What is Password Salting? An Ultimate Guide
We all know that passwords alone aren’t enough to keep accounts secure. Yet, weak password storage remains one of the biggest security gaps in organizations. Attackers don’t need advanced tactics, just a stolen password hash and a little computing power can be enough to crack accounts wide open.
Salting is among the simplest yet powerful methods for enhancing password security. It ensures that hackers cannot utilize precomputed attacks to crack password hashes, even if they manage to steal them. But what exactly is the process of salting and why is it important? Let’s explore it.
What is Salting?
The process of adding a unique, random string (cryptographic salt) to a password before hashing is known as password salting. This guarantees that two users’ stored password hashes will be entirely different, even if they share the same password. Without salting password storage, hackers can compare stolen hashes to known values and crack multiple accounts at once. With salting, every password must be cracked individually, making large-scale attacks far more difficult.
Hashing vs Encryption vs Salting
We hear a lot of confusion between these terms, so let’s set the record straight:
- Encryption: Converts readable data into a secret format using a cryptographic key and an encryption algorithm. The data is protected in transit or storage, but it can be decoded by someone who has the correct key. Common techniques are Rivest-Shamir-Adleman (RSA) and Advanced Encryption Standard (AES). When discussing what is encryption, it’s important to note that while encryption protects data at rest and in transit, salting security ensures that even if password hashes are exposed, attackers cannot easily reverse-engineer them using precomputed attacks.
- Hashing: Using a mathematical algorithm, data is transformed into a unique, fixed length string. Password hashing is one-way, which means that the original data cannot be reconstructed, in contrast to encryption. It is often utilized for data integrity verification and password storage. Bcrypt and SHA-256 are two examples.
- Salting: Enhances hashing by adding a unique, random string (salt) to the data before hashing. This prevents hackers from cracking hashed passwords using precomputed tables, such as rainbow tables. Salting guarantees that two users’ hashed values differ, even if they have the same password.
Why Is Password Salting Important?
Unsalted passwords are extremely susceptible to breaches. When hashed without other security layers, even powerful passwords can be hacked. Password hashing alone isn’t enough, salting is essential for preventing hackers from instantly cracking passwords using precomputed hash tables, such rainbow tables. Even identical passwords produce entirely different hashes when a unique salt is added to each one before hashing, ensuring that no two users have the same saved hash. Because they must guess each password separately rather than using precomputed values, attackers find it much more difficult to employ brute-force or dictionary attacks. A stolen hash might be readily compared to known values without salting, but salting makes password breaches much more difficult and improves security overall.
How Does Password Salting Work?
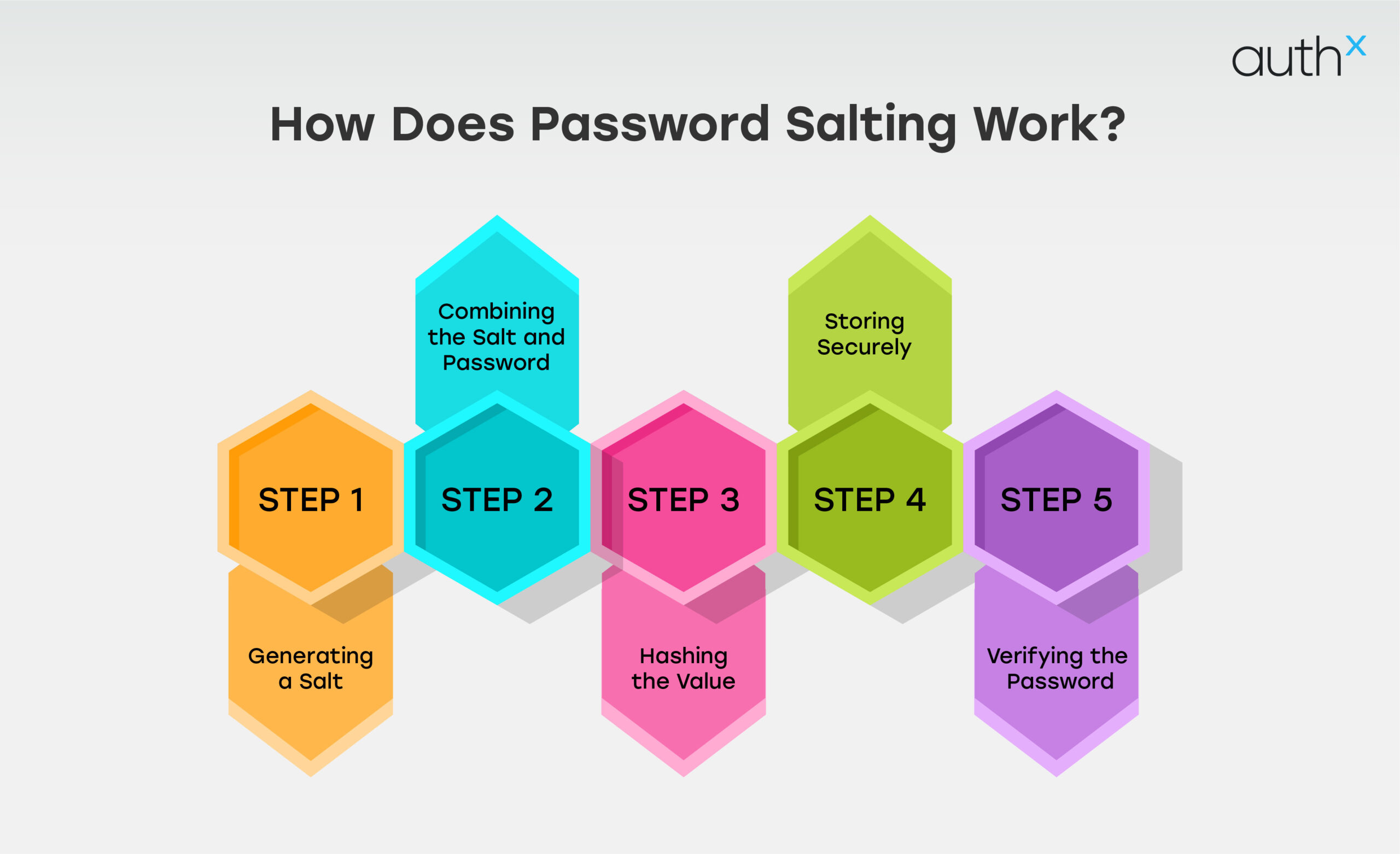
Here’s how salting password storage strengthens security:
- Generating a Salt: The system creates a unique, random string (cryptographic salt) for each password. This ensures that even identical passwords produce different hashes.
- Combining the Salt and Password: Prior to password hashing, the salt is either prepended or appended to the password.
- Hashing the Value: The system creates a unique, irreversible hash by applying a cryptographic hashing technique (such as SHA-256 or bcrypt) on the salted password.
- Storing Securely: The salt and the hash are kept separate in the database. This makes it difficult for attackers to decode the password, even if the hash is exposed.
- Verifying the Password: When a user tries to log in, the system retrieves the original salt, combines it with the entered password, hashes the result, and compares it with stored hash. If the data matches, access is granted to the user.
Example:
Without salting:
- Password: orange → Hash: 5d41402abc4b2a76b9719d911017c592
With unique salts:
- Password: orange + Salt: y3Unz → Hash: 024ca8e38b33f9116c151123eb432d20
- Password: orange + Salt: 1Hx$ → Hash: a64b21d49e1f7f52d3cd3bbdb51c5c77
The hashes of multiple users will always differ, even if they select the same password. By blocking precomputed attacks like rainbow table attack, this greatly improves security by making it more difficult for hackers to guess passwords.
How Salting Strengthens Password Security?
Password salting makes it far more difficult for hackers to decode stored credentials by adding a unique, random value to each password prior to hashing. Salting ensures that every password needs to be cracked individually, even if hackers manage to gain access to a database.
- Brute-Force Attacks: Brute-force attacks include trying every possible password combination repeatedly until the correct one is found. Even though this process takes a long time, adding salt makes it much more challenging. Although many users have the same password, their hashes will differ due to a special salt. This makes large-scale attacks impossible since attackers must crack each password individually rather than applying the same brute-force method to multiple accounts.
- Dictionary Attacks: Many users choose common passwords, making them easy targets for attackers who rely on precompiled lists of frequently used passwords and their hashes. Without salting security, stolen password hashes can be quickly matched against these lists. However, when salting is applied, even if a password appears in a dictionary, its hashed value is unique due to the cryptographic salt. This makes dictionary attacks far less effective, as attackers cannot use precomputed hash lists to crack multiple passwords at once.
- Rainbow Table Attacks: A rainbow table is a huge collection of hash values for popular passwords that have already been computed. A hacker can swiftly compare a list of unsalted password hashes to a rainbow table and crack passwords in just a few of seconds if they manage to steal it. Salting eliminates this risk by ensuring that even identical passwords have unique hash values. Since a separate rainbow table would need to be generated for each unique salt, these precomputed tables become practically useless.
- Reverse Engineering with Known Hashing Algorithms: Kerckhoff’s Principle states that robust cryptographic procedures, not secrecy, should be the foundation of security. This means that even if an attacker understands the exact hashing technique used by a system, they should be unable to easily crack passwords. Salting makes it impossible for attackers to use generic precomputed attacks. This makes it much more difficult to extract plaintext passwords.
Organizations can protect user credentials and reduce the risk of password-related breaches by combining salting with robust hashing algorithms like SHA-256, Argon2, or bcrypt.
Best Practices for Salting Security
- Choosing a Strong Salt: A cryptographic salt should be random, long, and unique for every password to prevent attacks. They must be generated using cryptographically secure random number generators (CSPRNGs) and should never be stored alongside the password hash.
- Storing Salts Securely: To avoid easy access, salts and password hashes should be stored separately. Organizations can utilize encrypted storage or hardware security modules (HSMs) to further secure their salts.
- Ensuring Proper Salt Length: A salt should be at least as long as the hash output to maximize security. For example, when using SHA-256, the salt should be at least 32 bytes to prevent collisions and strengthen password protection.
- Avoiding Common Mistakes: Using predictable values like usernames or timestamps as salts weakens security. Reusing the same salt across multiple passwords or implementing a system-wide salt instead of unique ones per password increases vulnerability to attacks.
- Adding an Extra Layer: Peppering: Peppering involves adding a secret key before hashing, which is not stored in the database. Unlike salts, peppers remain separately secured, making it even harder for attackers to crack passwords, even if they gain access to the hashed values.
Password Salting vs. Modern Authentication Methods
While salting password storage improves security, it’s not a complete solution. Modern methods reduce password risks even further:
| Security Method | How It Works | Key Benefits |
|---|---|---|
| Password Salting | Adds a unique cryptographic salt before hashing | Ensures unique hashes, prevents precomputed attacks like rainbow tables |
| Multi-factor Authentication (MFA) | Requires multiple authentication factors (e.g., password + OTP, biometrics) | Strengthens security by requiring additional verification beyond passwords |
| Identity and Access Management (IAM) | Centralizes authentication, access control, and user identity management | Streamlines authentication, enforces policies, and enhances security across systems |
| Passwordless Authentication | Uses biometrics, security keys, or mobile authenticators instead of passwords | Eliminates password risks while providing a seamless and secure login experience |
Bottom Line: While password salting enhances traditional authentication, MFA, IAM, and Passwordless authentication provide scalable, future-ready security solutions.
Why Businesses Need Strong Authentication Measures?
Salting alone isn’t enough but it’s a crucial layer of defense. When combined with strong hashing, MFA, and IAM solutions, it significantly reduces password security risks.
The future? Passwordless authentication. No passwords mean no hashes to crack, no credentials to steal, and no brute-force attacks to deal with. It’s time for businesses to completely abandon passwords if they want to stay ahead.
FAQs
What is salting, and why is it necessary?
Salting adds a unique cryptographic salt to each password before hashing. This prevents attackers from using precomputed hash tables to crack passwords.
How Long Should a Salt Be?
A salt should be at least 32 bytes, ideally matching the hash length, to maximize randomness and security.
Should Every User Have a Unique Salt?
Yes, using a unique salt for each password ensures no two hashes are the same, preventing attack patterns.
Can a Salt Be a Simple Value Like a Username?
No, predictable salts can be guessed, reducing security—always use cryptographically random values.
What is encryption, and how is it different from hashing?
Encryption converts data into a secure format that can be decrypted with a key, while hashing is a one-way process that cannot be reversed.


