Understanding SCIM: Simplifying User Identity Management Across Cloud App

Managing user identities across cloud apps shouldn’t feel like trying to update every contact in your phone manually—one by one, over and over again. Yet, for many IT teams, that’s exactly what user provisioning looks like—creating, updating, and revoking access across multiple platforms, often with tedious manual processes. If you miss a step, you risk exposing employees to security risks or preventing them from accessing important tools.
This is where SCIM (System for Cross-domain Identity Management) comes in. Think of it as an automatic sync for your organization’s user identities, which streamlines provisioning, reduces errors, and makes life easier for IT personnel. But what is SCIM, and why should your organization care? Let us break it down.
What is SCIM?
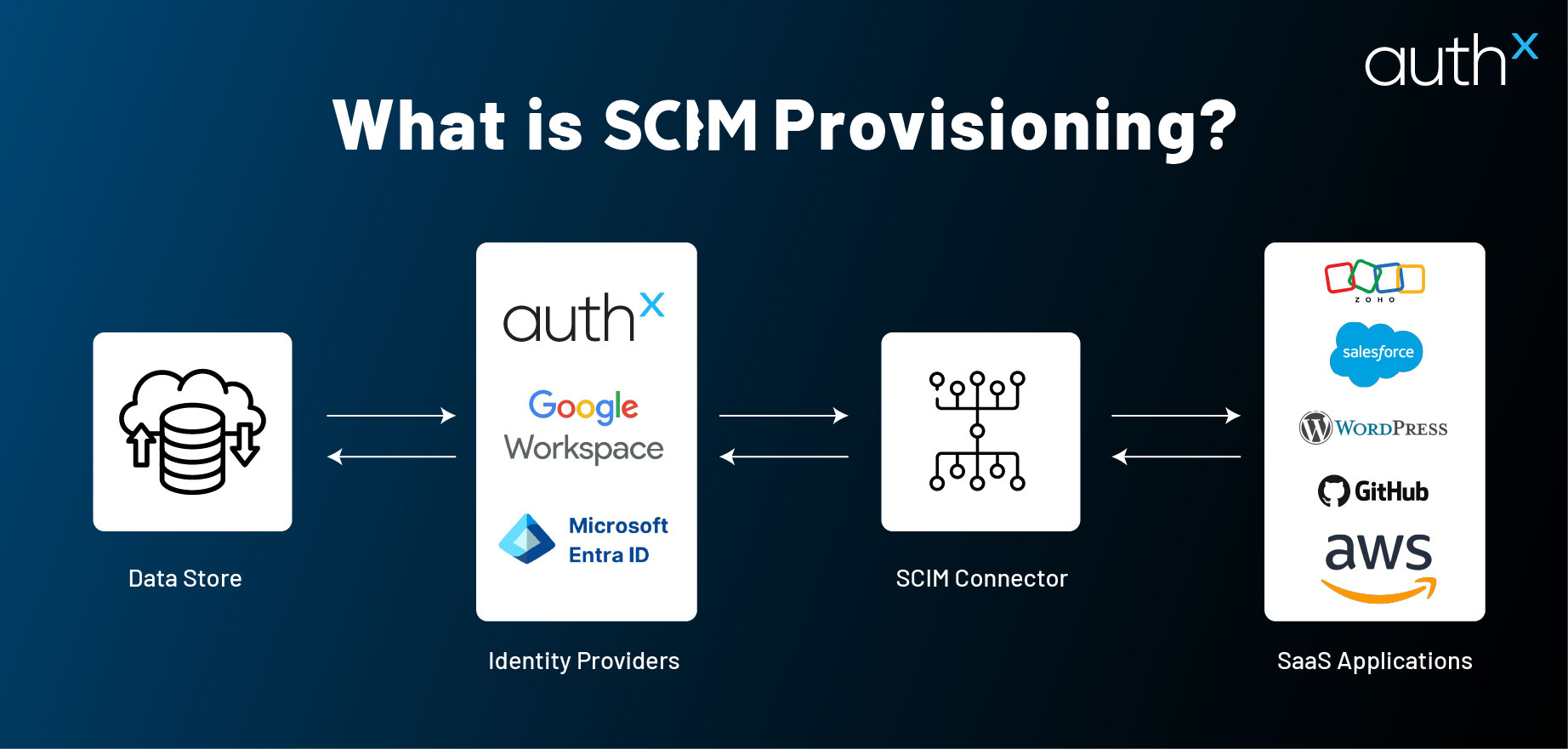
SCIM stands for System for Cross-domain Identity Management. It is an open standard that simplifies and automates user identity management, particularly in cloud environments. Instead of manually provisioning or deprovisioning accounts, SCIM automates this process, reducing errors and ensuring compliance with security policies.
Without SCIM provisioning, IT teams would need to update every app individually when an employee joins, changes roles, or leaves. That’s an administrative nightmare! SCIM solves this by synchronizing user identity data across all connected systems.
We’ve worked with countless IT teams who struggle with identity sprawl across multiple platforms. Their biggest question? What is SCIM provisioning, and how does it make life easier?
How SCIM Works?
SCIM uses RESTful APIs and JSON to exchange user identity data between systems. Imagine it like a translator that ensures the correct user information flows from one app to another. Hence, your employees or contractors always have the right access to their needed resources.
Here’s how SCIM works in practice:
- Automated Provisioning: When new employees join, SCIM automatically creates their user profile across all connected cloud apps.
- Updates in Real-Time: As roles or permissions change, SCIM ensures those updates are synchronized across platforms.
- Offboarding: When employees leave, SCIM deactivates their accounts, ensuring no unauthorized access.
IT teams often ask, “How does SCIM work, and does it improve security?” The answer is YES. SCIM authentication ensures that only authorized users can access the right tools, reducing the risk of breaches caused by outdated permissions.
Key Benefits of SCIM
The reason organizations are shifting to SCIM provisioning isn’t just automation—it’s security, efficiency, and cost savings.
- Efficiency: SCIM reduces manual work, automating tedious tasks like user creation and deactivation. IT teams can save hours, if not days, by letting SCIM handle identity management.
- Improved Security: SCIM authentication ensures users always have the correct level of access, reducing the risk of unauthorized access due to outdated credentials.
- Cost Savings: With SCIM protocol, businesses eliminate costly, custom-built integrations that require ongoing maintenance.
- Increased Productivity: By employing SCIM to manage user data, IT personnel can concentrate on more strategic projects rather than handling repetitive tasks.
SCIM Use Cases
SCIM is built for efficiency in various scenarios, including new employee onboarding and account deactivation. A few instances of how SCIM can be applied in practical settings are as follows:
- Onboarding: SCIM automatically sets up new hire accounts for all required apps, including cloud storage tools, HR systems, and email. This means there won’t be any hold-ups or delays while getting new hires up to speed.
- Role Changes: Any change in a role, such as promotion or departmental transfer, is instantly reflected in all integrated systems when using SCIM. Imagine the hassles that could be eliminated if there was no longer a need to upgrade every system manually.
- Offboarding: To reduce the risk of security breaches, SCIM ensures that employees’ access to all systems is immediately terminated when they leave.
SCIM vs. Other Protocols: SAML and SSO
You may have heard of SAML vs SCIM or wondered how SCIM SSO fits into the picture. While SCIM, SAML, and SSO (Single Sign-On) all play roles in identity management, they serve different purposes.
| Feature | SCIM (System for Cross-domain Identity Management) | SAML (Security Assertion Markup Language) | SSO (Single Sign-On) |
|---|---|---|---|
| Primary Function | User identity provisioning and lifecycle management | Authentication and authorization | Unified authentication across multiple apps |
| What It Does? | Automates user creation, updates, and deprovisioning | Verifies identity and share authentication data between providers | Allows users to log in once and access multiple systems |
| Key Benefit | Ensures consistent user identity data across cloud apps | Establishes trust between identity providers and service providers | Reduces login fatigue and improves user experience |
| How It Works? | Uses REST APIs and JSON to sync identity data across systems | Uses XML-based assertions for authentication | Uses authentication tokens to grant access to multiple apps |
| Best Used For | Managing user access, permissions, and deprovisioning | Securely logging users into cloud apps without storing passwords | Allowing users to access multiple applications with a single login |
| Works With | Identity providers (IdPs) like Okta, Azure AD, and Google Workspace | Federated authentication protocols and IdPs | Authentication systems that support federated identity |
| Relations to Others | Complement SAML and SSO by keeping user data synchronized | Works with SCIM to ensure authenticated users have up-to-date profiles | Uses SCIM to automate user identity updates across apps |
Integrating SCIM with AuthX
At AuthX, we understand the challenges of managing user access in a cloud-first world. That’s why we’ve made integrating SCIM into our platform easy, allowing seamless user provisioning and de-provisioning across your apps.
Whether you use Microsoft Entra ID (formerly Azure AD) or another identity provider, AuthX ensures your user data stays synchronized, secure, and compliant. Our SCIM authentication capabilities enhance security while reducing the workload for IT teams.
Why SCIM Matters to Your Business?
Implementing SCIM is more than simply efficiency; it’s about allowing your company to expand and scale securely. As more businesses migrate to cloud-based apps, managing user IDs across various platforms becomes increasingly tricky. It’s about enabling productivity and creating an agile IT environment that can keep up with the pace of business. And, we’re seeing more businesses realize that SCIM is essential to their identity management strategy.
Conclusion: SCIM is the Future of Identity Management
As cloud adoption increases, so does the demand for fast, secure, and effective user identity management. SCIM is the solution organizations require to stay ahead of the curve by automating user provisioning, boosting security, and saving money and time.
At AuthX, we are dedicated to simplifying identity management for businesses of all sizes. With SCIM integration, we can help you automate your identity lifecycle, ensuring the organization is safe, scalable, and future-ready.
Are you ready to streamline your user provisioning process? Contact us today to learn how SCIM can transform your identity management strategy.
FAQs
What is SCIM, and why is it important?
SCIM (System for Cross-domain Identity Management) automates user identity management, ensuring accurate data sync, fewer errors, and improved security.
How does SCIM work in an organization?
SCIM uses RESTful APIs and JSON to manage user identity data between identity providers and cloud apps. It automates provisioning, updates, and deprovisioning to streamline access management.
What is SCIM provisioning, and how does it differ from manual provisioning?
SCIM provisioning automates account creation, updates, and deletions across multiple platforms. Unlike manual provisioning, it ensures real-time synchronization, reducing administrative workload.
How does SCIM authentication enhance security?
What is the difference between SAML vs SCIM?
SAML handles authentication, allowing secure logins without storing passwords, while SCIM protocol manages user lifecycles across applications. Together, they enable seamless and secure identity management.
How does SCIM SSO improve user experience?
SCIM SSO lets users log in once to access multiple apps, while SCIM ensures consistent identity data. This reduces login fatigue and automates user provisioning for efficiency.