What is the NIS2 Directive?
Why is NIS2 Compliance Essential?
If you believe compliance is just another boring checkbox, think again! NIS2 compliance involves more than simply adhering to rules; it includes securing your network and information systems to ensure business continuity and maintain trust with customers and partners. Here’s why it is important:
- Strengthened Cybersecurity Posture: Ensures your business is resilient to threats like ransomware and phishing.
- Avoid Hefty Fines: Non-compliance penalties can amount to up to €10,000,000 or 2% of global annual revenue, whichever is greater.
- Standardized Practices Across the EU: Standardizes practices across the EU, reducing ambiguity for organizations operating in multiple countries.
- Trust & Reputation: Being compliant signals to customers and partners that your organization prioritizes security and data protection.
Who Needs to Comply with NIS2?
Under the NIS2 Directive, industries are categorized into two main groups: Essential Entities and Important Entities. These categories are designed to prioritize compliance and establish distinct security measures based on the criticality of the sector.
1. Essential Entities
These are the industries considered to have the most impact on the economy and society. Disruptions to their services can have serious economic and social consequences. Key sectors that fall under this category include:
- Energy: Power generation, transmission, and distribution.
- Transport: Including air, rail, and maritime transport.
- Banking: Financial institutions, including payment systems.
- Healthcare: Hospitals, clinics, and healthcare providers.
- Water Supply: Entities involved in drinking water distribution and sewage services.
- Digital Infrastructure: Providers of cloud services, data centers, and critical IT services.
2. Important Entities
These sectors, while crucial, are considered slightly less critical in comparison to essential entities but still require strong cybersecurity measures. Examples include:
- Digital Services: Online platforms, such as search engines, social media, and e-commerce sites.
- Food: Critical factors in food production, supply chains, and distribution.
- Public Administration: Governmental bodies and services.
Cybersecurity Measures Required by NIS2 (NIS2 Requirements)
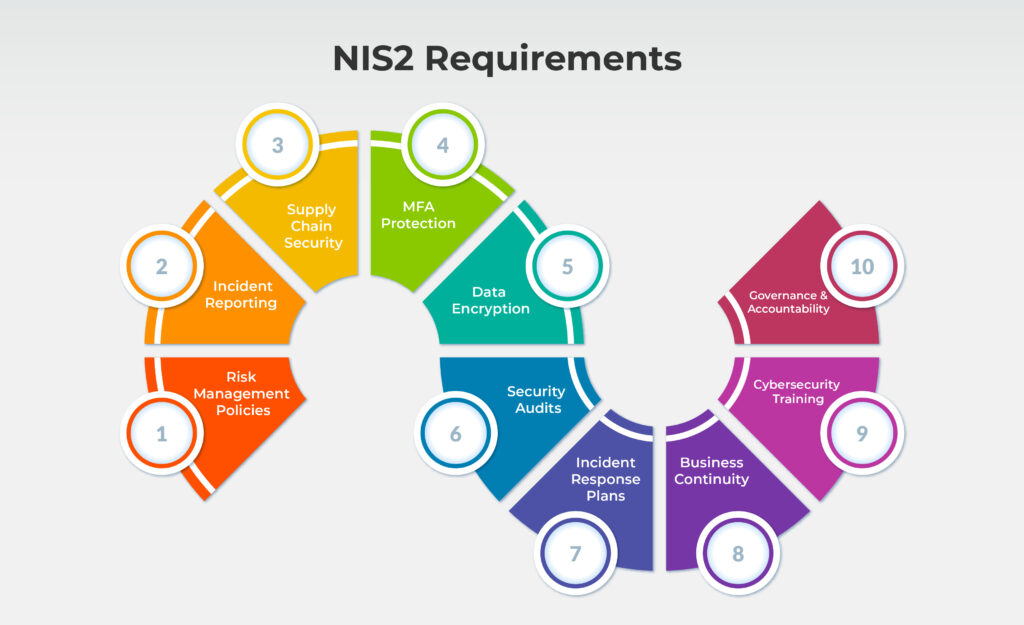
- Risk Management and Security Policies: Organizations must implement robust risk management practices and security policies that address network and information systems risks and ensure ongoing risk assessments.
- Incident Handling and Reporting: Entities are required to establish incident detection, response, and recovery processes. They must report significant cybersecurity incidents to national authorities within 24 hours of detection.
- Supply Chain Security: Organizations must assess and manage cybersecurity risks across their supply chain, ensuring that third-party providers comply with adequate cybersecurity measures.
- MFA Protection: Multi-factor authentication (MFA), continuous authentication, and encrypted communication solutions for access points ensure multi-layered security, safeguarding your network from unauthorized access and cyber threats.
- Encryption and Data Protection: Entities should apply strong encryption to protect data, both in transit and at rest, ensuring that sensitive information is securely handled.
- Regular Security Audits and Testing: Continuous security testing, audits, and vulnerability assessments must be performed to identify and fix weaknesses in network systems, including penetration testing and risk assessments.
- Incident Response Plans: Clear, well-documented incident response plans must be in place, including procedures for recovery, communication, and restoring critical services following a cyberattack.
- Business Continuity and Resilience: Businesses must implement business continuity measures and resilience strategies, ensuring critical services can be maintained or quickly restored after a disruption.
- Cybersecurity Training and Awareness: Organizations must train employees regularly on cybersecurity threats, best practices, and the specific procedures to follow in the event of a cyber incident.
- Cybersecurity Governance and Accountability: The directive requires a clear governance framework with designated personnel responsible for cybersecurity, along with a commitment to continuous improvement in security practices.
These measures aim to enhance the overall security posture of critical sectors and their digital infrastructures in the EU, ensuring high protection against cyber threats and incidents.
How AuthX Helps You Achieve NIS2 Compliance?
- Multi-Factor Authentication (MFA): AuthX enables passwordless authentication through methods like Passkeys, Badge Tap & Go, biometrics, and mobile push notifications—helping organizations comply with NIS2’s MFA requirements while reducing reliance on traditional passwords.
- Zero Trust Security: AuthX supports zero trust architecture, ensuring that all users and devices are authenticated and continuously validated, effectively reducing risks and enhancing security policies.
- Encrypted Access Control: AuthX’s zero trust policy protects data by encrypting it both in transit and at rest. Our solutions ensure secure communication and data protection across devices, securing access to critical systems without compromising performance.
- Continuous Monitoring: With real-time access logs and detailed reporting, AuthX enables continuous monitoring and supports regular security testing to detect vulnerabilities, helping businesses stay ahead of emerging threats.
- Role-Based Governance: AuthX facilitates robust governance with comprehensive role-based access management. Designated personnel can manage security roles and track user activity, promoting transparency and accountability in line with compliance needs.
How Does NIS2 Impact Identity Security?
Strong identity management and access control are key foundations of NIS2. Organizations must ensure that only authorized users have access to their systems and data, which is why Multi-Factor Authentication (MFA) is so important. Simple passwords are no longer enough, as they vulnerabilities that attackers can simply exploit. By layering security with factors such as passkeys, badge tap access, biometrics, OTPs, or mobile push notifications, MFA helps reduce risks, aligning your organization with NIS2 compliance.
Enhanced MFA for NIS2 Compliance with AuthX
To comply with the NIS2 Directive, organizations need more than basic MFA tools— they need flexible, modern authentication solutions.
At AuthX, we offer passwordless authentication methods to enhance security without compromising the user experience:
Passkeys – Secure and frictionless login using cryptographic keys.
Badge Tap & Go – A simple card tap is a fast and convenient way to access systems.
Biometric Authentication – Leverage face and fingerprint scans for top-tier security.
Mobile Push Notifications – Authenticate with a quick mobile prompt.
Mobile Face Verify – Use smartphone facial recognition for seamless logins.
OTP (One-Time Passwords) – Add a second layer of security with time-sensitive codes.
How to Get NIS2 Compliant: A Step-by-Step Guide
Step 1: Assess Your Cybersecurity Gaps
Identify weaknesses in your current security posture. Conduct a gap analysis against NIS2 requirements, focusing on access management and incident response.
Step 2: Implement a Strong IAM Framework
Deploy a robust IAM platform with MFA to secure access points. With AuthX, you can combine SSO, MFA, and passwordless authentication to balance security and convenience.
Step 3: Train Your Workforce
Ensure employees are familiar with cybersecurity best practices and authentication flows. Our Passkeys, Badge Tap & Go, Biometrics, and Mobile Push solutions allow users to adapt quickly to secure workflows without friction.
Step 4: Monitor, Report, and Optimize
Implement real-time monitoring tools to track logins and potential breaches. Our IAM platform provides instant insights to ensure accurate and timely regulatory reporting.
NIS2 Compliance Starts with Secure Identity Management
Transform Your Cybersecurity and Achieve NIS2 Compliance with AuthX
The NIS2 Directive is not a challenge; it’s an opportunity for you to reconsider your approach to cybersecurity. See compliance as an opportunity to improve your security posture and optimize your processes rather than as a barrier. With AuthX’s Zero Trust framework, seamless SSO, and passwordless MFA, you can use these legal requirements to your benefit.
Are you ready to meet the NIS2 requirements? Success can be achieved with the correct IAM approach, and AuthX is here to support you at every stage. Connect with our experts now to learn more.
FAQs
What are the requirements for NIS2?
What is the NIS regulation 2?
What is new in NIS2?
Which sectors does NIS2 apply to?
It includes digital providers including cloud services, data centers, and online platforms as well as essential sectors like energy, healthcare, transportation, and financial services.


