What is Identity Proofing? A Simple Guide to Secure Verification

Ever wondered what stands between you and a cybercriminal trying to steal your identity? It’s not just passwords; it’s identity proofing. In fact, studies show that 70% of weak passwords can be cracked in less than 1 second by hackers using simple brute force attacks, making robust identity proofing essential in safeguarding your data.
We understand that passwords appear to be the best security measure. However, these are only the first step in protecting your Digital identity. Remember the last time your bank called or asked a security question to confirm your identity? This is an example of identity proofing. It guarantees that no one else can access your personal information. In a world full of cyberthreats, identity proofing serves as a digital bouncer to keep malicious individuals out. So, what is the exact structure of it and why does it matter so much to organizations? Let’s get started.
What is Identity Proofing?
Verifying that someone is who they claim to be is known as identity proofing, and it is a key element of digital security. This process involves gathering and verifying proof, such as government-issued identification documents, biometrics, and other private information, to demonstrate a user’s genuine identity. The National Institute of Standards and Technology (NIST) defines two key concepts in this context:
- Claimed Identity: The information a user provides to a system during registration that indicates their claimed identity.
- Actual Identity: The validated data that attests to the user’s actual identity.
Identity proofing is essential for organizations to prevent unauthorized access.
With the growing complexity of digital threats, identity proofing is becoming more and more crucial. With a strong compound annual growth rate (CAGR) of 14.9%, the global identity verification market is expected to nearly double from its 2023 valuation of $10.9 billion to $21.8 billion by 2028. This rise shows how important identity verification is for preventing fraud and protecting online interactions.
Organizations may establish trust and guarantee that only the right individuals have access to critical data by utilizing modern methods like biometrics, AI-driven document verification, and behavioral analysis.
Why Identity Proofing is Crucial?
You might be wondering, “Isn’t a password enough?” Unfortunately, no. Let’s break it down.
Fraud Prevention: Imagine finding that your bank account has been emptied when you wake up one morning. Doesn’t this sound terrible? Proper Identity verification reduces the probability of fraud. It is a proactive measure that guards against identity theft and safeguards private information from exploitation.
Compliance Requirements: Strict privacy laws apply to industries like banking and healthcare. If you break these guidelines, you face the risk of a data breach and serious penalties. We assure you that investing in identity proofing is significantly less costly than paying for non-compliance later.
Financial firms, for instance, have to abide by Know Your Customer (KYC) laws, which demand accurate identity verification. Ensuring compliance requires adhering to the National Institute of Standards and Technology’s (NIST) digital identification requirements (NIST identification Proofing).
Building Trust: The trust of your customers is invaluable. With a solid identity proofing process, they’ll feel confident knowing that their data is protected, building a relationship of trust and reliability.
How Identity Proofing Works?
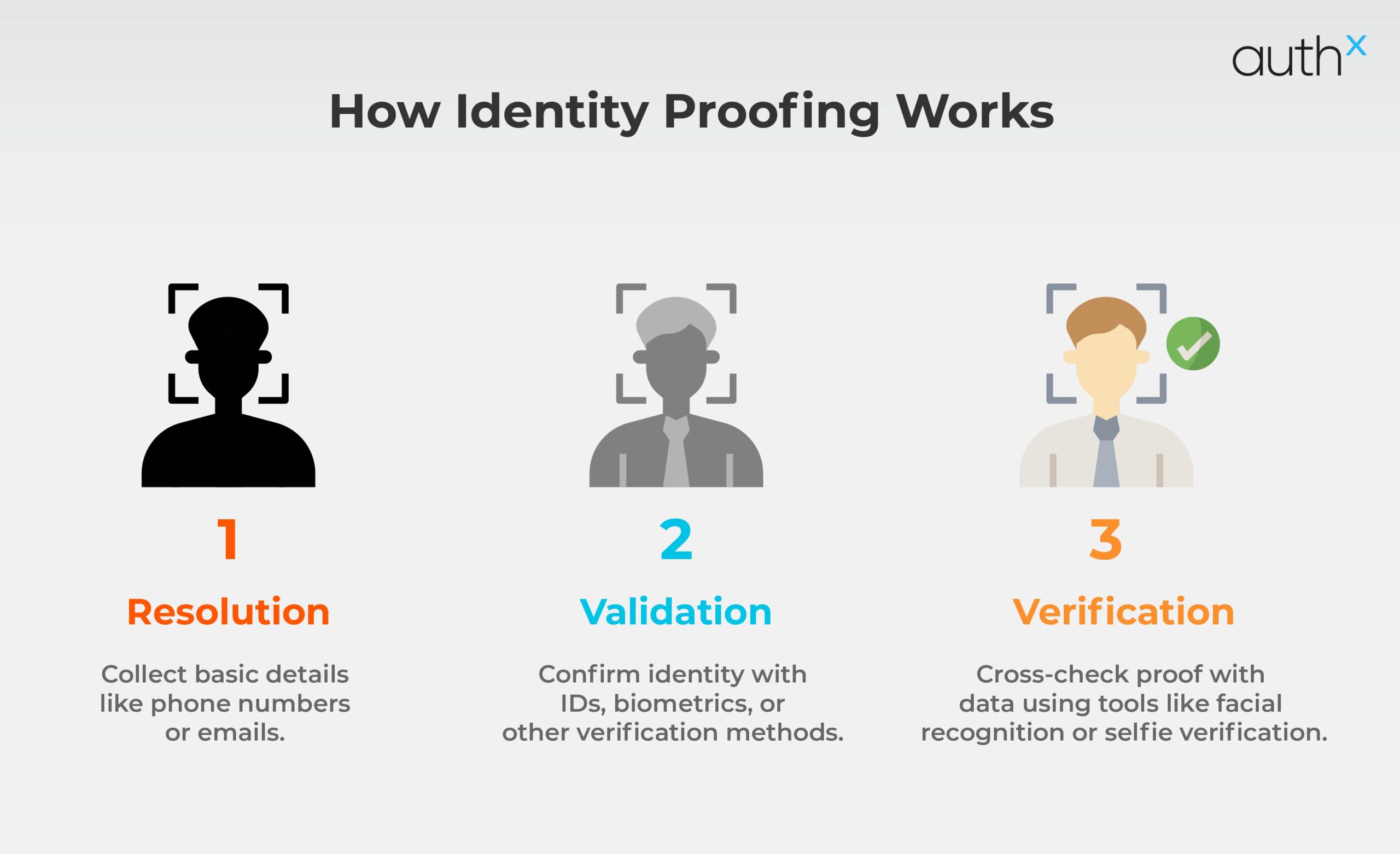
The process might sound complex, but it’s about three simple steps:
Resolution: This is the first stage where the system gathers fundamental identification data, including phone numbers or email addresses.
Validation: The person must prove that they are who they claim to be by using government-issued IDs, biometric scans, or other forms of verification. Strong evidence must be presented.
Verification: To verify that the identity is authentic, the system finally compares the provided proof with existing data (perhaps using liveness detection or facial recognition). For example, the system may ask for a selfie photo to verify the claimed identity.
Modern Identity Proofing Technologies
AI & Algorithms: AI is far more than recommending your next show on Netflix. Additionally, it gains intelligence over time by learning from every encounter and identifying security threats such as fraudulent attempts and phony identification documents.
Biometrics: Despite the fact that they might sound like something from a science fiction movie, Biometric authentication is getting more and more popular. Fingerprints and facial recognition assist in confirming that you are the person logging in.
Liveness Detection: This is one of the most innovative advancements in identification verification. It ensures that the individual being validated is present and isn’t attempting to use a photo to trick the system.
Key Use Cases of Identity Proofing
Now let’s discuss real-world implications. Identity proofing isn’t limited to government organizations or large financial institutions. Various industries use it to protect sensitive data:
Finance: Identity verification can assist stop fraudulent transactions for costly purchases or returns in e-commerce.
Healthcare: With the rise in popularity of telemedicine, it is more important than ever to confirm that the person you are dealing with is your doctor or patient.
E-commerce: Identity verification can help prevent fraudulent transactions for expensive purchases or returns.
Workforce Solutions: Maintaining internal security involves making sure that employees are who they claim to be for things like access control and onboarding.
Identity Proofing vs Identity Verification
Identity Proofing vs. Identity Verification are two terms that are frequently used when talking about the process of ensuring secure access to systems. Although both are essential for protecting user identities, they have different functions and take place at different phases.
| Aspect | Identity Proofing | Identity Verification |
|---|---|---|
| Purpose | Confirms that the user is who they claim to be. | Validates the authenticity of the identity proof provided. |
| Stage in the Process | Occurs at the initial stage when a user first interacts with a system. | Happens after identity proofing, to confirm the user's actual identity. |
| Methods Used | Biometric scans, document verification, knowledge-based authentication. | Verifies identity documents, uses multi-factor authentication, and biometrics. |
| Usage | Used during onboarding or for new customer registrations to establish identity. | Used for transactional activities or when accessing sensitive information. |
| Security Level | Provides the first layer of defense by proving the claimed identity. | Ensures the authenticity of the identity and adds an additional security layer. |
| Example | Document verification, selfie photo, biometric verification. | Liveness detection, facial recognition, two-factor authentication. |
Compliance Considerations
Here’s the reality: compliance isn’t something you can just ignore. Whether it’s NIST standards or GDPR, there are levels of identity proofing required depending on the data you’re handling.
- Level 1: No identity proofing
- Level 2: Basic proofing (e.g., document verification)
- Level 3: Comprehensive verification, including biometrics and multi-factor authentication
Meeting compliance is critical—not just to avoid fines, but to maintain user trust.
Challenges in Identity Proofing
Let’s be honest: it’s not all smooth sailing. One significant challenge? Balancing security and user experience. Too many verification processes can annoy users and result in abandoned sign-ups. And, as evolved as AI is, it isn’t perfect. Fraud attempts may still slip through the loopholes. But that’s where continuous improvement comes in—AI systems that learn and evolve with every interaction.
Benefits of Identity Proofing
When you get it right, the rewards are clear:
Enhanced Security: Keep cybercriminals at bay and protect your business from unauthorized access.
User Trust: Customers want to know their data is safe. A good identity proofing system assures them that it is.
Regulatory Compliance: Avoid hefty fines by staying compliant with global standards.
Operational Efficiency: Automate the verification process, reducing human error and streamlining workflows.
Future of Identity Proofing
The future of identity proofing? It’s only getting smarter. AI-driven systems will one day recognize subtle signs of fraud, even understanding behavior patterns to detect threats before they happen. Blockchain and other emerging technologies will be essential in establishing tamper-proof digital identities and ensuring a secure, decentralized verification procedure. Furthermore, even more accuracy and security will be offered by developments in biometric systems like behavioral biometrics and voice recognition.
Identity proofing will emerge to smoothly interact with IoT devices as industries shift toward a more digital-first strategy, allowing for safe identity verification across interconnected platforms. The focus will not just be on enhanced security but also on delivering frictionless user experience.
Choosing the Right Identity Proofing Solution
When picking an identity proofing solution, ask yourself: What’s most important to you? User experience, compliance, or both? Our advice: go for a solution that’s scalable and balances security with ease of use. At AuthX, we provide that sweet spot—advanced biometric solutions, seamless integration, passwordless authentication and systems that are fully compliance-ready.
Conclusion
Identity verification is not an option; it is an essential requirement. From preventing fraud to maintaining compliance and user confidence, it’s an essential component of protecting your digital ecosystem. Get in touch with us if you’re keen to improve your identity proofing game. At AuthX, we’re here to help you streamline the process and remain on top of both security and user experience trends.
FAQs
What is a method for confirming users' identities?
Methods like facial recognition, fingerprint scanning, and document verification are commonly used, with AI specifically aiding in detecting fake IDs and ensuring liveness during biometric checks.
How does remote identity proofing work?
Remote identity proofing is the process of verifying a person’s identity without needing to be physically present using secure methods like document verification, biometric scanning, and facial recognition.
What is the difference between identity proofing and authentication?
Identity Proofing verifies the user’s claimed identity during the initial setup using methods like biometrics. Authentication confirms identity later through credentials such as passwords or multi-factor authentication.