Adaptive Access Security
Enhance your security with advanced, context-aware access controls that dynamically respond to user behavior and risk using adaptive access technologies.
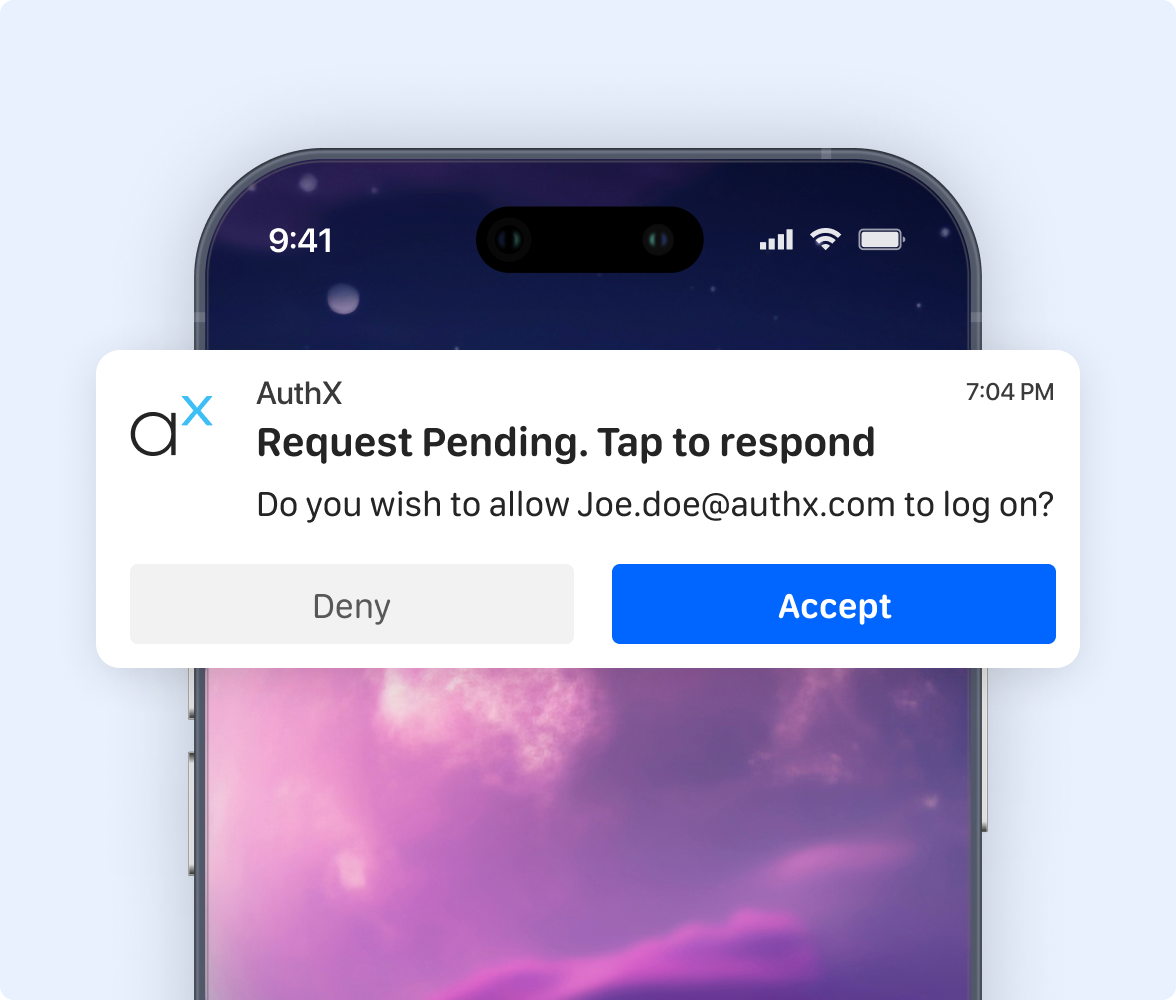
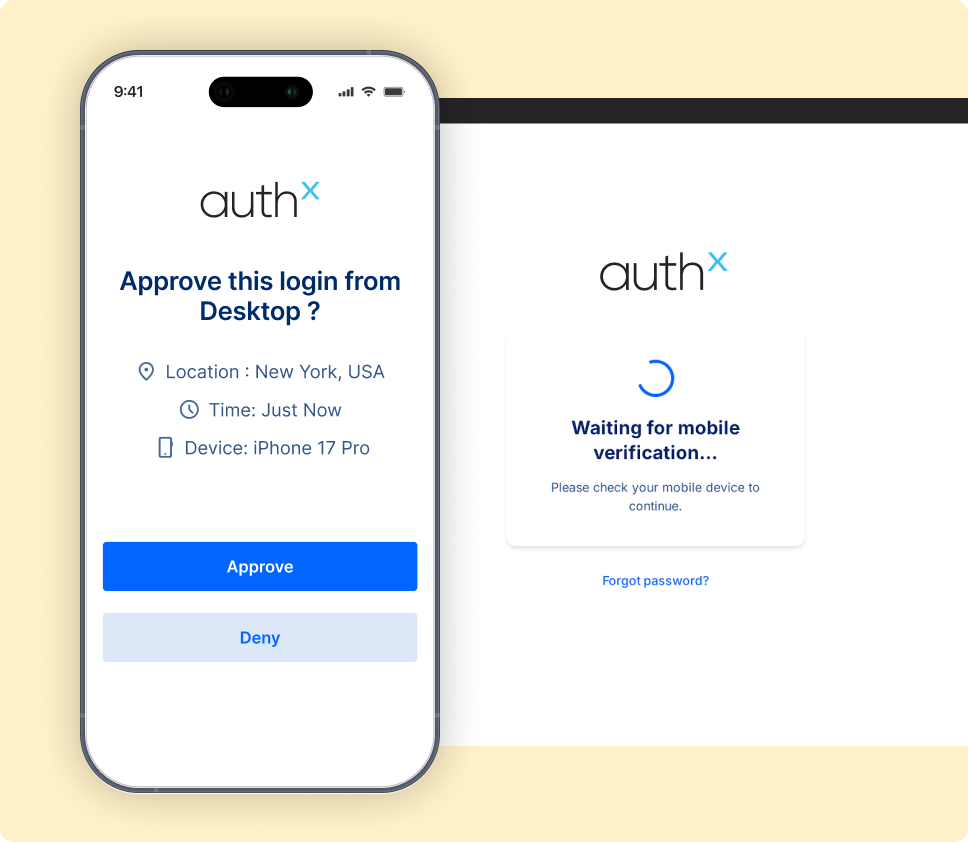
Adaptive Access Security That Responds to Risk in Real Time
Adaptive Access Security continuously evaluates user behavior and context to adjust access in real time. When risk changes, such as a new device or location, additional verification is applied automatically, balancing strong security with a smooth user experience.
How does it work?
Adaptive access security works quietly in the background, making smart decisions every time someone tries to log in, without turning your users’ lives into an obstacle course. Here’s how it plays out in the real world:
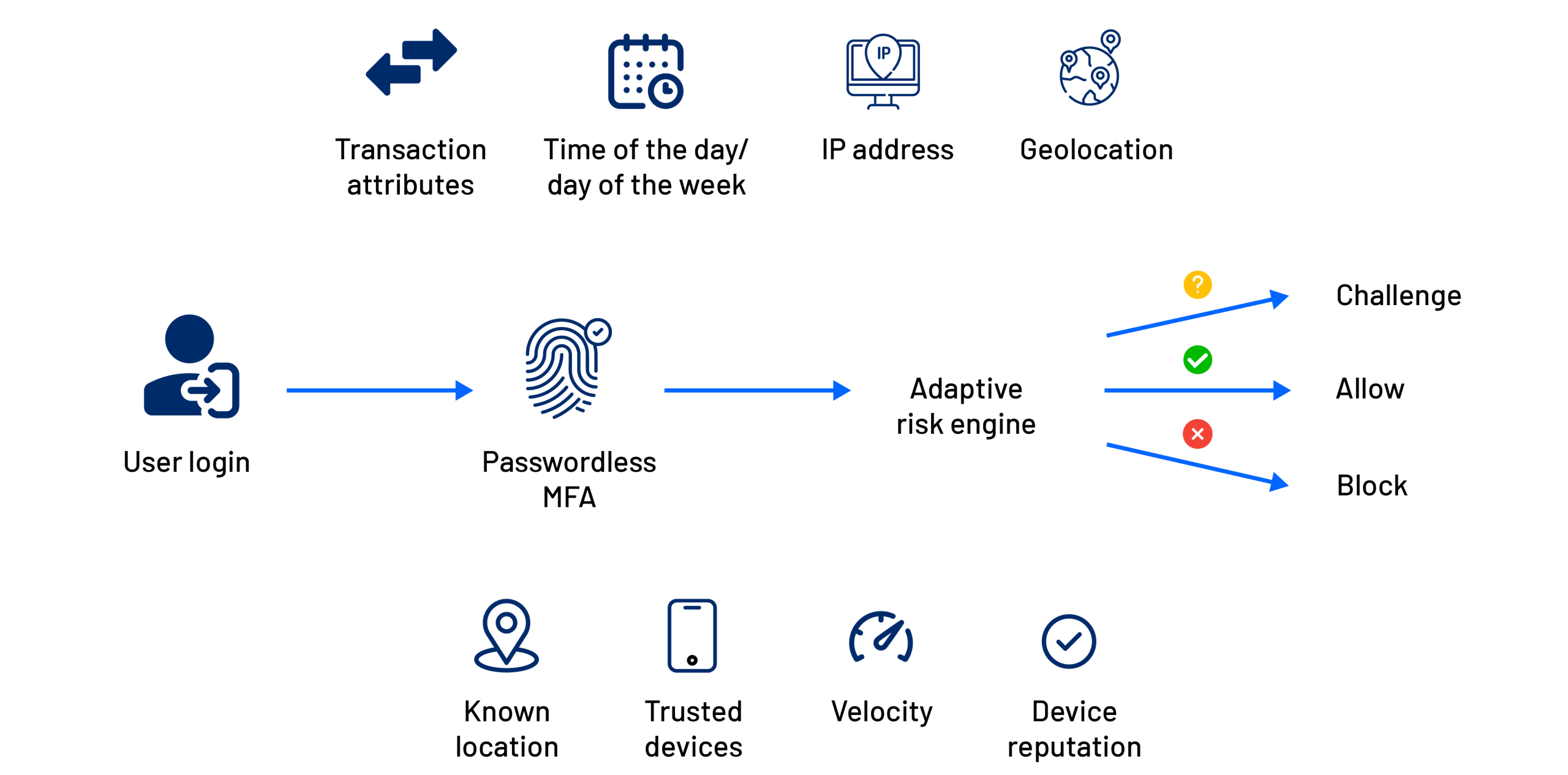
Experience the Benefits of Risk-Based Adaptive Authentication
Protection from Untrusted Networks
Only compliant devices and trusted networks are allowed access, while suspicious connections are automatically blocked or challenged.
Granular Access Control
Access policies adjust dynamically based on role, context, and data sensitivity as authentication risk changes.
Real-Time Risk Response
Unusual behavior is detected instantly, triggering additional verification or access restrictions without disrupting legitimate users.
Upgrade Authentication When Needed
Adaptive security that understands context, challenges risky access, and keeps trusted users moving without friction.
Recognizing Devices
Verifying specific devices before granting access.
Using Geolocation
Confirming the legitimacy of access attempts with location data.
Analyzing Behavior
Monitoring and assessing user behavior patterns for anomalies.
Validating IP Addresses
Checking the origin of access requests to prevent malicious activities.
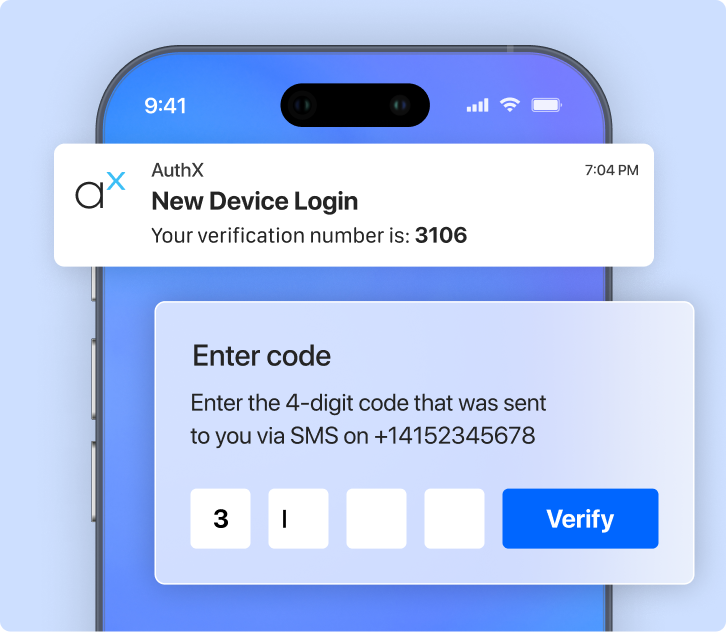
Implementing Adaptive Authentication with MFA
Enable adaptive workflows that smoothly integrate Multi-Factor Authentication (MFA) with advanced login risk analysis.
By dynamically adjusting authentication methods based on real-time risk assessments, AuthX ensures optimal security without compromising efficiency or user convenience. This approach allows for precise customization of authentication levels.
Key Benefits of Adaptive Access Security
Enhanced Protection
Reduce the risk of unauthorized access by continuously monitoring and adapting to threats using adaptive access control.
Zero Trust Approach
Align your security strategy with a zero-trust framework by implementing adaptive auth and ensuring continuous verification.
User Convenience
Maintain a seamless user experience by introducing additional authentication steps, when needed, with adaptive authentication solutions.
Real-Time Responses
Quickly adapt to changing risk levels and threats with proactive security measures driven by adaptive access.
Cost-Effective
Save potential costs associated with security incidents through preventative measures.
Improved Compliance
Meet industry standards and regulatory requirements through layered, dynamic security including adaptive authorization.
