As businesses transition to a more digital and mobile workforce, traditional security methods are being stretched thin. With the global adaptive authentication market projected to grow at a 13.1% CAGR, reaching USD 85.5 billion by 2033, it’s clear that organizations are prioritizing smarter security solutions. Employees now work from various devices and locations, making it increasingly difficult to ensure secure access without impacting productivity. The result? There is a growing need for a solution that can balance robust security with seamless user experience. Adaptive Authentication rises to the challenge, offering a dynamic, context-aware approach that adjusts security measures in real-time.
For example, if employees access sensitive company data from a trusted device at their usual office location, the system might allow them to log in without additional steps. However, if the same employee tries to log in from an unfamiliar location or device, adaptive security will trigger additional security checks, such as multi-factor authentication. This helps protect sensitive data without compromising convenience, offering a smarter, more flexible way to stay secure.
What is Adaptive Authentication?
Simply put, Adaptive Authentication dynamically adjusts the level of security based on the user’s context and access request. Unlike traditional authentication methods like static passwords or fixed Multi-Factor Authentication (MFA), Adaptive MFA considers factors such as the user’s location, device, behavior, and even the time of access. The goal? To provide the highest security without interrupting the user experience.
We often hear from security leaders how challenging it is to balance robust security with user convenience. What is Adaptive MFA? It’s a solution designed to address this challenge by adding contextual intelligence to authentication processes. When users log in from their usual devices, their access is seamless. However, additional checks can be triggered when a login attempt is made from an unfamiliar location or device, enhancing security while keeping the process frictionless.
How Does Adaptive Authentication Work?
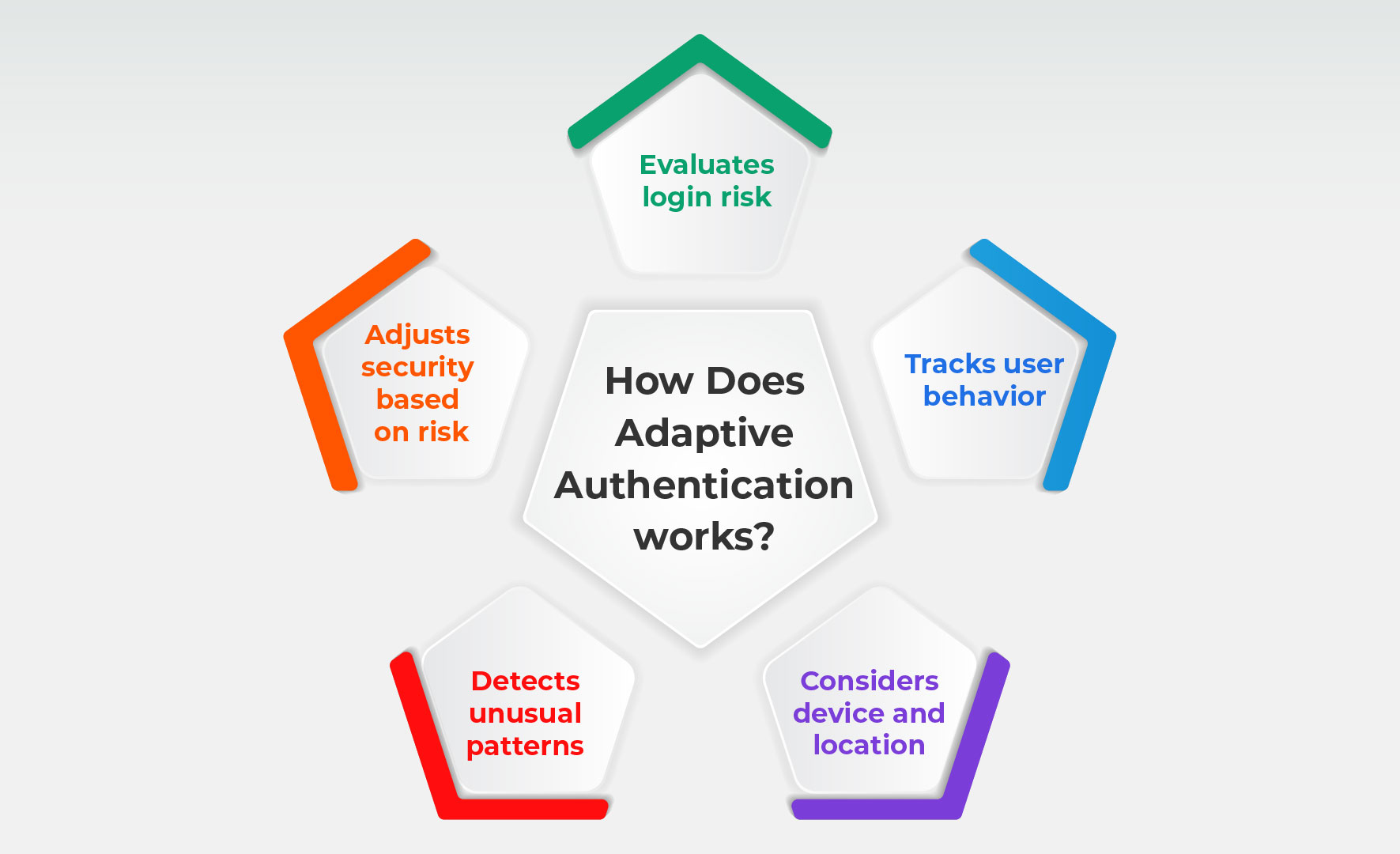
Adaptive Authentication employs a combination of behavioral analysis, risk-based decision-making, and machine learning. Here’s how it works:
- Risk-based Authentication: Adaptive security continuously assesses the level of risk associated with every login attempt. When it detects a higher risk, such as a login from an unfamiliar device or a suspicious location, it adjusts the level of verification required.
- User Profiles: Over time, systems create detailed profiles based on a user’s typical behaviors like their login times, frequent devices, and geographic locations. These profiles form the foundation of adaptive identity solutions, helping to distinguish between normal and abnormal behaviors effectively.
- Contextual Factors: Factors like device posture (is it secure?), location (is this an unusual place?), and time (is this out of the ordinary?) all come into play. This context helps the system determine how much verification is needed.
- Behavioral and Machine Learning: AI and machine learning allow systems to track user behavior patterns, learning what’s “normal” and what isn’t. If something seems off, the system can prompt additional authentication steps.
Businesses are frequently astounded by how well these technologies integrate. It’s like having a security guard who can modify their approach according to the circumstances.
Why is Adaptive Access Important?
One of the main reasons adaptive access is crucial is the growing adoption of flexible work environments. Remote, hybrid, and BYOD models demand more advanced security measures. Traditional approaches like static MFA just aren’t enough anymore. Adaptive authentication is an excellent fit with the zero-trust security concept, which states that we should always verify everything and trust nothing, including networks, users or devices.
What makes adaptive access most effective is its ability to stop fraud and unauthorized access. Adaptive access control is revolutionary in industries where sensitive data is involved, such as healthcare or banking. By continuously determining if access attempts are legitimate, it reduces risks like account takeovers and credential theft.
Let’s not forget the user experience. We hear from IT professionals that they often balance security with usability. Adaptive access security measures don’t disrupt users during low-risk activities, meaning it doesn’t add friction when it’s not needed.
Key Benefits of Adaptive Authentication
Here are the main benefits of adopting adaptive Authentication:
- Enhanced Security: Adaptive access control adds extra protection levels when it detects anomalies in real-time risk assessment. This makes it more difficult for hackers to go beyond it.
- Improved User Experience: The best part? For users, it reduces friction. When everything is regular, there is no extra hassle, but if something unusual happens, further verification measures are taken.
- Cost-Effectiveness: A system that guards against unauthorized access reduces the cost of fraud and data breaches. By stopping incidents before they happen, organizations can save millions of dollars.
- Flexibility and Scalability: Adaptive authentication can expand to accommodate the needs of small and large businesses alike.
Deployment Methods and Use Cases
Adaptive Authentication isn’t just theoretical—it has real-world applications. Here are some key use cases:
- Remote Access & Cloud Apps: Adaptive authentication ensures secure access to resources, including virtual desktop environments, as numerous employees use cloud-based apps or work remotely.
- BYOD Environments: Adaptive security can help reduce the risks related to personal devices in BYOD environments, where employees utilize them for work.
- High-Risk Operations: For sensitive actions, such as accessing critical data or performing financial transactions, adaptive access control ensures higher levels of verification are applied.
- Role-Based Access Control: It also works well when different user roles require different access levels. For example, an admin might need to go through more steps than a regular employee.
Adaptive Multi-factor Authentication vs Traditional Authentication
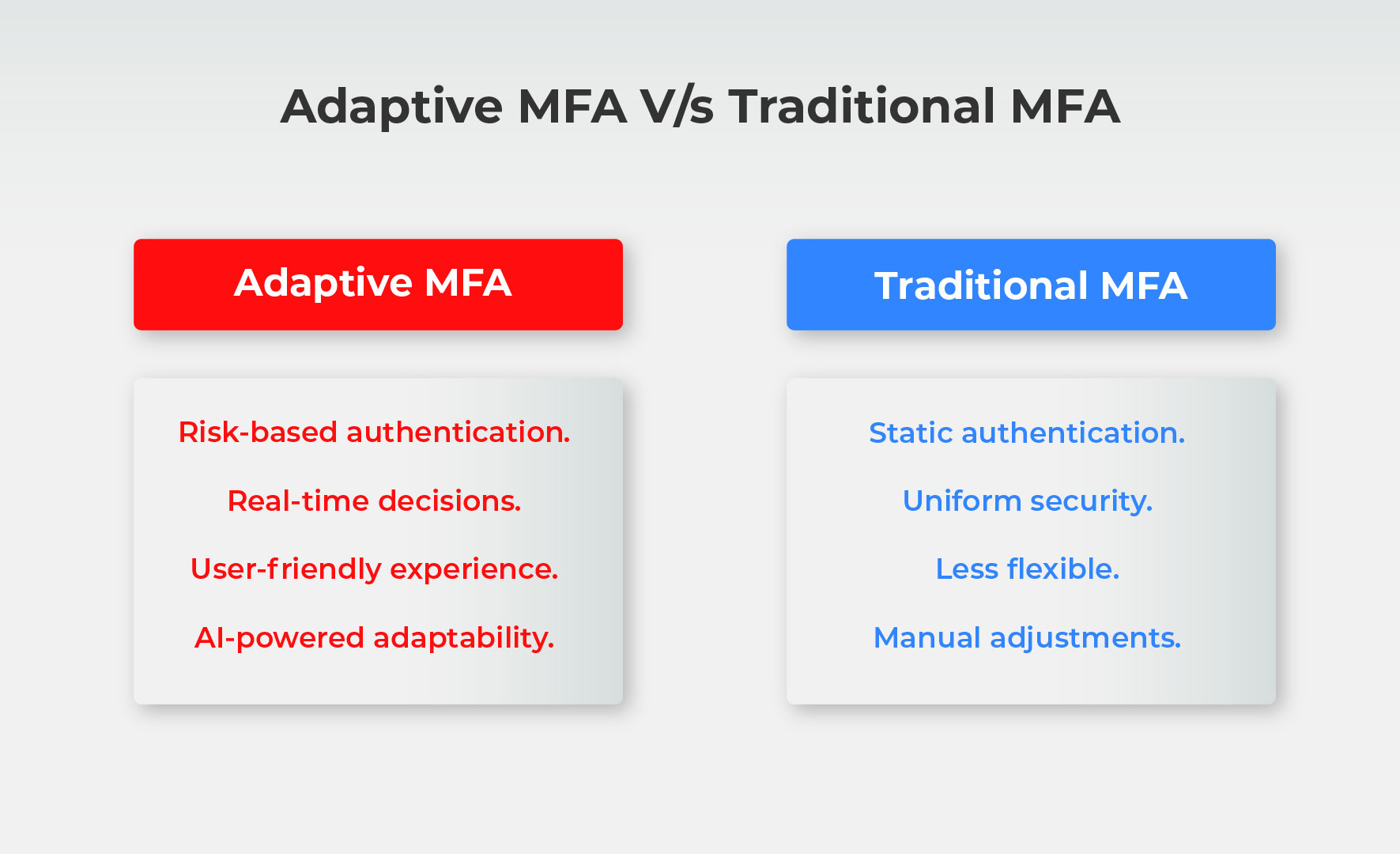
Traditional authentication methods like single passwords or static MFA have significant limitations. A password, while a basic form of protection, is often easy to bypass or steal. And even static MFA doesn’t adapt based on context—it’s the same process every time.
In contrast, adaptive MFA assesses risk in real time and adjusts the level of Authentication required. For example, in traditional MFA, you might always have to enter a code sent to your phone, but with adaptive Authentication, you may not need that step if the login is from a recognized device and location.
Challenges and Considerations
Adaptive authentication has its own set of challenges, just like any other system. IT teams frequently express anxiety about striking a balance between security and user convenience. Adaptive authentication is beneficial, but there could still be a trade-off between data security and user experience.
Another challenge is integration with legacy systems. Some older systems weren’t designed to handle such dynamic authentication methods, which can complicate deployment. But the good news is, many modern solutions now have workarounds that make it easier to integrate with existing infrastructures.
Finally, there’s the issue of continuous monitoring and policy updates. Security threats evolve constantly, so your policies need to be adaptive too. That means continuously assessing user behaviors and adjusting security measures accordingly.
Integrating Adaptive Authentication with Other Security Solutions
Adaptive Authentication doesn’t have to work alone. When combined with other security measures, it strengthens the entire security framework:
- Single Sign-On: Adaptive Authentication and SSO can complement each other to improve security and simplify access control. The two technologies work well together.
- Passwordless Authentication: By integrating adaptive authentication with passwordless methods like passkeys or biometrics, you can offer a safe, seamless experience that reduces the risk of credential theft.
- Zero Trust Framework: Adaptive authentication is an essential component of the Zero Trust framework, which ensures that all devices, users, and connections are regularly validated.
Examples of Adaptive Authentication across Industries
Adaptive authentication is being used successfully in various industries, including but not limited to:
- Healthcare: Adaptive authentication ensures that healthcare professionals can securely access patient data without slowing their workflow in the healthcare industry, where quick and secure access to EHRs is crucial.
- Financial Services: By limiting access for critical tasks to authorized individuals, adaptive authentication protects sensitive client information and valuable transactions in the financial sector.
- Retail & E-commerce: Adaptive authentication helps safeguard customer accounts and payment transactions, reducing fraud and boosting trust as online shopping gains traction.
Future Trends in Adaptive Authentication
The future of adaptive authentication and adaptive identity looks bright. AI and machine learning developments will only strengthen the system’s capacity to identify irregularities and anticipate risks before they occur. Furthermore, integrating with modern technologies like biometrics and blockchain could offer even more opportunities for secure and smooth user experiences.
Adaptive authentication will keep evolving as cybersecurity threats get more complex, making sure that companies stay one step ahead of cybercriminals.
Transform Cybersecurity with Adaptive Authentication
Adopting adaptive authentication is crucial, and this cannot be emphasized enough. Data protection is only one aspect of it; another is giving customers as well as employees a secure, easy-to-use experience. Having witnessed the development of authentication techniques, we can say with confidence that companies should take adaptive authentication into account if they want to remain competitive in the current digital environment.
If you want to improve the cybersecurity of your organization, now is the time to evaluate current authentication processes. Explore how AuthX’s adaptive authentication solutions can enhance your user experience and security posture.


