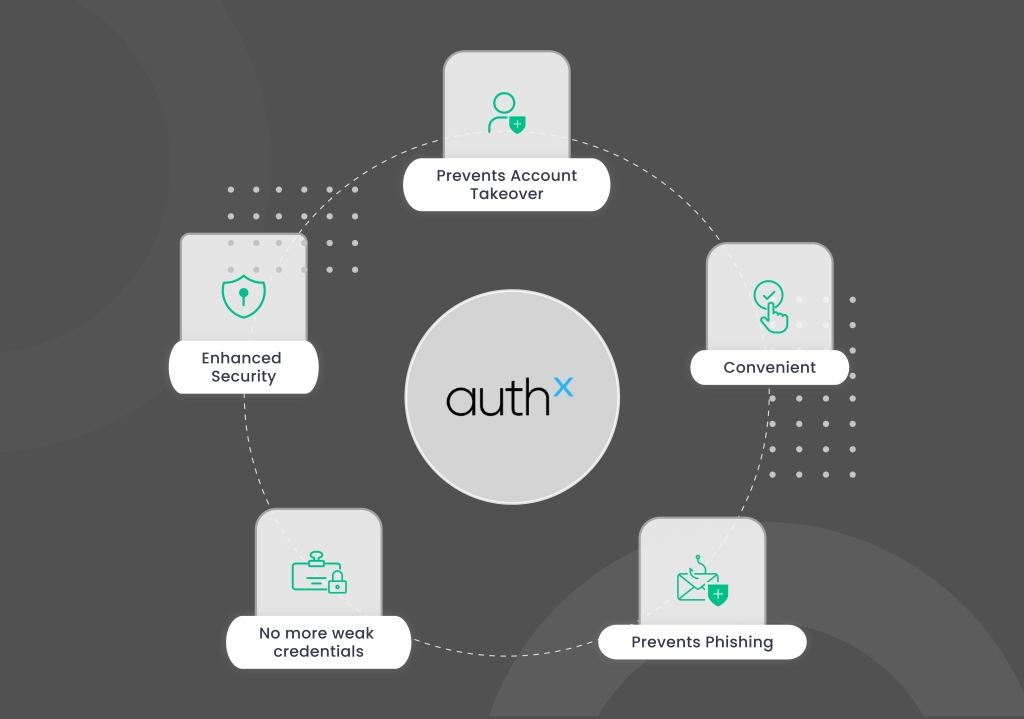
- Prevent account takeover: Safeguard your account from hackers and cyberattacks by enabling passwordless authentication.
- Prevent Phishing: By using passwordless authentication, you can prevent phishing emails from compromising your account.
- Convenience: Avoid writing long passwords to access your workstation by authenticating your desktop with a simple push of a button.
- No more weak credentials: Eliminate the need for passwords and strengthen your account security by integrating with Authenticator apps.
- Enhanced security: Multifactor Authentication (MFA) is a security feature that adds an extra layer of security to workstations and user identities.
Conclusion
People nowadays carry several user passwords and identities for a variety of web applications. Having multiple credentials for a single identity, the user puts the individual and the organization at risk. Passwordless authentication will make it easier for users to handle their user credentials for social networks, official accounts, and any other web accounts that require login.
AuthX provides a wide range of authentication services. AuthX offers identity management and workstation security solutions, ranging from multi-factor authentication to single sign-on.