What is Identity Verification? The Key to Secure Access with AuthX Verify

Security teams fight unauthorized access every day. But here’s the problem: most organizations rely on usernames, passwords, and even MFA without verifying who is behind the screen. Cybercriminals don’t need to hack in when they can just log in using stolen credentials.
This is where identity verification changes the game. Instead of assuming someone is who they claim to be, it confirms their real identity before granting access. Whether a healthcare provider is accessing patient records or an employee logging into a corporate system, identity verification ensures only legitimate users get through.
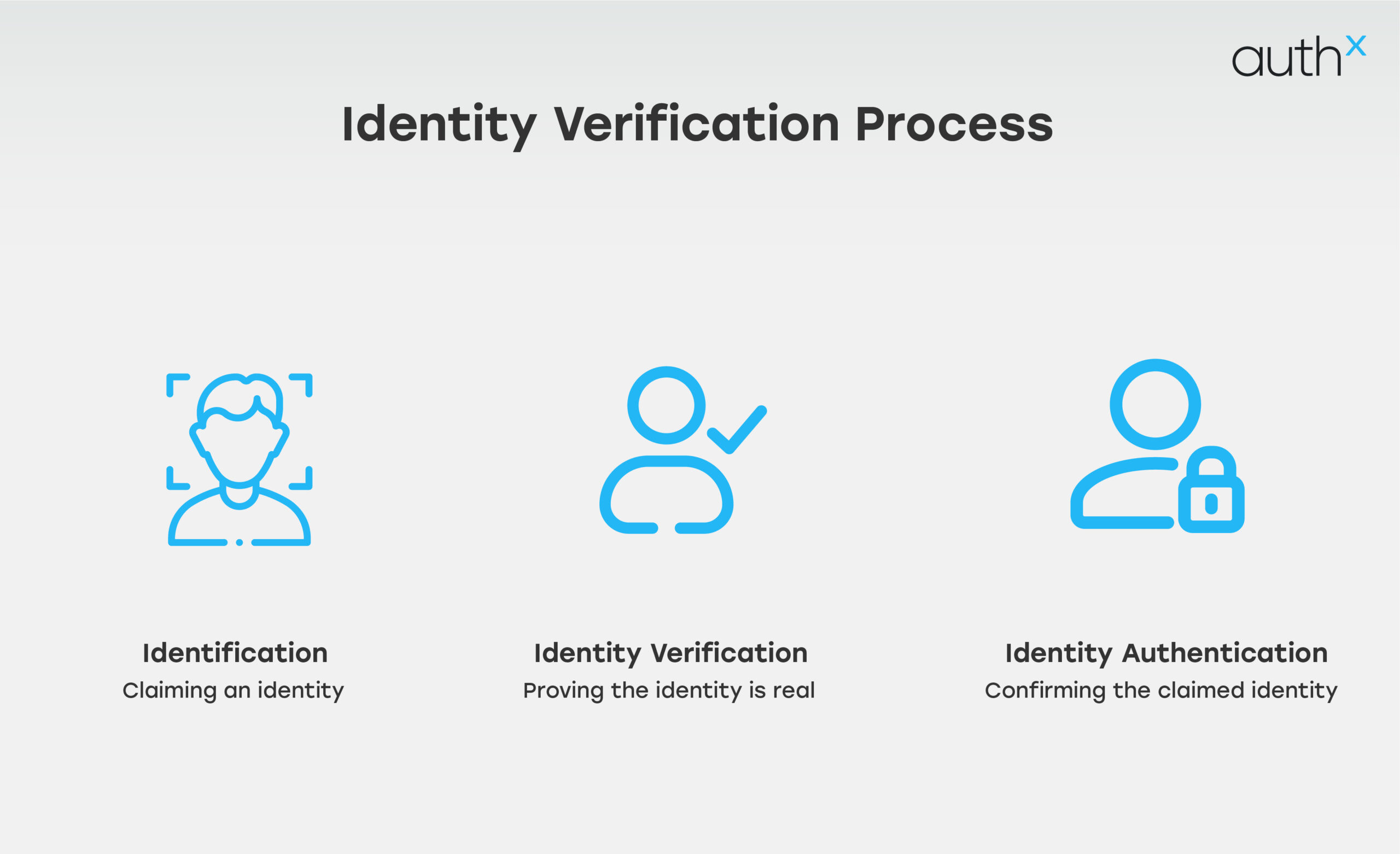
Identity Verification vs. Authentication
People often mix up identity verification and authentication, but they serve different purposes.
- Identity verification happens before access is granted. It checks if the user is a real, verified person.
- Authentication happens after identity verification. It allows a verified user to log in repeatedly.
If identity verification is weak, unauthorized users can slip through the cracks.
Why Identity Verification is Critical?
Most cyberattacks don’t involve brute-force hacking. Instead, they exploit weak identity controls. According to Verizon Data Breach Report, over 80% of breaches involve stolen or weak credentials . Without strong identity verification, organizations remain vulnerable to:
- Phishing attacks – Attackers steal passwords and MFA codes to impersonate users.
- Fake account creation – Fraudsters create synthetic identities to commit financial fraud.
- Insider threats – Employees or contractors access data they shouldn’t.
Traditional security methods like passwords and knowledge-based authentication (KBA) questions are failing. Attackers easily bypass them with social engineering, credential stuffing, and deepfake technology.
IT leaders commonly say, “We have MFA, so we’re safe.” But MFA alone isn’t enough if an attacker has stolen the credentials and the second factor. The real question is—how do you verify the user’s true identity before granting access?
How AuthX Verify Enhances Identity Verification?
At AuthX, we’ve seen firsthand how weak identity verification leads to security breaches. That’s why we built AuthX Verify, a flexible identity verification solution that fits into existing authentication workflows without disrupting user experience.
Key Features of AuthX Verify:
- Biometric Verification: Facial recognition, fingerprint scanning, or iris detection ensures that only the right person can access systems.
- Document Authentication: Government-issued ID scanning validates identities before onboarding users.
- Risk-Based Verification: Additional verification steps kick in if a login attempt looks suspicious (e.g., an unusual location or device).
- Continuous Identity Verification: Instead of verifying identity once at login, AuthX Verify continuously checks throughout the session.
Real-World Use Cases
Industries with high compliance and security requirements are already moving toward identity verification. Here’s how organizations are using AuthX Verify today:
Healthcare
- Doctors and nurses verify their identity before accessing electronic health records (EHRs).
- Remote telehealth sessions require identity proofing before granting access.
- Hospital staff must verify their identity before prescribing controlled substances.
Finance
- Customers verify their identity during account creation to prevent synthetic fraud.
- High-value transactions require biometric authentication Confirmation instead of just passwords.
- Employees re-verify their identity before accessing sensitive financial systems.
Enterprise Security
- Employees authenticate with biometrics instead of passwords.
- Privileged users re-verify their identity before accessing critical systems.
- Remote workers confirm identity before connecting to VPNs.
The Future of Identity Verification
Identity fraud isn’t going away. Attackers leverage AI, deepfake technology, and stolen biometric data to bypass traditional security controls. Organizations need multi-layered identity verification to stay ahead.
What’s Next?
1. Passwordless Authentication Becomes the Standard
- Passwords remain the weakest link. Biometric and hardware-based authentication are replacing them.
2. AI-Powered Verification Improves Security
- Machine learning can analyze behavioral patterns to detect anomalies and prevent fraud.
3. Regulations Will Demand Stronger Identity Proofing
- Healthcare (HIPAA), Finance (KYC), and government security standards will require continuous identity verification.
A CISO we recently spoke with summed it up perfectly:
“The identity layer is the next big battlefield in cybersecurity. Organizations that fail to verify identities properly will be the easiest targets for attackers.”
Ensuring Trust in Every Login
At AuthX, we believe that identity verification should be built into every authentication process, not just during onboarding but throughout the entire user session.
The days of trusting passwords, security questions, or one-time passcodes are over. Identity verification ensures that only the right users get access, every single time.
Ready to upgrade your security? Let’s talk.
FAQs
What is Rainbow Attack in Cybersecurity?
A Rainbow Attack is when hackers use precomputed hash tables to crack passwords quickly. This method is faster than brute-force attacks but ineffective against salted hashes.
How Does a Rainbow Table Attack Work?
Attackers compare stolen password hashes against a precomputed Rainbow Table. If a match is found, they instantly recover the original password.
How Can You Prevent a Rainbow Table Cyber Security Breach?
Use password salting, strong hashing algorithms, and multi-factor authentication. Moving to passwordless authentication eliminates the risk entirely.
Why Are Rainbow Table Attacks Less Common Today?
Security improvements like salting and modern hashing algorithms have made Rainbow Tables ineffective. However, outdated systems remain vulnerable.