Future-Proofing Access: A Deep Dive into Role Based Access Control (RBAC)

Managing user access isn’t just about convenience, it’s about security and compliance. Yet, many organizations still rely on outdated methods that make access management a headache. Employees have too much or too little access, IT teams scramble to fix permission issues, and security risks grow unnoticed.
Role Based Access Control (RBAC) changes the game. It streamlines access management, strengthens security, and ensures compliance. If your organization is still manually assigning permissions, it’s time for a shift.
What is Role Based Access Control (RBAC)?
RBAC is a security framework where access permissions are assigned based on roles rather than individual users. Instead of granting access one by one, organizations define roles like HR, IT Admin, or Finance, and assign users accordingly.
We see RBAC in action everywhere:
- A nurse can access patient records but can’t prescribe medication.
- A finance team member can view invoices but can’t modify company budgets.
- A customer support agent can read but not edit client information.
RBAC applies to both digital security (software, databases) and physical security (badge access to restricted areas).
Why Organizations Need RBAC?
Improved Permission Management
One of the biggest challenges in IT is managing permissions at scale. Manually assigning access is a nightmare. With RBAC, you set permissions once per role and assign users to those roles, ensuring consistency and efficiency.
Strengthened Security and Compliance
RBAC follows the Principle of Least Privilege (PoLP), meaning users only get the access they need, nothing more. This reduces insider threats and accidental data leaks.
Regulatory compliance is another major driver. RBAC helps organizations meet HIPAA, GDPR, and PCI-DSS requirements by maintaining structured access controls and audit trails.
Scalability and Efficiency
RBAC scales effortlessly. Whether you have 50 employees or 50,000, permissions remain organized. IT admins no longer need to track individual user access, roles handle it automatically.
How RBAC Works?
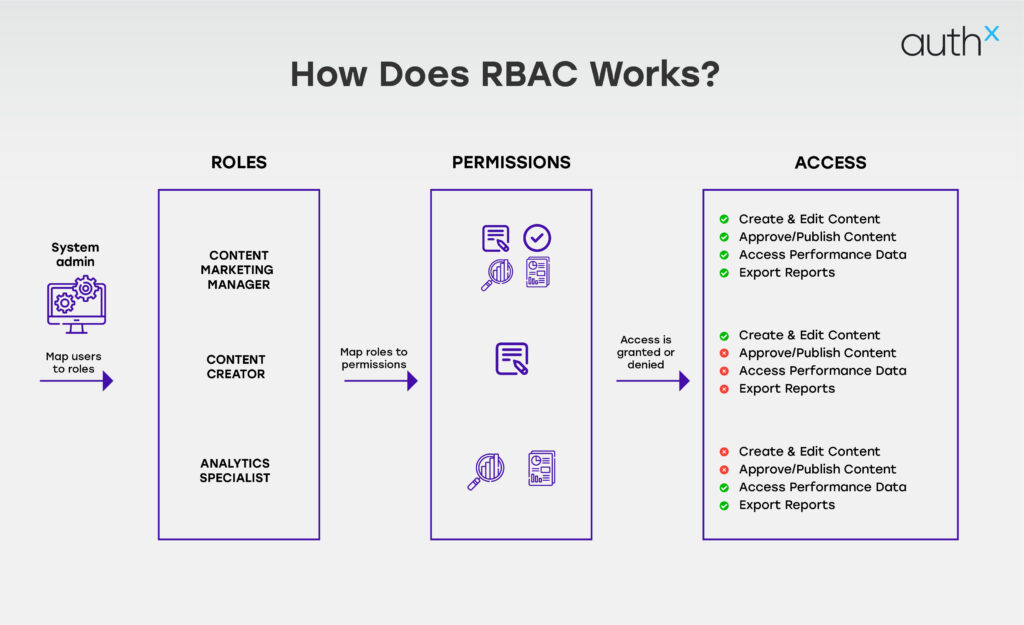
- Define Roles – Identify key job functions (HR, IT Admin, Finance). Establish role-based access based on responsibilities and operational needs. Ensure roles are structured to minimize excessive permissions.
- Assign Permissions – Link each role to specific system actions (read-only, edit, approve). Follow the principle of least privilege to limit access to only what’s necessary. Ensure permissions align with compliance and security policies.
- Assign Users to Roles – Users inherit permissions from their assigned role. Automate role assignments where possible to streamline onboarding. Regularly review and update role assignments to reflect personnel or responsibility changes.
- Ensure Separation of Duties – Prevent conflicts of interest (e.g., one person initiates a payment, another approves it). Establish clear rules to avoid excessive control by a single user. Monitor role changes to prevent security loopholes.
Key Components of RBAC
Security Principals
RBAC applies to users, groups, service accounts, and even applications. Every entity that needs access to a system is considered a security principal. Properly defining these principals ensures access control is both effective and manageable.
Role Definitions
Roles can be predefined (Admin, Read-Only) or customized based on business needs. A well-structured role definition simplifies user management and minimizes unnecessary access. Clear role boundaries prevent privilege creep, where users accumulate excessive permissions over time.
Scope of Access
RBAC isn’t a one-size-fits-all model. It can be applied at different levels to match organizational needs. Some roles may grant access across an entire company, while others may be restricted to specific departments or individual applications. Defining the right scope prevents excessive or unintended access.
Types of RBAC Models
Core RBAC
Basic structure where roles define access levels. It provides a simple way to manage user permissions without assigning them individually. This model is ideal for organizations looking for a simple yet effective access control system.
Hierarchical RBAC
Roles inherit permissions from higher-level roles. A senior engineer gets full system access, while a junior engineer has limited permissions. This model improves scalability by reducing redundancy in role assignments and simplifying permission management.
Constrained RBAC
Separation of duties ensures no single user has too much control. Example: One employee submits an expense report, another approves it. This model reduces the risk of fraud or errors by distributing critical tasks among multiple users.
Symmetric RBAC
Allows flexibility while maintaining visibility over permissions. It ensures that permissions can be adjusted dynamically while maintaining security and compliance. This model is useful for organizations with frequently changing roles and responsibilities.
RBAC vs. Other Access Control Models
| Model | How It Works | Pros | Cons |
|---|---|---|---|
| RBAC | Access based on roles | Scalable, efficient | Needs well-defined roles |
| Mandatory Access Control (MAC) | Central authority assigns permissions | High security | Less flexible |
| Discretionary Access Control (DAC) | Owners assign permissions | More control for users | Harder to manage at scale |
| Attribute-Based Access Control (ABAC) | Access based on attributes (location, time) | Dynamic | Complex implementation |
| Access Control Lists (ACLs) | Permissions assigned per user | Granular control | Not scalable |
How to Manage RBAC at Scale?
- Role Hierarchy and Inheritance: A well-structured RBAC system ensures clear hierarchies. For example, IT Admins might have full access, while Help Desk staff have limited access to specific tools.
- Transitive Role Assignments: If a user joins a department, they automatically inherit that department’s role permissions, no manual setup needed.
- Handling Multiple Role Assignments: Users with multiple roles get combined permissions. A Contributor role at the company level and a Reader role at the department level result in the highest applicable level of access.
How Automation Enhances RBAC?
Manual role assignments introduce risks. Automation changes that.
- Reduces Human Error: No more manual mistakes in permission assignments. Automation eliminates inconsistencies that can arise from human oversight. It ensures employees receive the correct access without accidental over-provisioning.
- Improves Security: Automatically removes access when employees leave. This prevents former employees from retaining unauthorized access to critical systems. It also reduces the risk of insider threats by enforcing timely permission revocations.
- Speeds Up Onboarding: New employees instantly receive the right permissions. They can start working on day one without delays caused by access requests. This improves productivity and ensures compliance with organizational access policies.
How AuthX Strengthens RBAC for Enterprises?
At AuthX, we’ve seen firsthand how role-based access transforms security and efficiency. Our platform takes RBAC further with:
- Dynamic Role Management – Automate role assignments based on job functions.
- Seamless Integration – Works across cloud and on-prem applications.
- Adaptive Security – Risk-based authentication adjusts access dynamically.
Organizations don’t just need access control; they need access intelligence. That’s where AuthX makes the difference.
Why RBAC is Essential for Modern Security?
We hear IT leaders say, “Managing permissions is out of control.” The reality is traditional access control doesn’t scale. RBAC does.
It simplifies access, enhances security, and ensures compliance. More importantly, it helps organizations reduce risk without slowing down operations. If your team is still managing access manually, it’s time to rethink your strategy.
With an advanced IAM solutions like AuthX, you can implement RBAC seamlessly and future-proof your access management.
FAQs
What does RBAC mean in security?
RBAC means Role-Based Access Control, where access is granted based on roles, not individuals. This improves security and simplifies permission management.
How does RBAC security enhance compliance?
RBAC security enforces the Principle of Least Privilege (PoLP), reducing unauthorized access. It also helps organizations meet regulatory requirements like HIPAA and GDPR.
Why should businesses implement RBAC?
RBAC means better security, reduced admin work, and streamlined onboarding. It prevents insider threats by restricting unnecessary access.
How does RBAC differ from traditional access control?
RBAC assigns permissions based on roles, unlike DAC, where users control access. It scales better and minimizes security gaps.