Secure Access Control Trends for 2024

2023 was a stark wake-up call for cybersecurity. Data breaches, once a distant worry, became a chilling reality, exposing the vulnerabilities of traditional security approaches. Siloed data, static defenses, and weak authentication methods proved insufficient against increasingly sophisticated cyberattacks. This is where access control emerges as the modern guardian of your digital realm.
This solutions are the foundation of a secure infrastructure, as unauthorized access is often the initial point of security breaches. In this blog, we will explore the upcoming trends of 2024 in access control, revealing their potential to strengthen your digital assets and shield your organization from emerging risks.
Access Control Future Trends
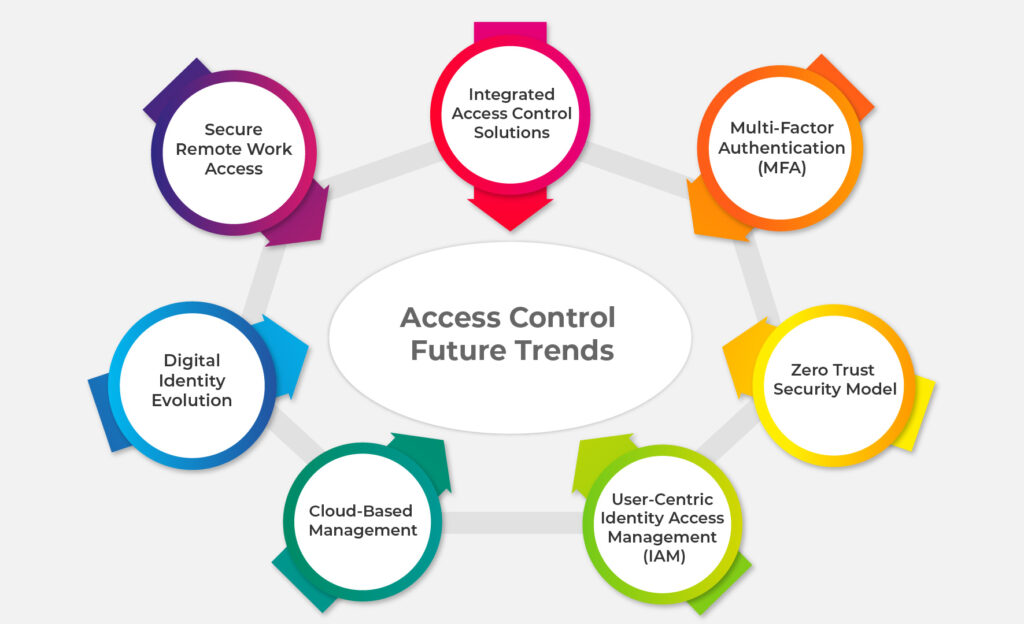
Traditional security measures are no longer enough. To truly safeguard your digital assets, it’s crucial to embrace the innovative trends shaping the future of access control:
1. Seamless Access Control Systems Integration
The future of Secure access control lies in smooth integration with other security measures. Organizations are turning to unified solutions encompassing access control, mobile device management (MDM), video surveillance, and even AI-powered security intelligence systems. This extensive approach boosts both security and management efficiency.
2.The Rise of Multi-factor Authentication (MFA)
Multifactor authentication (MFA) is no longer just an option; it has become a necessity for enhanced security. MFA will be pivotal, as it combines multiple forms of verification, such as something you know (password), something you have (smartphone or security token), and something you are (biometric), significantly enhancing security. Expect MFA to become more user-friendly and widely adopted.
3.Zero Trust Security Model
The Zero Trust Security model is gaining popularity as organizations recognize the limitations of perimeter-based security. In coming years, we anticipate a surge in the adoption of Zero Trust principles, which require continuous verification of users and devices regardless of location or network.
4.User-Centric Identity Access Management (IAM)
IAM (Identity and Access Management) systems are evolving to be more user-centric, providing an effortless and personalized experience. Users can expect more streamlined and secure access to resources customized to their needs, while organizations benefit from enhanced security and ease of management.
5.Cloud-Based Management
Cloud-based management is an excellent trend in access control. It empowers organizations to remotely manage access, providing agility, scalability, and flexibility. This shift enables rapid upgrades, reduces physical infrastructure constraints, and streamlines security management in the digital age.
6.Digital Identity Evolution
The concept of digital identity is transforming. Traditional username-password combinations are no longer robust enough to protect sensitive data. It is now expected to see the widespread adoption of passwordless authentication as a secure means of access. These methods offer an enhanced level of security as they are challenging to duplicate or forge.
7.Remote Work and Secure Access
With the rise of remote work, secure access from various locations and devices is critical. Access control systems adapt to this trend, enabling employees to work securely from anywhere without compromising the organization’s data.
Access Solutions Offered by AuthX:
Navigating the evolving landscape of access control can be daunting. AuthX is your trusted partner in this journey. Our comprehensive solutions address every aspect of your security needs:
1. Identity and Access Management (IAM)
AuthX excels in Identity and Access Management (IAM), providing a comprehensive solution that streamlines user authentication, authorization, and management. The centralized platform ensures efficient control over access rights, incorporating features like multi-factor authentication and simplified user provisioning. The intuitive interface balances between user convenience and stringent security measures, enhancing overall data protection.
2.RFID Tap & Go
AuthX transforms access control with a frictionless solution: RFID Tap & Go. This technology simplifies access through a swift tap, reducing reliance on passwords. Integrating advanced RFID technology, AuthX ensures secure and smooth access, catering to the requirements of modern and dynamic work environments. The RFID Tap & Go system enhances workplace efficiency by providing a secure, smart, and agile access system.
3.Remote Workstation Management
AuthX’s Remote Workstation Managementet not only facilitates secure remote system access for efficient employee workflows but also enhances managing control with features like remote lock, unlock, shut down, and log off. This comprehensive solution ensures that remote workstations adhere to stringent security policies, minimizing the risk of data breaches and unauthorized system access.
It can remotely lock or log off workstations in response to security concerns and has the flexibility to shut down or unlock workstations as needed.
4.Privileged Access Management (PAM)
IAM (Identity and Access AuthX’s Privileged Access Management (PAM) acts as a guardian of critical systems and data. Through granular control and monitoring, PAM ensures that only authorized individuals access sensitive information. AuthX PAM provides a robust framework for managing and securing privileged accounts, mitigating the risk of insider threats.
Advanced authentication measures and session monitoring are employed to detect and address potential security breaches. With PAM, organizations can protect their digital assets, meeting compliance requirements and bolstering overall cybersecurity posture.
Protect Your Digital Resources with Access Control
Effective access control is more than just keeping unauthorized individuals out; it’s about granting access to the right people at the right time. Here’s why access control is crucial for protecting your digital resources:
- Preventing Unauthorized Access: Access control systems are the first defense against unauthorized access attempts. You can significantly reduce the risk of breaches by implementing robust authentication and authorization techniques.
- Data Protection: This system ensures that sensitive data is only accessible to those who require it. Fine-grained access controls enable you to define who can view, edit, or delete specific data, adding an extra layer of security. Access control also helps you comply with regulations by ensuring that only authorized personnel can access and modify sensitive data.
- User Accountability: Access control systems maintain audit logs, which can help detect and track suspicious activities. This accountability can prevent insider threats and facilitate post-incident investigations.
- Scalability: As your organization grows, access control systems can scale with you. You can easily add or remove users, adjust permissions, and expand your security infrastructure.
- Cost Efficiency: While this systems require an initial investment, they can save you significant costs in the long run by reducing the risk of data breaches, which may result in costly penalties, legal fees, and reputation damage for your brand.
Act Now with AuthX
As access control technology evolves in response to the dynamic security landscape, it’s crucial to embrace these advancements to safeguard your organization’s digital assets effectively. Consider making AuthX your access control companion. AuthX effortlessly integrates with the latest technologies and security trends, propelling your access control to new heights and keeping you ahead of the curve.
With AuthX, you can fortify your organization’s defenses, protect sensitive data, and ensure that only authorized individuals access your digital domain. Don’t procrastinate in the face of future security challenges; act today with AuthX and secure your organization’s future.