We’ve all been there. You settle at your desk, ready to take on the day, only to encounter the dreaded password prompt. You are about to enter your password but hold on! Did it start with a number or a capital letter? What about that weird symbol at the end? The email requesting a password reset suddenly feels like a personal attack. Does this sound familiar?
In a constantly evolving digital world, passwords are rapidly becoming the weakest link in the security chain. Single Sign-On (SSO) and Multi-Factor Authentication (MFA) are like two superheroes saving the day. Both provide methods to secure access to your company’s systems while making life easier for your team members. But what is SSO and what is MFA? More importantly, how do they benefit cybersecurity, and where does SSO vs MFA come into play for your organization? Let’s break it down.
What is SSO?
Convenience is the primary focus of Single Sign-On (SSO). Imagine this: All your linked apps are accessible after just one login, saving you from having to re-enter your login credentials every time. This is the magic of SSO. Having worked extensively with enterprise IT teams, we can attest to the time and energy SSO can save. It’s particularly helpful to organizations that use multiple types of cloud-based apps, allowing employees to access everything from emails to document management tools with just one login.
But here’s the catch: SSO also introduces a potential vulnerability. If your single set of credentials is compromised, all connected applications could be at risk. So, while SSO streamlines access, businesses must remain vigilant about protecting that one set of credentials.
What is MFA?
Essentially, Multi-Factor Authentication requires more than simply a password to access an account. You are asked to prove your identity using two or more factors to add an extra layer of security. These factors can include:
- Something you know: A password or PIN.
- Something you have: A physical device, such as a smartphone or security token.
- Something you are: Biometrics like fingerprints or facial recognition.
- Somewhere you are: IP Address based location check.
MFA is an excellent approach to strengthen security, especially for apps that handle sensitive information. For example, it is common to use a password in addition to a one-time passcode sent to your phone while logging into online banking. This “something you have” element makes it much more difficult for unauthorized users to gain access, even if they can find out your password.
Despite MFA’s effectiveness as a security precaution, it’s crucial to keep in mind that no system is perfect. As security professionals frequently state, reducing the damage of a breach is something we can do, and we should do, instead of trying to prevent every attack, which is challenging.
Types of SSO
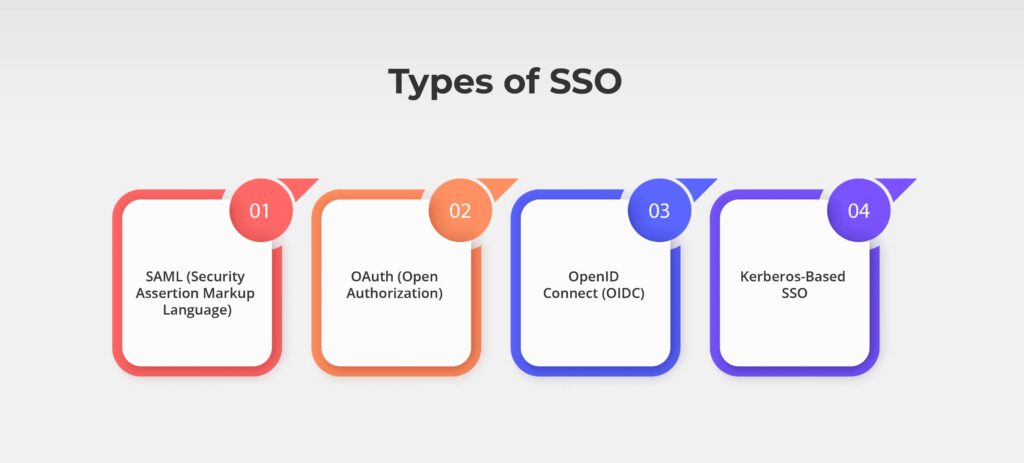
Types of SSO refer to the various methods used to simplify and secure user access by centralizing authentication, utilizing different protocols and technologies to fit specific use cases:
- SAML (Security Assertion Markup Language)
A widely adopted protocol that enables secure, seamless authentication across web applications, ideal for enterprise use cases. - OAuth (Open Authorization)
Allows secure access delegation without sharing credentials, commonly used for social logins or third-party app integrations. - OpenID Connect (OIDC)
An identity layer built on OAuth 2.0, offering enhanced user identity verification and compatibility with modern applications. - Kerberos-Based SSO
Relies on ticket-based authentication for secure and efficient access in internal networks, often used in enterprise and government systems.
Types of MFA
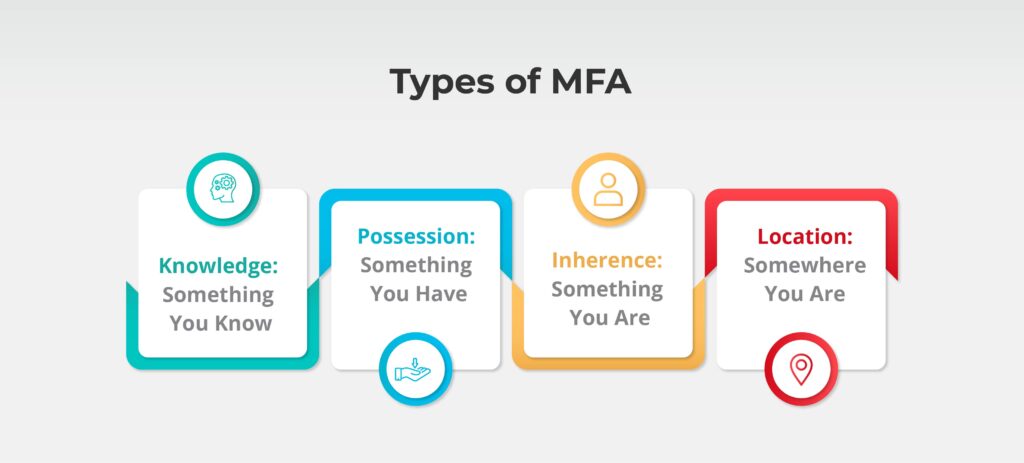
Multi-Factor Authentication (MFA) is categorized into four main types of authentication factors, each ensuring secure access based on different principles:
1. Knowledge: Something You Know
Knowledge-based authentication relies on information that only the user should know.
Examples:
- Security questions with secret answers
- Passwords and PINs
2. Possession: Something You Have
Possession-based authentication verifies identity through a physical object in the user’s possession.
Examples:
- Physical Tokens: Hardware devices like USB security keys or smart cards
- Push Notifications: Real-time prompts sent to a user’s mobile device
- SMS or Email Codes: Verification codes sent via text or email
3. Inherence: Something You Are
Inherence-based authentication uses the user’s unique physical or behavioral traits for verification.
Examples:
- Biometric Verification: Fingerprint scans, facial recognition, or iris scans.
4. Location: Somewhere You Are
Location-based authentication validates identity based on the user’s physical location.
Examples:
- IP address-based location checks
- Access restricted to specific geographic areas
By leveraging a combination of these authentication types, organizations can tailor their security measures to match specific use cases and risk levels while balancing user convenience and robust protection.
Benefits of SSO
Understanding the benefits of SSO simplifies access and enhances efficiency.
- Simplified Access Across Applications: SSO eliminates the need for numerous login credentials by enabling users to access multiple applications after logging in once.
- Reduced Login Interruptions: SSO minimizes the need for multiple logins. It leads to improved user experience and reduced workflow interruptions.
- Improved User Productivity: By removing password-related problems, SSO frees up users’ time so they can focus on their work.
- Lower IT Support Costs: With fewer login issues, helpdesk requests for password resets are reduced. This saves the IT teams’ time and resources.
- Enhanced Security with Centralized Control: By centralizing authentication, SSO streamlines security management and facilitates access policy monitoring and enforcement.
Benefits of MFA
Understanding the benefits of MFA is crucial for modern security strategies.
- Enhanced Protection Against Unauthorized Access: MFA adds an extra layer of security by requiring multiple factors to verify identity, significantly reducing the risk of unauthorized logins.
- Reduced Risk of Credential-Based Attacks: Even if a password is compromised, additional authentication factors like biometrics or tokens prevent unauthorized access.
- Improved Compliance with Security Regulations: MFA helps meet data protection standards like GDPR and HIPAA, ensuring organizations remain compliant with regulatory requirements.
- Flexible Authentication Methods: MFA offers multiple verification options, including biometrics, push notifications, and physical tokens, catering to diverse security needs.
- Stronger Security for Remote Access: For remote and hybrid workforces, MFA ensures secure access to systems, protecting sensitive data from external threats.
SSO vs MFA: Comparing the Two
Here’s where the real decision-making starts. SSO and MFA each serve a distinct purpose, but they’re not mutually exclusive. In fact, using both together can deliver the best of both worlds: convenience and security.
Here’s a comprehensive comparison table:
| Aspect | Single Sign-On (SSO) | Multi-Factor Authentication (MFA) |
|---|---|---|
| Definition | Allows access to multiple apps with one login. | Verifies identity using two or more factors. |
| Purpose | Simplifies logins and reduces password fatigue. | Strengthens account security. |
| Key Benefit | Boosts user convenience and productivity. | Protects against unauthorized access. |
| Use Cases | Best for frequent access to multiple apps. | Ideal for securing sensitive data and meeting compliance. |
| Primary Focus | Convenience: Streamlined access to apps. | Security: Adds layers of protection. |
| Authentication Process | Single login grants access to all connected apps. | Requires two or more authentication steps (e.g., password + biometric + RFID badge). |
| Security Level | Medium: Relies on secure credential storage. | High: Even if one factor is compromised, others protect access. |
| User Experience | Fast and easy, with fewer interruptions. | Convenient and intuitive, especially with passwordless MFA. |
| Implementation | Easier to set up with compatible apps. | More complex, requiring additional hardware/software. |
| Compatibility | Works with apps using protocols like SAML or OAuth. | Supports most systems and devices. |
| Risk Mitigation | Reduces password reuse but creates a single point of failure if breached. | Limits risk, even if one factor is compromised. |
| Cost | Licensing for SSO providers but saves on password management. | Additional costs for devices or software. |
| Compliance Support | Supports access control compliance. | Essential for meeting security regulations like GDPR or HIPAA. |
| Examples | - Access all Microsoft 365 apps with one login. - Use one login for Google Workspace. |
- Password + fingerprint for banking apps. - Password + push notification for system login. |
When comparing SSO vs MFA, we often suggest thinking of SSO as the front door to your applications and MFA as the security system around that door. It’s about reducing friction without compromising on protection.
When to Use SSO?
SSO is ideal in environments where user convenience and efficiency are priorities. Organizations with employees accessing multiple systems daily—like CRM tools, project management platforms, and collaboration apps—benefit significantly. By centralizing access, SSO reduces time spent on password resets, allowing employees to focus on their tasks and improving overall productivity. However, in the SSO vs MFA equation, security-sensitive environments should still layer MFA on top.
For instance, a global retail chain with hundreds of employees using various inventory and sales platforms could simplify workflows with SSO, minimizing login disruptions. Educational institutions managing multiple student and faculty platforms can also leverage SSO for smoother access. With fewer credentials to manage, IT teams spend less time on support tickets related to password recovery. Additionally, SSO promotes security by reducing password fatigue, which often leads to weaker password practices
When to Use MFA?
MFA is essential for businesses handling sensitive or high-risk data, such as financial, healthcare, or government organizations. It adds a critical layer of security, safeguarding data and protecting against unauthorized access. Beyond data protection, MFA fosters trust by ensuring customers and stakeholders that their information is secure. Yet, MFA alone may slow workflows, which is why pairing it with SSO often resolves the SSO vs MFA conundrum.
Consider an e-commerce platform integrating MFA to protect user accounts from fraud during online transactions. Similarly, a hospital system can implement MFA to secure patient data while allowing doctors to access records securely from various devices. Remote work environments with employees accessing company resources from multiple locations also benefit greatly from MFA. By combining convenience with strong security, MFA helps organizations meet compliance requirements and mitigate risks.
Combining SSO and MFA
In many cases, the real magic happens when you combine SSO and MFA. This two-pronged approach allows businesses to streamline access to applications while ensuring strong security. Adding MFA on top of SSO mitigates the risk of a compromised password by requiring additional verification factors.
Think of this as a layered security model. By combining the simplicity of SSO with the protection of MFA, you get a seamless experience that doesn’t sacrifice security for convenience.
Implementation Tips
So, how do you get started? Here are a few practical tips I recommend to businesses I work with:
- Evaluate your needs: Not all apps need the same level of protection. High-risk applications (such as financial systems) should emphasize MFA, whereas low-risk apps may benefit from SSO.
- Start small: If you’re new to MFA or SSO, consider implementing the solution gradually. Begin with high-priority users or systems before expanding.
- Choose the right solution: Look for MFA and SSO solutions that integrate smoothly with your existing infrastructure and enable scalability for future growth.
- Educate your users: Proper training is crucial. Ensure your team understands how MFA works and why it’s important.
- Prioritize compatibility: Ensure the solution works seamlessly with your technology stack, including platforms like Citrix, IGEL, and other key systems.
Final Thoughts
The SSO vs MFA debate isn’t about choosing sides—it’s about leveraging their strengths together in your organization’s IAM strategy. Together, they offer the perfect blend of convenience and protection, ensuring your business stays secure without compromising user experience.
Security does not have to slow you down. Together, MFA and SSO make access easier while protecting your digital assets. Whether it’s reducing login times with SSO or enhancing security with MFA, the combination ensures that your team can focus on what really matters.
Ready to enhance both security and productivity? Explore how AuthX’s integrated solutions can help you implement MFA and SSO effortlessly tailored to fit your unique business needs.


