What is Multi-factor Authentication (MFA)? Ultimate Guide to MFA

With the rise in cyber-attacks in recent years, businesses must prioritize cybersecurity initiatives. As technology evolves, so do the methods used by cybercriminals to breach critical information. In this unstable environment, the need for stronger authentication processes has never been greater. That’s where Multi-factor Authentication (MFA) comes in—a cybersecurity guardian that acts as a solid barrier against unauthorized access. Multi-factor authentication is a security practice that requires multiple forms of identity verification before providing access to an account or system. This blog will explore the significance and benefits of MFA and why is multi factor authentication important for an organization’s cybersecurity strategy.
How does Multi-factor Authentication work?
Multi-factor Authentication is a security practice that requires users to provide multiple forms of identification before granting access to a system, application, or network. Traditionally, the most common form of authentication was a username and password. However, as cyber threats grew, this single layer of security became increasingly vulnerable. MFA, also known as two-factor authentication (2FA) or three-factor authentication (3FA), enhances the authentication process by adding additional layers of verification, categorized into three factors: something you know, something you have, and something you are.
Something You Know:
This involves knowledge factors like traditional username and password combination, representing knowledge-based authentication.
Something You Have:
This involves a possession factor, such as a smart card, security key, security token, or mobile phone.
Something You Are:
This factor incorporates biometric authentication, utilizing unique physical or behavioral traits like fingerprints, palm scans, or facial recognition.
Multi-factor Authentication vs. Two-factor Authentication (2FA vs. MFA)
Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) are related concepts but differ in the number of authentication factors used. While 2FA specifically requires two factors (typically something you know and something you have), MFA can involve a more diverse set of factors, adding an extra layer of security by incorporating additional elements, such as biometrics.
Parameters | Two-Factor Authentication (2FA) | Multi-Factor Authentication (MFA) |
Definition | Involves the use of two authentication factors | Encompasses the use of more than two authentication factors |
Typical Factors | Knowledge-Based Authentication (e.g., password or PIN) and Possession-Based Authentication (e.g., physical device) | Knowledge-Based Authentication (e.g., password or PIN), Possession-Based Authentication (e.g., physical device), and Biometric Authentication (e.g., fingerprints, facial recognition) |
Verify the Resources | 2 ways to verify identity resources | More than 2 ways to verify identity resources |
Actions in Authentication | 2 actions before authentication, quick access. | Multiple actions to confirm authentication, complex process. |
Security Level | High | Very high |
Security Breaches/Threats | Vulnerable to attacks if one factor is compromised | Higher resilience as multiple factors of authentication built stronger protection |
Securing Access with AuthX’s Multi-factor Authentication Methods
AuthX employs advanced security measures to safeguard access, including various types of multi-factor authentications to offer substantial defense against unauthorized access.
1. RFID Tap & Go
While AuthX’s RFID Tap & Go Technology simplifies user access with a simple tap, augmenting this convenience with heightened security measures is crucial. Leveraging RFID for swift and secure identity verification, this passwordless authentication method ensures user convenience without compromising stringent security standards. Additionally, integrating a more secure second factor, such as mobile facial recognition, enhances authentication robustness, further strengthening the security framework.
2. Biometric Authentication
As multi-factor authentication technology progresses, it becomes increasingly user-friendly with increased utilization of passive methods such as biometrics. AuthX employs advanced biometric authentication, utilizing fingerprint scanning and facial recognition, to ensure a secure and convenient user experience. Biometrics strengthens security by uniquely identifying individuals based on physiological characteristics. This improves the authentication system while simultaneously providing high accuracy.
3. Mobile Authentication
AuthX offers Mobile Authentication, employing innovative methods such as Authentication via Mobile Push Notification, Remote Unlock, Face-Verify, and One-Time Passcodes (OTP). Users seamlessly receive real-time authentication requests on their AuthX authenticator app, introducing a dynamic layer of security. This guarantees a seamless and user-friendly experience using mobile devices, providing convenience and robust protection for users.
Adaptive Multi-factor Authentication
Adaptive Multi-factor Authentication represents a transformative approach to bolstering security. This intelligent system customizes how you prove who you are by considering your typical behavior, location, device usage, and login times. It employs anti-fraud regulations to build a predetermined response to the authentication attempt. It dynamically adjusts to ensure it’s you, making security even more potent.
1. Dynamic Risk Assessment
Adaptive MFA leverages continuous risk assessment, including implementing risk-based authentication, to evaluate the context of each access attempt. If a user’s behavior deviates from the norm or the access request originates from an unfamiliar location, the system may prompt additional verification, ensuring a proactive response to potential threats. To enhance protection, always use MFA in response to heightened risk scenarios.
2. User Behavior Analysis
Adaptive MFA distinguishes between legitimate users and potential threats by analyzing behavior patterns. For example, if a user typically logs in from a specific device and location, a deviation from this pattern may trigger intensified authentication requirements.
3. Frictionless Authentication
One of the main advantages of Adaptive MFA is its ability to balance security and user experience. When the system notices low-risk instances, it can automate the authentication procedure, reducing disruptions for authorized users while remaining attentive against potential threats. This adaptability is particularly evident with the addition of passwordless MFA, which provides users with a convenient and robust authentication experience.
What are the Benefits of MFA?
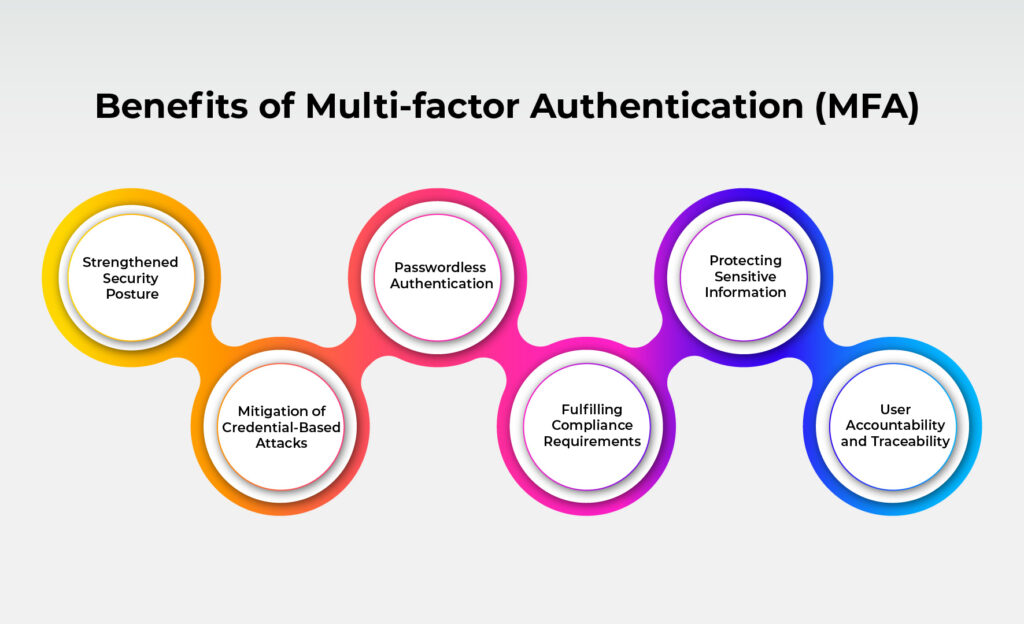
The benefits of MFA (Multi-Factor Authentication) significantly improve digital security by adding an extra layer of protection through multiple verification methods.
1. Strengthened Security Posture
MFA strengthens the security stance of organizations by using multiple barriers to prevent unauthorized access. Even if one layer is compromised, additional authentication factors act as a strong obstacle, making it harder for attackers to navigate complex defenses.
2. Mitigation of Credential-based attacks
The increasing number of credential-based attacks, including phishing and brute force attacks, emphasizes the importance of MFA. With the inclusion of multi-factor authentication, cyber attackers’ compromise of login credentials becomes an incomplete success, as they have to deal with additional challenges beyond the initial breach.
3. Passwordless Authentication Enabled
MFA enables passwordless authentication, allowing users to provide multiple forms of authentication instead of a password. This enhances security and user experience by reducing reliance on traditional passwords and introducing innovative authentication methods.
4. Fulfilling Compliance Requirements
In an era defined by stringent data regulations and compliance demands, MFA is essential for organizations striving to adhere to guidelines such as GDPR, HIPAA, and PCI DSS. MFA implementation aligns with the regulatory context, exhibiting a commitment to robust cybersecurity techniques.
5. Protecting Sensitive Information
The stakes are exceptionally high for organizations dealing with sensitive information, be it intellectual property, patient data, customer data, or financial records. MFA acts as a digital guardian, ensuring only authorized employees with legitimate access credentials can navigate the digital assets.
6. User Accountability and Traceability
MFA adds a layer of accountability by connecting user identities to several types of authentications. This increases user accountability and allows for traceability in the event of a security incident, facilitating forensic investigations and incident response operations.
Implementing Multi-factor Authentication Effectively
Organizations must take a strategic approach to MFA deployment to optimize its potential:
1. User Education
It is essential to educate users about the importance of MFA and provide clear instructions on its usage. A well-informed user base will likely embrace and adhere to the additional authentication steps.
2. Integration with Identity and Access Management (IAM)
Smooth integration of MFA with IAM systems ensures a unified approach to user authentication and access control. This constructive collaboration enhances overall security while simplifying administrative tasks.
3. Adaptive Authentication
Implementing adaptive authentication, wherein the level of authentication is dynamically adjusted based on contextual factors such as user location, device used, and time of access, further enhances the efficacy of MFA.
4. Continuous Monitoring and Evaluation
Cyber threats are dynamic, requiring continuous monitoring and evaluation of MFA systems. Regular audits, vulnerability assessments, and updates to authentication protocols are crucial in maintaining the integrity of the security framework.
Conclusion
Organizations cannot afford insufficiency in their cybersecurity strategy in today’s digital landscape, where information is extremely valuable and cyber threats offer considerable risks. MFA is a powerful defense, offering a multi-layered protection mechanism in addition to standard authentication techniques. Its deployment is a strategic requirement for enterprises looking to protect their digital assets, maintain regulatory compliance, and strengthen their defenses against the never-ending wave of cyber threats with additional security. With its passwordless and multi-factor authentication solutions, AuthX MFA is a dependable partner in enhancing cybersecurity. Explore AuthX’s innovative MFA solutions and set up multi-factor authentication to strengthen your organization’s defenses - connect with us to know more.