Honestly, when someone is locked out of their work account, the phrase “forgotten password” is probably the most typical one you’ll hear. However, that is only the beginning in terms of business security. Securing your system involves many tasks, from controlling user access to making sure that only authorized individuals enter (and exit). User provisioning and deprovisioning are therefore relevant.
We have witnessed firsthand how proper execution of these procedures may mean the difference between a security nightmare and a smooth sailing experience. Protecting your entire organization, from the beginning to the end, is more important than simply using strong passwords.
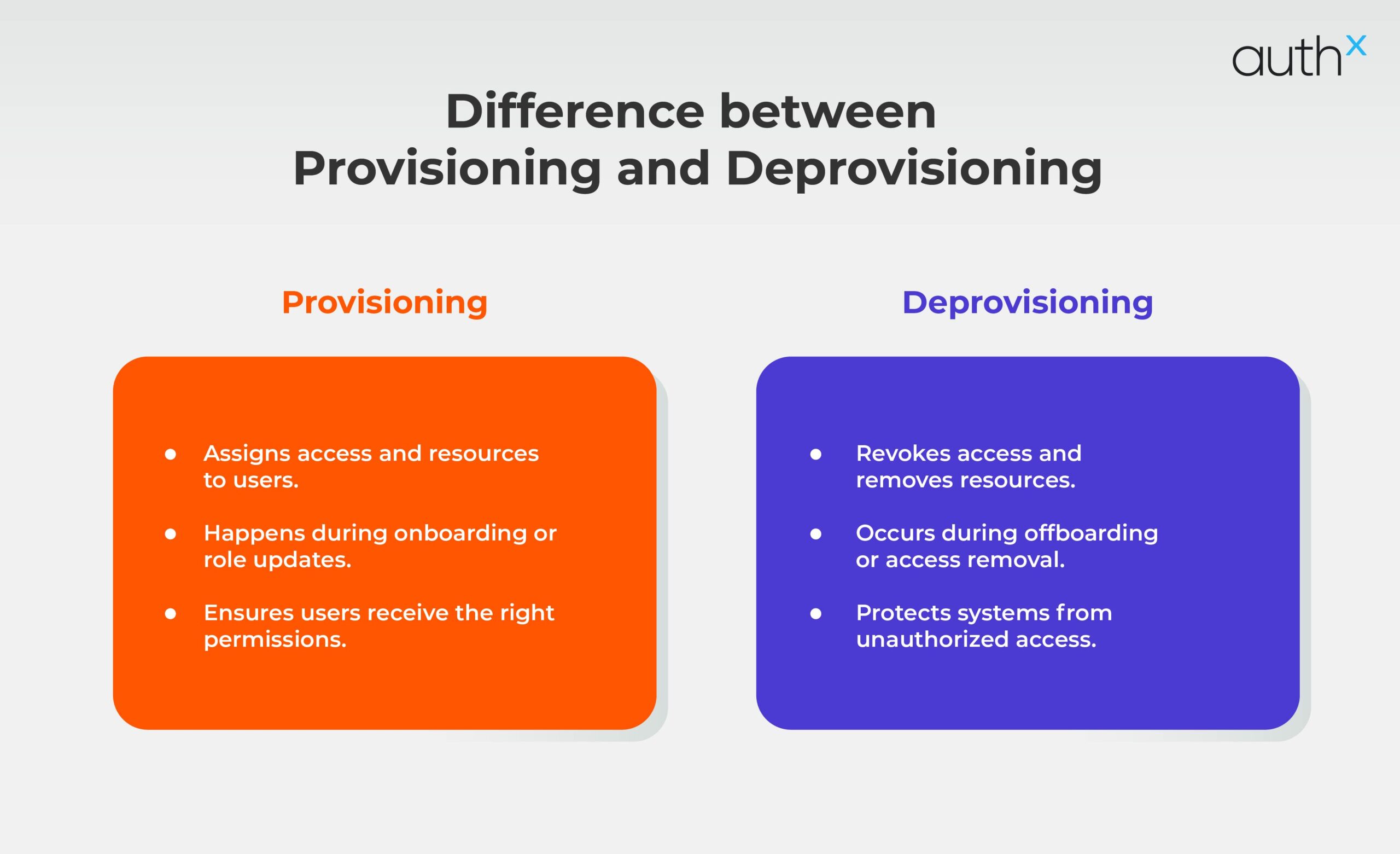
What is User Provisioning?
In simple terms, what is provisioning? It’s providing people access to the tools and apps they require to do their tasks. Consider it as distributing keys to your virtual workspace, guaranteeing that staff members have access to the essential documents, applications, and resources immediately.
And yes, it’s as important as it sounds. But how do you actually do it? Here’s the breakdown:
- Network Provisioning: Configuring and maintaining network resources, including routers, switches, firewalls, and IP addresses, is known as network provisioning. This guarantees smooth communication between devices, servers, and users. In telecommunications, it can include assigning phone numbers or configuring wireless services.
- Server Provisioning: The process of building and setting up virtual or physical servers to meet an organization’s requirements is known as server provisioning. This can involve anything from setting up real hardware in a data center to establishing virtual computers in the cloud.
- Application provisioning: Application provisioning ensures that apps operate smoothly and efficiently by optimizing and configuring them across enterprise settings. It often involves setting aside funds for enterprise solutions such as software-as-a-service (SaaS) tools.
- User Provisioning: Managing digital identities through the creation, modification, and revocation of access to systems, apps, and data is known as user provisioning. It can incorporate procedures like role-based access control (RBAC) and guarantees employees have the right access for their tasks.
- Service provisioning: Service provisioning grants access to IT services while managing credentials and limiting data access as needed. Examples include provisioning access to analytics tools or HR systems.
- Automated provisioning: Automated provisioning takes manual tasks out of the equation, using automation to assign access accurately and quickly. It improves operational efficiency and security by reducing errors and expediting procedures.
To keep IT systems safe and productive, provisioning and deprovisioning are essential processes. Automated provisioning is becoming increasingly crucial for businesses trying to strengthen their security posture and optimize procedures.
What is Deprovisioning?
Now, let’s talk about what is deprovisioning. The word isn’t used to make security sound more difficult. It is only the process of removing access when it is no longer required. Deprovisioning ensures that a user cannot access anything once they leave the firm, change roles, or simply they no longer require access.
Without deprovisioning, you risk leaving “zombie” accounts floating around; users who can still log in even though they shouldn’t. That is a compliance problem in addition to being a security disaster waiting to happen.
Risks of Poor Deprovisioning
Okay, let’s get real. If you don’t manage deprovisioning properly, you’re asking for trouble. Imagine leaving an empty office unlocked at the end of the day and hoping no one comes in. That’s what happens when accounts aren’t deactivated immediately.
If you don’t handle it right, you might end up with:
- Orphaned accounts: Accounts belonging to users who no longer work at the company but still have active credentials.
- Stale privileges: Old permissions hanging around, giving people access they shouldn’t have.
- Unmonitored access: Potential vulnerabilities in your systems.
Best Practices for User Provisioning and Deprovisioning
So how do we fix this? It’s all about the best practice. We know from experience that these little tips make a world of difference.
- Automate: This is your shortcut to efficiency. Automating your provisioning and deprovisioning helps eliminate errors and ensures a consistent process.
- Follow the Principle of Least Privilege: Always grant users only the access they require in accordance with the principle of least privilege. If someone only needs access to the kitchen, it’s like not handing them the keys to your entire office.
- RBAC (Role-Based Access Control): This enables you to designate particular jobs with levels of access. It’s like creating a digital organizational structure that assigns roles.
- Review Permissions Regularly: Remember the sticky note with your password on it? Yeah, you don’t want your permissions hanging around unmonitored for too long either. Regular audits help avoid outdated permissions and security holes.
- Implement MFA: Multi-Factor Authentication (MFA) adds an additional layer of security to critical access points, making it more difficult for unauthorized users to get access.
Benefits of Effective User Provisioning and Deprovisioning
One cannot overstate how crucial it is to manage user provisioning and deprovisioning. Here’s what you stand to gain:
- Security: You can lower the likelihood of unauthorized access and strengthen your security posture as you limit access when it is no longer needed.
- Compliance: With regulations like GDPR and HIPAA becoming more and more important, having efficient access control ensures sure audits don’t catch you off-guard.
- Operational Efficiency: By automating the onboarding and offboarding process, employees can spend less time on manual labor and more time on strategic tasks.
- Cost Savings: Over time, there will be significant cost savings due to fewer errors, security breaches, and downtime.
Automating User Provisioning and Deprovisioning: Why It Matters!
The idea of manually managing thousands of user accounts sounds like a nightmare. Thankfully, automation exists.
Simply put, automation is:
- Efficient: Your team no longer has to spend time on manual provisioning and deprovisioning.
- Secure: Automated systems follow security protocols more consistently than a tired employee ever could.
- Scalable: Whether you’re a startup or a large enterprise, automation grows with you, managing thousands of user accounts without a hitch.
At AuthX, we get it. Scaling your business should never be limited by IAM provisioning and access management. That’s why automation is key.
Integration with Existing Systems
The great news? Don’t abandon your current systems to implement automated user provisioning and deprovisioning. AuthX integrates with your existing Identity and Access Management (IAM) and Single Sign-On (SSO) systems to guarantee uninterrupted processes throughout the entire stack.
Tools and Solutions for User Provisioning and Deprovisioning
So how does AuthX help with all of this? Here’s how we do it:
- Centralized platform: One place to manage everything—no more jumping between different tools and interfaces.
- Automated workflows: We handle SCIM user provisioning and deprovisioning for you, reducing manual errors and speeding up processes.
- Real-time monitoring and alerts: We keep an eye on unauthorized access attempts and policy violations, ensuring your system stays secure.
- Seamless integration: Whether your systems are cloud-based or on-premises, we integrate with them without a hitch.
Common Challenges and How to Overcome Them?
Like any process, user provisioning and deprovisioning come with their challenges. Here are some we often hear about:
- Inefficient provisioning: Slow processes and inconsistent access can bog down productivity.
Solution: Automate it. With AuthX, you get fast, consistent access every time.
- Excessive permissions: Too many privileges create a security risk.
Solution: Use RBAC and conduct regular audits to keep permissions in check.
- Deprovisioning delays: Keeping accounts active when they shouldn’t be is a recipe for disaster.
Solution: We guarantee that access is terminated as soon as someone departs or switches roles by using real-time deprovisioning.
Strategic Insights for Managing User Access
At the end of the day, managing user access isn’t just about following processes—it’s about managing the entire lifecycle of your users. From the moment they’re onboard to when they leave your company, every step matters. And the best way to do this is by integrating security and compliance into your workflows.
Remember, when the provisioning and deprovisioning solutions are solid, you’re not just ticking compliance boxes—you’re giving your business the foundation it needs to scale without compromising security.

