Step-Up Authentication Demystified: A Path to Smarter Access

Introduction
In today’s robust digital world, maintaining account security and managing sensitive data is exceptionally challenging than before. The estimated cybercrime across the globe is predicted to reach $10.5 trillion annually by 2025. Cyber-attacks are becoming more complex, and businesses need to protect data without hampering user experience.
Step-up authentication is an effective solution to this issue as it adds an additional security when users perform critical actions. This extra verification step ensures the right person is accessing the information. However, excessive verification can frustrate users, as 86% of customers are less likely to return to a service with poor login experiences. Adaptive authentication reduces unnecessary hurdles by adjusting security levels based on risk. In this blog, let’s explore how to implement step-up authentication effectively while maintaining a seamless user experience.
What Is Step-Up Authentication?
Step-up authentication is a dynamic security process designed to match the level of identity verification to the risk associated with an action or resource being accessed. Rather than applying the same authentication requirements for every action, it triggers additional steps only when the risk level is higher.
For example, users may be asked for extra verification when making a high-risk transaction or accessing critical data. This maintains a balance between security and user-ease. Cybercriminals are exploiting credentials from data breaches and phishing scams. Lesser authentication leads to easy cyberattack, and too many authentications for each login can be a very frustrating experience. Strong security is pretty much necessary, and equally important that organizations don’t make the authentication process a hassle for users.
Wondering how to strike a perfect balance between seamless security and user experience?
Effective implementation is key: poorly designed systems can expose businesses to significant risks and this vulnerability allowed hackers to exploit the system and steal millions of details. The strength of step-up authentication lies in ease of use, considering contextual triggers as the nature of the activity, the user’s behavior, and the value of the asset are being accessed. By using step-up authentication, organizations can protect their systems and data without unnecessarily burdening users. The goal is to maintain a simple, intuitive security process, only invoking additional checks when truly needed.
Step-Up Authentication vs. Multi-Factor Authentication vs. Adaptive Authentication
| Feature | Step-up Authentication | Multi-Factor Authentication (MFA) | Adaptive Authentication |
|---|---|---|---|
| Definition | Adds an extra verification step for high-risk actions after initial authentication. | Requires multiple forms of identification (e.g., password, OTP) to access an account. | Dynamically adjusts authentication requirements based on real-time risk factors. |
| When It Is Applied | Triggered by specific actions that involve accessing sensitive data or performing risky tasks. | Applied during the login process, typically requiring two or more factors of authentication. | Continuously evaluates user behavior and adjusts security measures based on context. |
| Authentication Methods | Additional methods like OTP, biometrics, or security keys after the initial login. | Common methods include passwords, OTPs, biometrics, or security tokens at login. | Uses contextual data such as IP address, device, geolocation, and user behavior for risk assessment. |
| Scope | Focused on securing high-risk actions after an initial login. | Ensures secure login by requiring multiple authentication factors upfront. | Context-aware, adjusts security based on factors like location, device, or unusual activity. |
| Risk Evaluation | Evaluated based on the action being performed (e.g., accessing sensitive data). | No real-time risk assessment; MFA is typically applied at login to verify user identity. | Continuously assesses risk in real-time and adapts authentication requirements dynamically. |
| Flexibility | Less flexible; triggered by predefined high-risk actions. | Fixed requirements at the time of login, typically not adjusted dynamically. | Highly flexible; adjusts security requirements in real-time based on risk level. |
When Should You Use Step-Up Authentication?
Effective step-up authentication strikes a balance between user convenience and security, especially for sensitive data. It’s most valuable when the risk of exposure is high or when additional verification is needed for certain actions. Here are key scenarios:
1. When Users Need Access to High-Risk Resources
Not all data require constant high-level security while accessing. When users need to access high-risk, step-up authentication ensures to verify the person’s identity.
2. When Users Want to Interact with Sensitive Data
Organizations can manage both non-sensitive and sensitive data by using step-up authentication. Employees can access non-sensitive data with a basic login but will be prompted for additional authentication when accessing sensitive data, ensuring protection even if credentials are compromised.
3. When Privileging Access for Paying Users
Step-up authentication is commonly used in subscription models, where free users access limited content and paying users get full access. For example, sites like *The New York Times* allow free article views, then prompt for login or subscription to access premium content, enhancing security and encouraging conversions.
4. When Sensitive Actions Are Performed
High-risk actions, like transferring funds, modifying account settings, or accessing sensitive data, should trigger step-up authentication. For instance, employees making changes to a production environment or GitHub repository should undergo additional verification to ensure authorization.
5. To Differentiate Between Free and Paid Users
Step-up authentication helps control access to features based on user subscriptions. In SaaS products, free users access basic features, while premium users unlock more. This ensures only authorized users can access higher-tier features, helping organizations manage resources.
6. When Action May Involve Irreversible or Sensitive Changes
If users are performing actions that might have irreversible consequences or could potentially harm the system or organization, step-up authentication provides an extra layer of protection.
7. To Limit Access to Sensitive Information
Step-up authentication allows for more close control over who can access different data. Employees can use standard credentials to access non-sensitive data of the system, but when they try to access sensitive data step-up authentication can be initiated.
8. When Users Expect Security for High-Risk Transactions
For certain high-risk activities, users themselves expect additional security checks. For example, when changing account passwords or updating payment information, users understand the need for extra verification to protect their sensitive data. Step-up authentication in these cases provides both security and user assurance.
9. When Reducing MFA Fatigue
In conditions where multi-factor authentication (MFA) is required for every login or action, users may find it frustrating or decrease engagement. Step-up authentication helps reduce this situation by applying additional authentication only, when necessary, for higher-risk actions or resources, without burdening users.
Examples of Step-Up Authentication in Action
Step-up authentication is a popular security measure that balances user convenience with enhanced protection of sensitive data. Here are real-world examples of its use across industries to secure high-risk actions and resources:
Step-Up Authentication in Financial Services
- Banking Apps: Users can log in with biometric authentication to view balances or transactions but are prompted for additional security when transferring funds.
- Online Banking: Banks require step-up authentication for sensitive actions, like changing account settings or adding payees, after the initial login.
Step-Up Authentication in E-Commerce and Retail
- Online Shopping: Customers can browse and check rewards with basic login, but for significant actions like making big purchases or changing shipping details, they are prompted for additional authentication, such as an OTP or email verification.
- Account Changes: When updating payment methods or personal details, step-up authentication ensures only the legitimate user can make these changes, preventing unauthorized access.
Step-Up Authentication in Healthcare
- Patient Portals: Authorities can access basic information with a password but are prompted for additional verification to view sensitive data like health reports or medications.
- Healthcare Professional Access: Medical staff may undergo step-up authentication, such as biometric scans, when accessing or modifying patient records to ensure compliance with security policies.
Step-Up Authentication in Online Services and Subscriptions
- Content Websites: Platforms like *The New York Times* allow limited access to content but prompt for login or subscription once users hit the paywall. Subscribers may then be asked for additional verification, such as SMS or email confirmation, to access premium articles.
- Streaming Services: Paid platforms use step-up authentication when users upgrade accounts, change payment methods, or access exclusive content, often requiring a one-time code or third-party verification.
Step-Up Authentication in Enterprise and Business Applications
- Code Repositories: Employees can access public repositories with basic authentication but must undergo step-up authentication to commit changes or modify production code.
- Internal Systems Access: Employees can access general resources with regular credentials but are prompted for additional verification before viewing sensitive data or making significant changes.
Other Step-Up Authentication Use Cases
Step-up authentication enhances security in the following scenarios:
- Repeated Incorrect Login Attempts: If a user repeatedly enters wrong credentials, step-up authentication verifies their identity through additional methods.
- Logins from Unusual Locations: When logging in from a new location, step-up authentication prompts for extra verification to confirm identity.
- Sensitive Transactions: For high-risk actions like money transfers or security changes, step-up authentication ensures the transaction is authorized by requiring an additional authentication method.
How to Implement Step-Up Authentication?
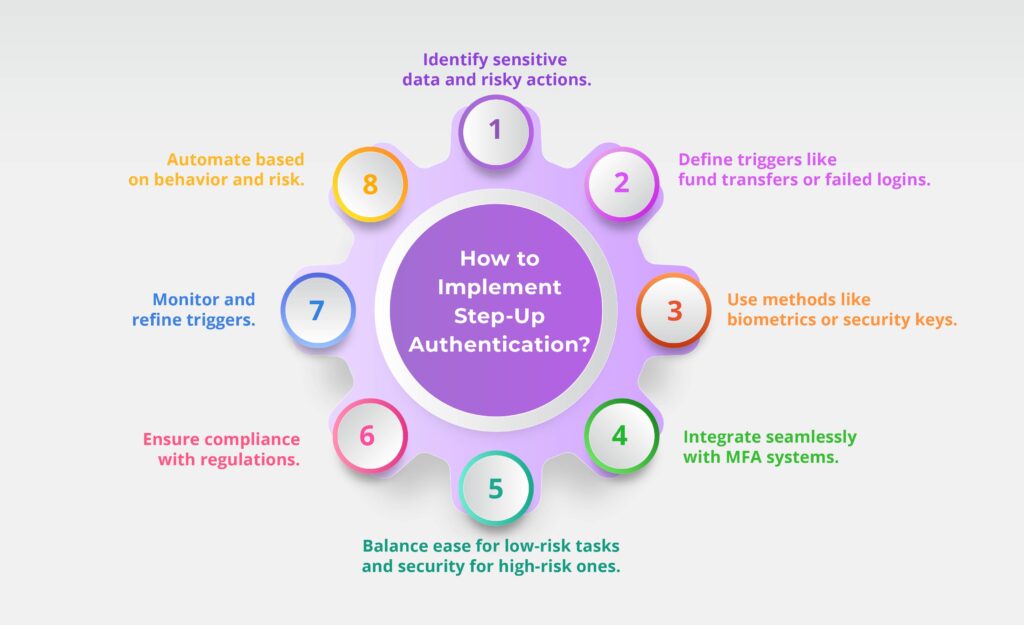
1. Assess Risk and Identify Key Scenarios
- Determine what resources are most sensitive such as financial information, health records, or proprietary data, and need additional security measures.
- Identify which actions carry higher risks, such as transferring funds, changing user account details, or accessing privileged data. These should trigger step-up authentication.
- Consider potential user behaviors that might indicate suspicious or risky activity, such as login attempts from new locations or multiple failed login attempts.
2. Determine Triggering Events
- A minor action can lead to financial loss, such as transferring money, changing payment methods, or accessing high-value assets.
- Logging from an unfamiliar device or connection could trigger an additional authentication layer.
- Multiple failed login attempts indicate a brute-force attack, prompting the system to ask for extra verification.
3. Select the Appropriate Authentication Methods
- A one-time code to the user to verify their identity.
- Biometric authentication to confirm the user’s identity.
- Implement security keys or app-based authentication for higher-risk actions.
- Although less secure than others, security questions can be a backup method for less sensitive cases.
4. Implement Step-Up Authentication into Your Existing System
- If you’re already using MFA, make sure the step-up authentication fits naturally into your existing user login process.
- Use a system, which allows you to customize when step-up authentication is triggered based on various risk indicators. For example, Authentication can monitor for unusual login patterns or behavior, and automatically request additional authentication when necessary.
- Ensure that the step-up authentication flow is intuitive and seamless. If users are prompted for additional credentials, the process should be easy to follow, and the steps should be clear.
5. Balance Security with User Experience
- Keep the process simple for users accessing non-sensitive resources. For instance, logging in to view account balances can be done with just a password or biometric scan.
- Requires additional authentication only when users perform actions like transferring money, accessing sensitive documents, or changing personal details.
6. Ensure Compliance with Regulatory Standards
- HIPAA (Healthcare): Protect sensitive patient’s information by requiring additional authentication for activities like accessing medical reports and medication.
- GDPR (General Data Protection Regulation): Ensures that sensitive data is only accessible by authorized individuals, which may require step-up authentication to access, edit, or delete information.
- PCI-DSS (Payment Card Industry Data Security Standard): For financial apps, setting up payment transactions and access to cards and customer’s data are protected with step-up authentication.
7. Monitor and Adjust for Effectiveness
- Use analytics to understand how users are interacting with the step-up authentication flow. Are they dropping off during additional authentication prompts? Is there any confusion or frustration?
- If users are repeatedly prompted for additional authentication, modify the events to ensure that step-up authentication is only invoked for high-risk actions.
- Conducting regular security audits to identify vulnerabilities and ensure that the system is effectively prevented.
8. Use a Reliable Identity Management System
- Authentication that allows you to customize rules based on user behaviour, risk profiles, and security needs. For instance, Authentication can automatically trigger additional authentication based on user location, device, or suspicious behaviour patterns, making the process more dynamic and responsive.
Conclusion
Step-up authentication is an essential security measure that balances user convenience with robust data protection. Adding an extra layer of verification only when accessing high-risk actions or sensitive data, ensuring a seamless experience for low-risk tasks while securing necessary actions. Whether in finance, e-commerce, healthcare, or corporate environments, step-up authentication adapts to the threat level, maintaining an ideal balance between usability and protection. When integrated with advanced tools like AuthX, businesses can enhance their security posture and provide adaptive, real-time protection.
AuthX makes it easier for organizations to implement step-up authentication effectively. AuthX, with its advanced features, enables businesses to assess risk in real time and prompt additional verification steps only when necessary. This ensures that sensitive data is secured while minimizing troubles for users. Setting up contextual authentication, that adapts to users’ behavior, and manage industry regulations, so that the organizations can protect themselves from cyber threats.
If you want to improve the cybersecurity of your organization, now is the time to evaluate current authentication processes. Explore how AuthX’s adaptive authentication solutions can enhance your user experience and security posture.
Frequently Answered Questions (FAQs)
How is step-up authentication different from regular multi-factor authentication (MFA)?
Regular MFA requests users to verify their authentication by using a combination of methods. For example, the user would be required to use a password and a one-time passcode to access.
Whereas, step-up authentication requests additional verification when you are performing a more sensitive action that requires an extra method of security.
How does step-up authentication improve security?
Step-up authentication enhances security by requiring extra verification for high-risk actions, reducing unauthorized access and safeguarding sensitive information.
How can businesses implement step-up authentication?
Businesses can implement step-up authentication using identity management solutions, which offer flexible tools for integrating multi-factor authentication and contextual verification. Tools like AuthX allows organizations to define custom rules that trigger additional verification based on the action, location, or other contextual factors, ensuring that security adapts to the level of risk.
Can step-up authentication prevent fraud?
Step-up authentication significantly reduces fraud by adding extra verification for high-risk actions. Even if intruders obtain login credentials, they can’t execute critical tasks without passing additional checks.
What role does AuthX play in step-up authentication?
AuthX elevates step-up authentication with smarter, adaptive security that adjusts to user behavior, action risks, and compliance needs. By making authentication intuitive and minimally disruptive, AuthX ensures robust security while delivering a seamless user experience.